KSS-CLI is a powerful and secure Command Line Interface (CLI) tool designed to help developers manage and store sensitive information, such as passwords, API keys, and other secrets, in a safe and encrypted manner. With a strong focus on security and ease of use, KSS-CLI utilizes a Secrets Manager approach, allowing users to securely store their secrets on their local devices and access them through the CLI.
macOSNodeJS
Using npm:
npm install -g kss-cliUsing yarn:
yarn global add kss-cliEncryption Key Management: When you run any command for the first time, KSS-CLI will attempt to retrieve the encryption key from the system's keychain. If the key is not found, KSS-CLI will generate a cryptographically secure encryption key and store it in the keychain. This ensures that your secrets remain secure, and KSS-CLI can access the key without further user intervention.
Passwords/Secrets Management: KSS-CLI securely stores passwords and secrets in an encrypted form in system's keychain also. All encryption and decryption operations are performed using the encryption key, ensuring your sensitive information is protected.
Keychain: Read more about keychain.
-
Add (
add) Command: Usekss-cli addto add new secrets. -
Remove (
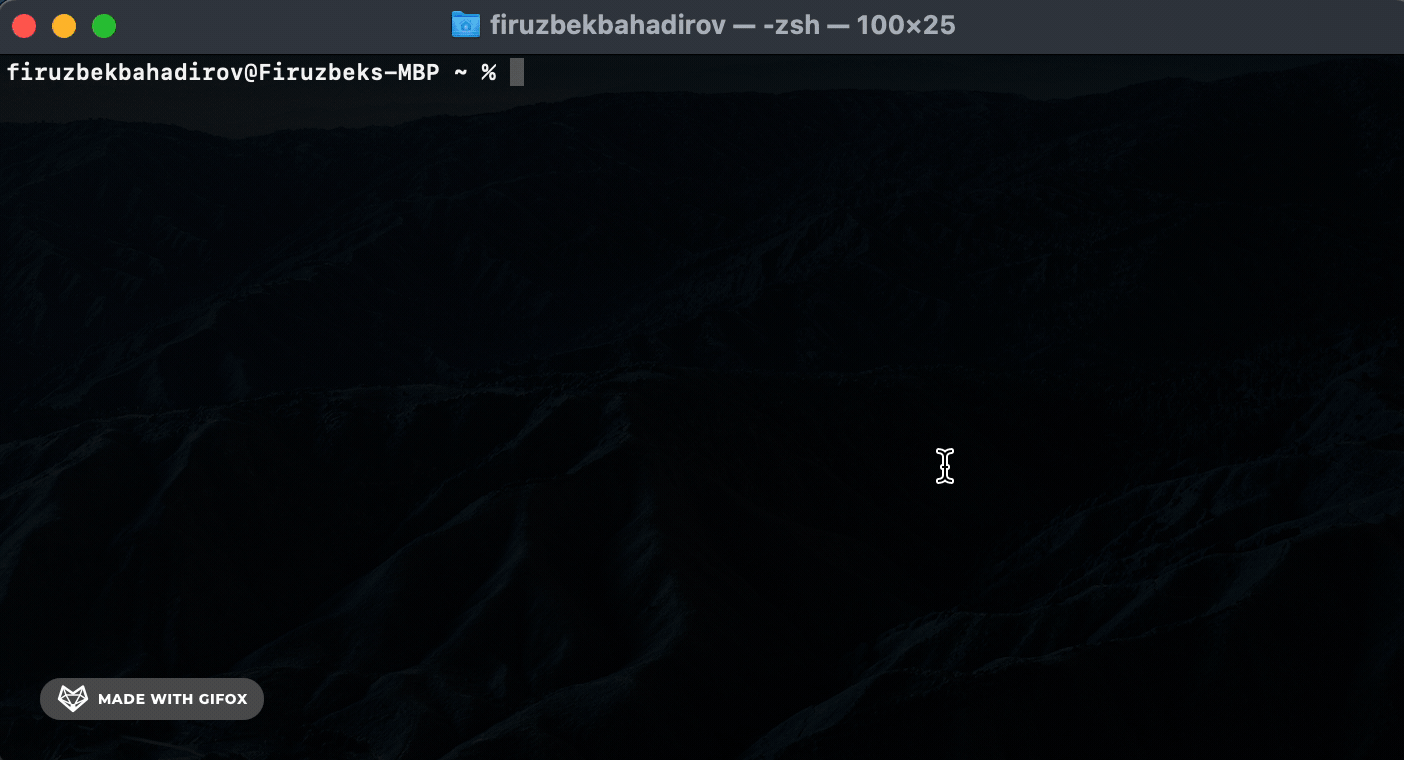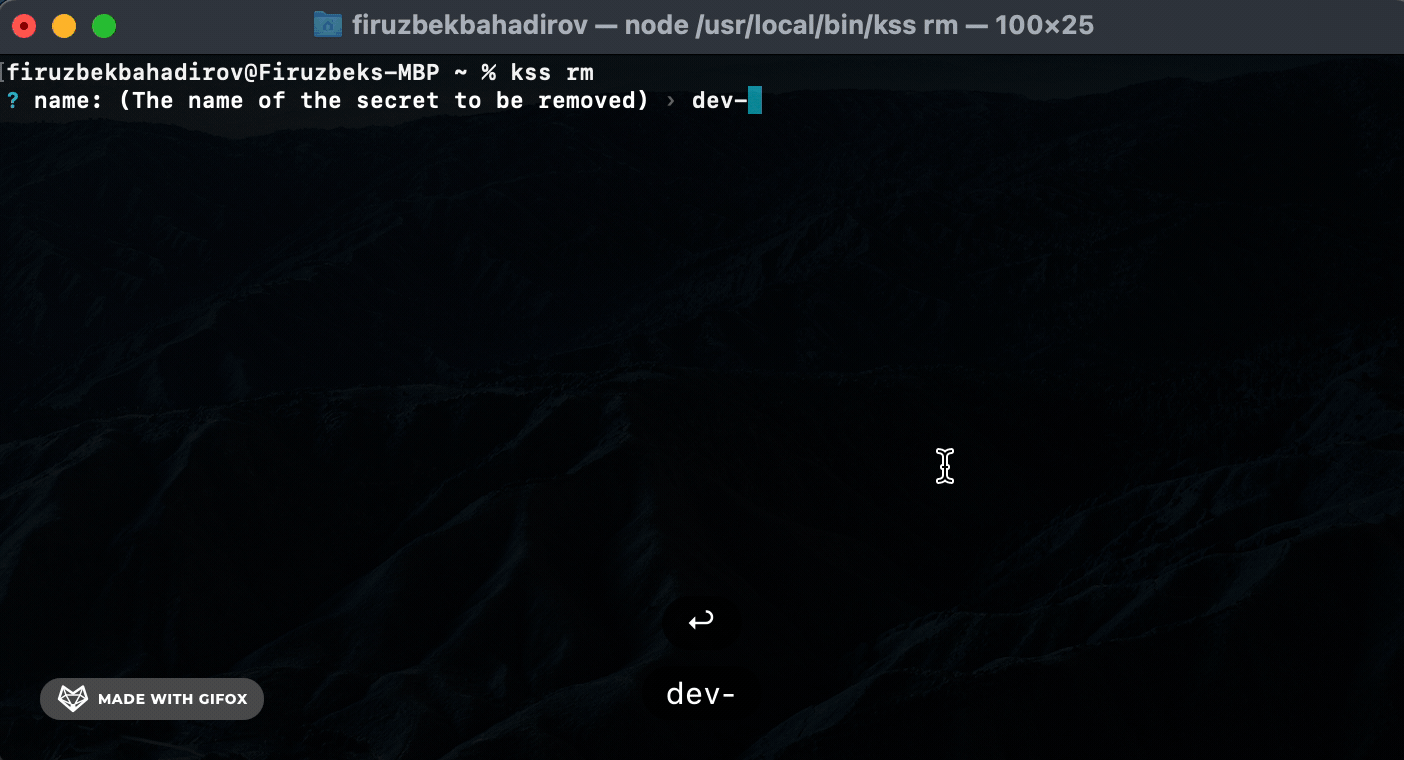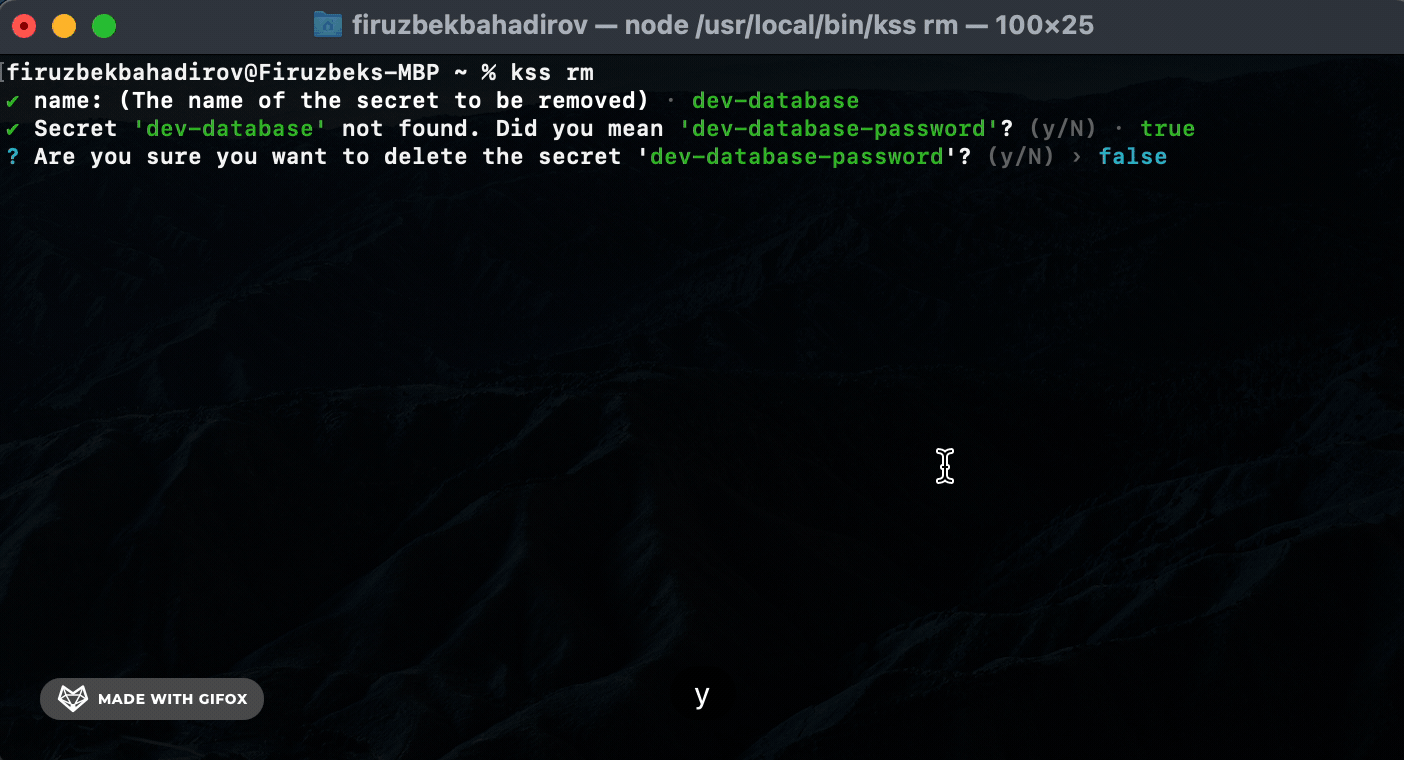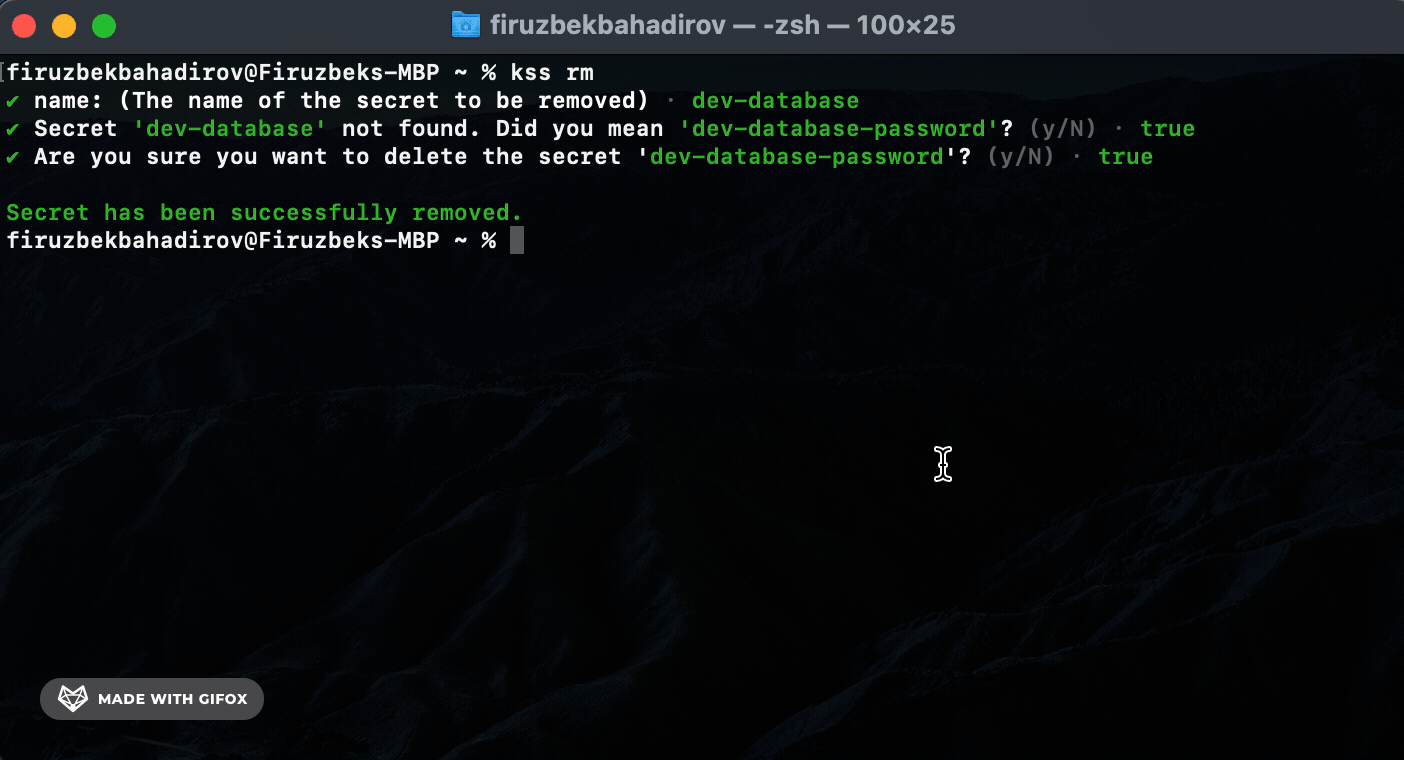
rm) Command: Usekss-cli rmto remove specific secrets. KSS-CLI will perform a search based on the providedsecret-nameand prompt for authorization before removing the secret. -
Copy (
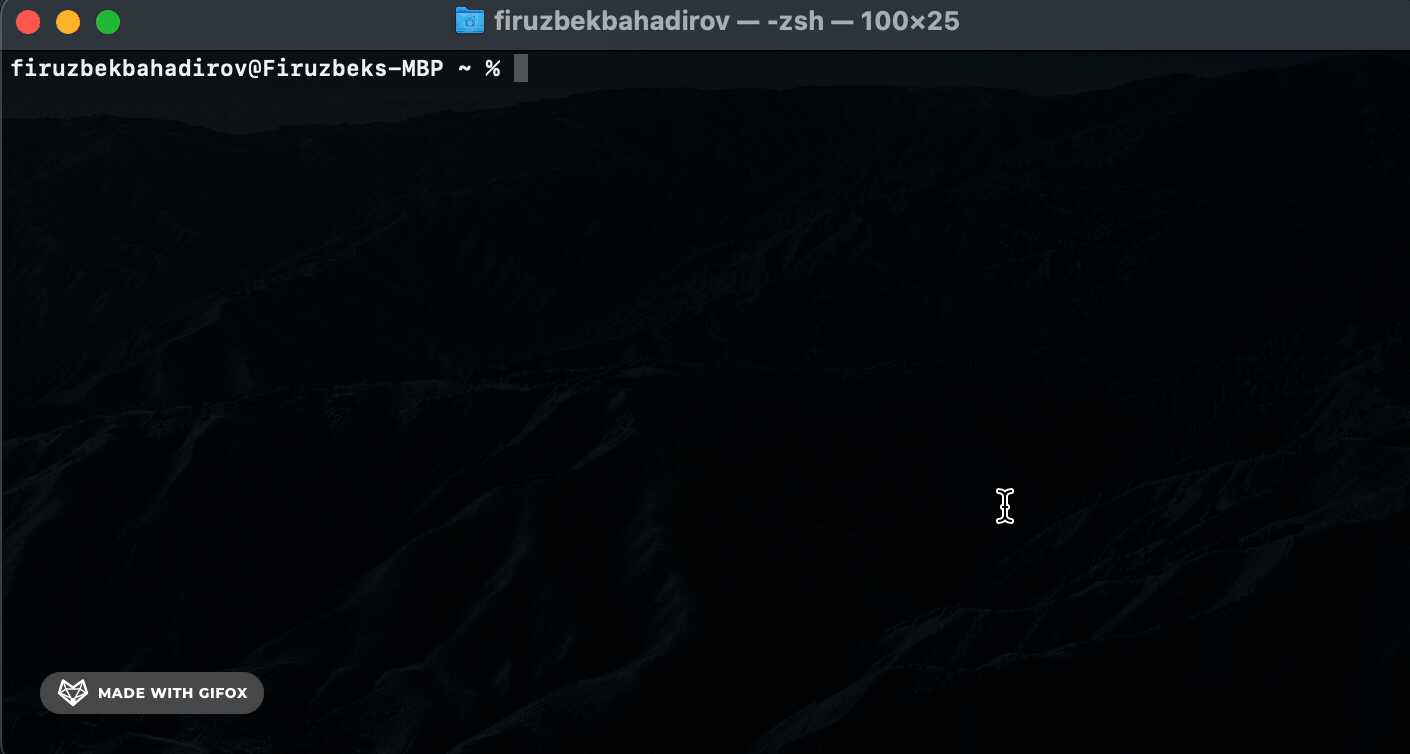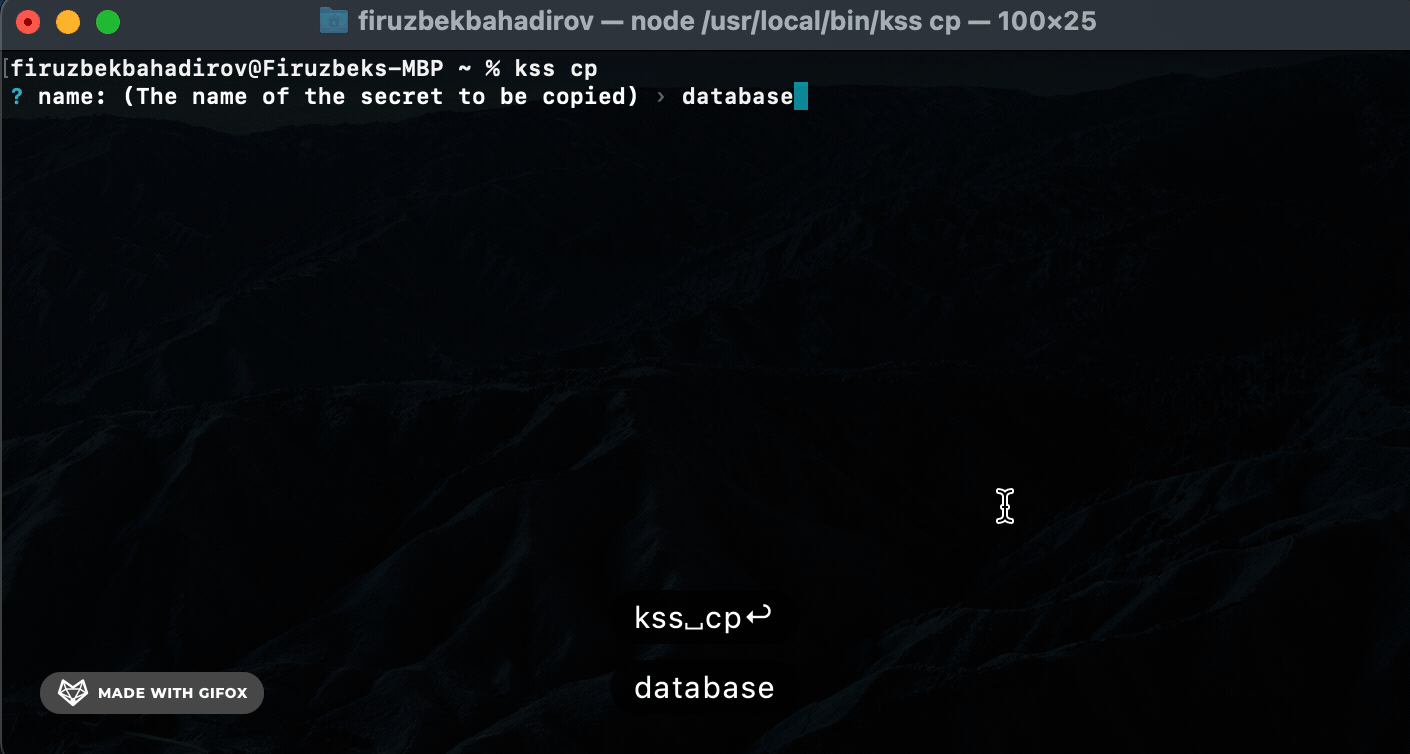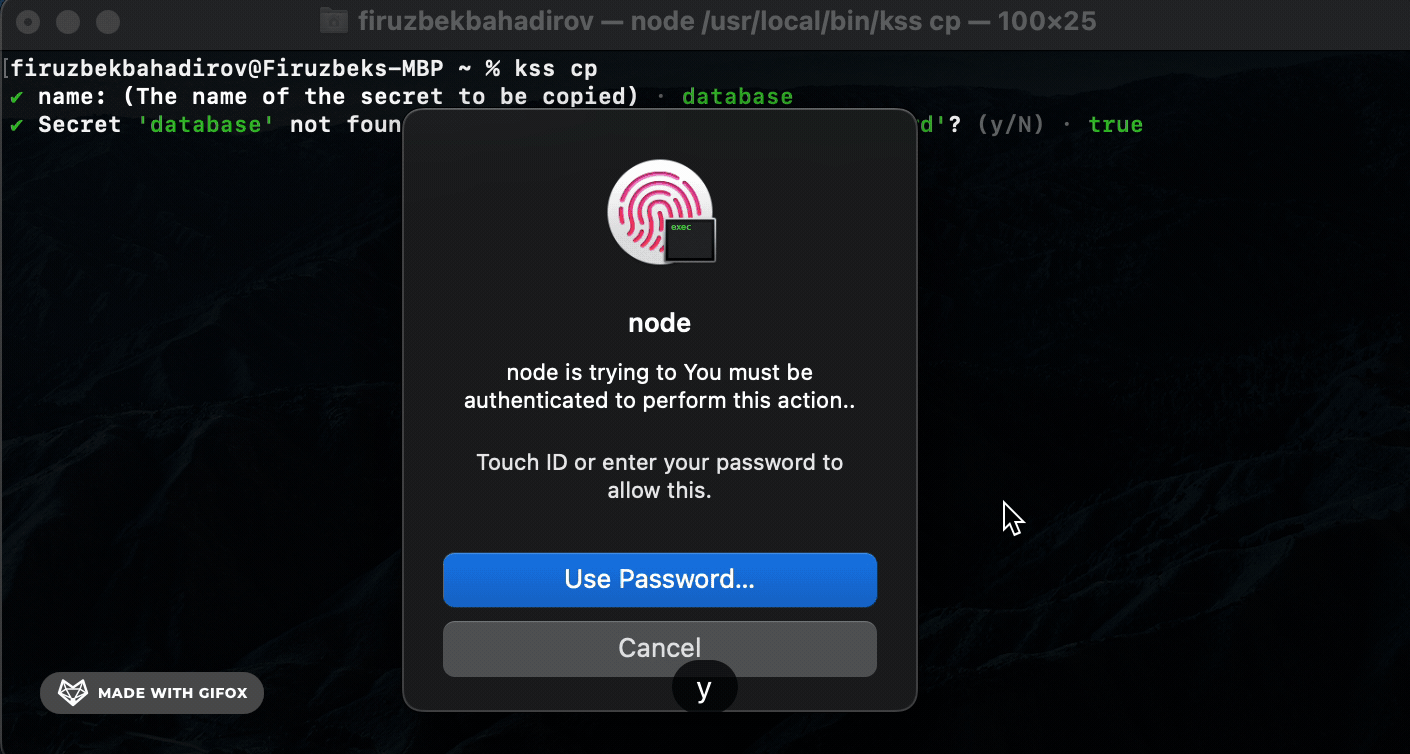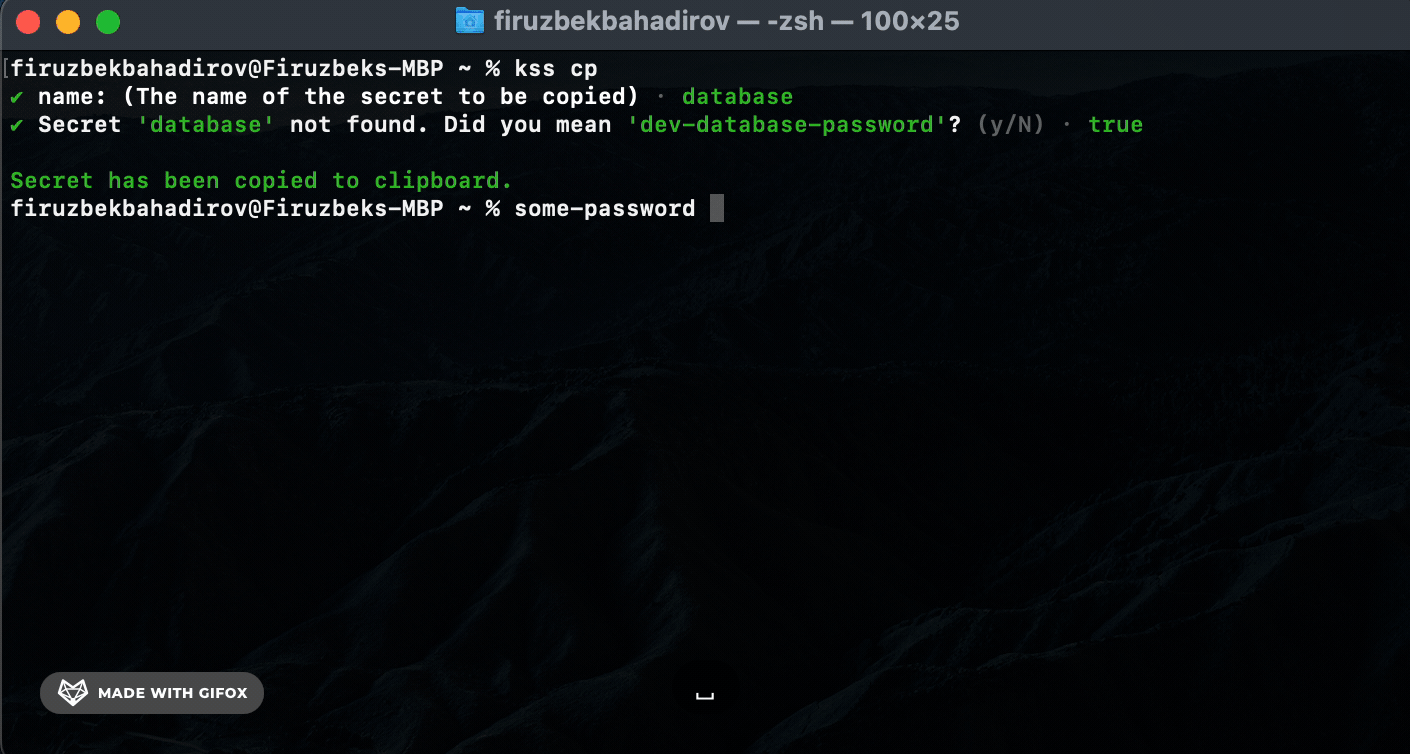
cp) Command: Usekss-cli cpto copy specific secrets to the clipboard. KSS-CLI will perform a full-text search based on the providedsecret-nameand prompt for authorization before copying the secret. -
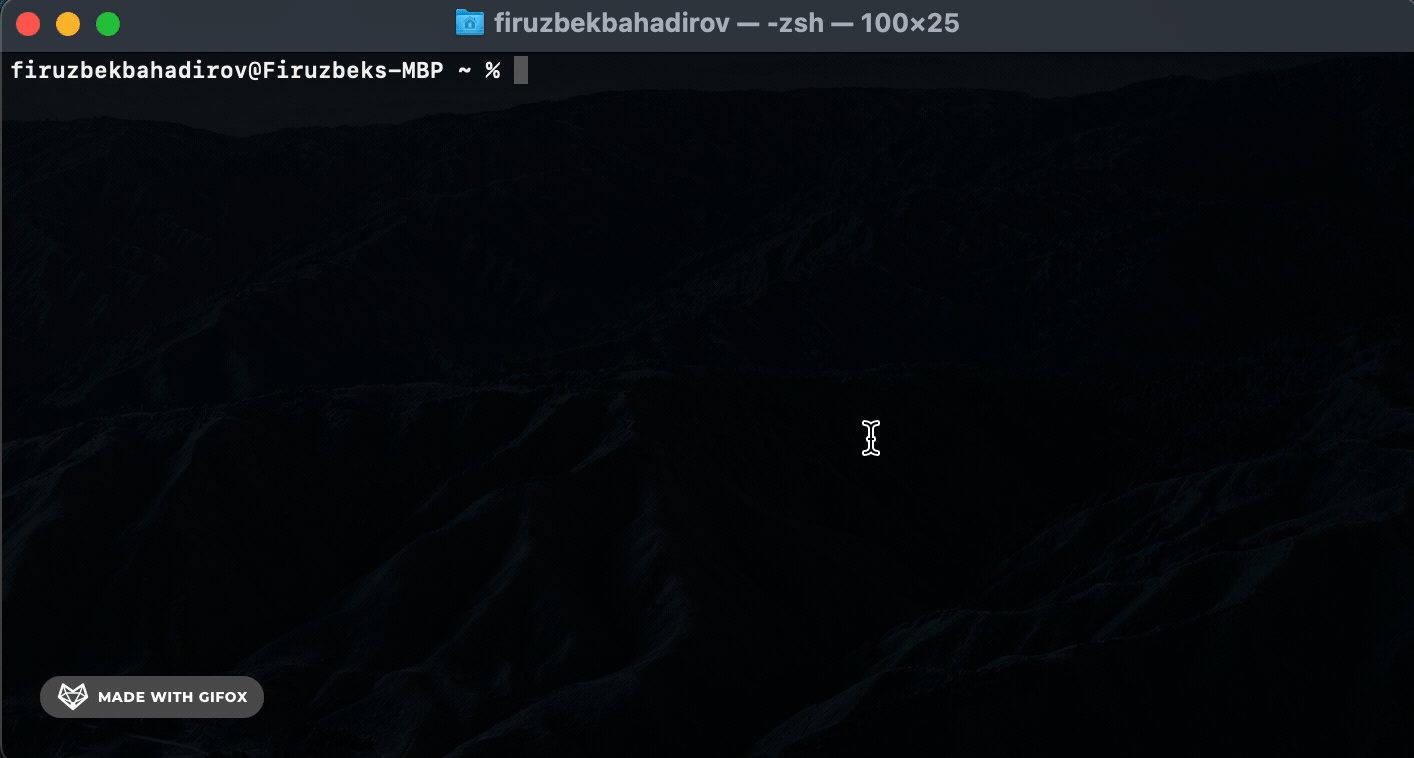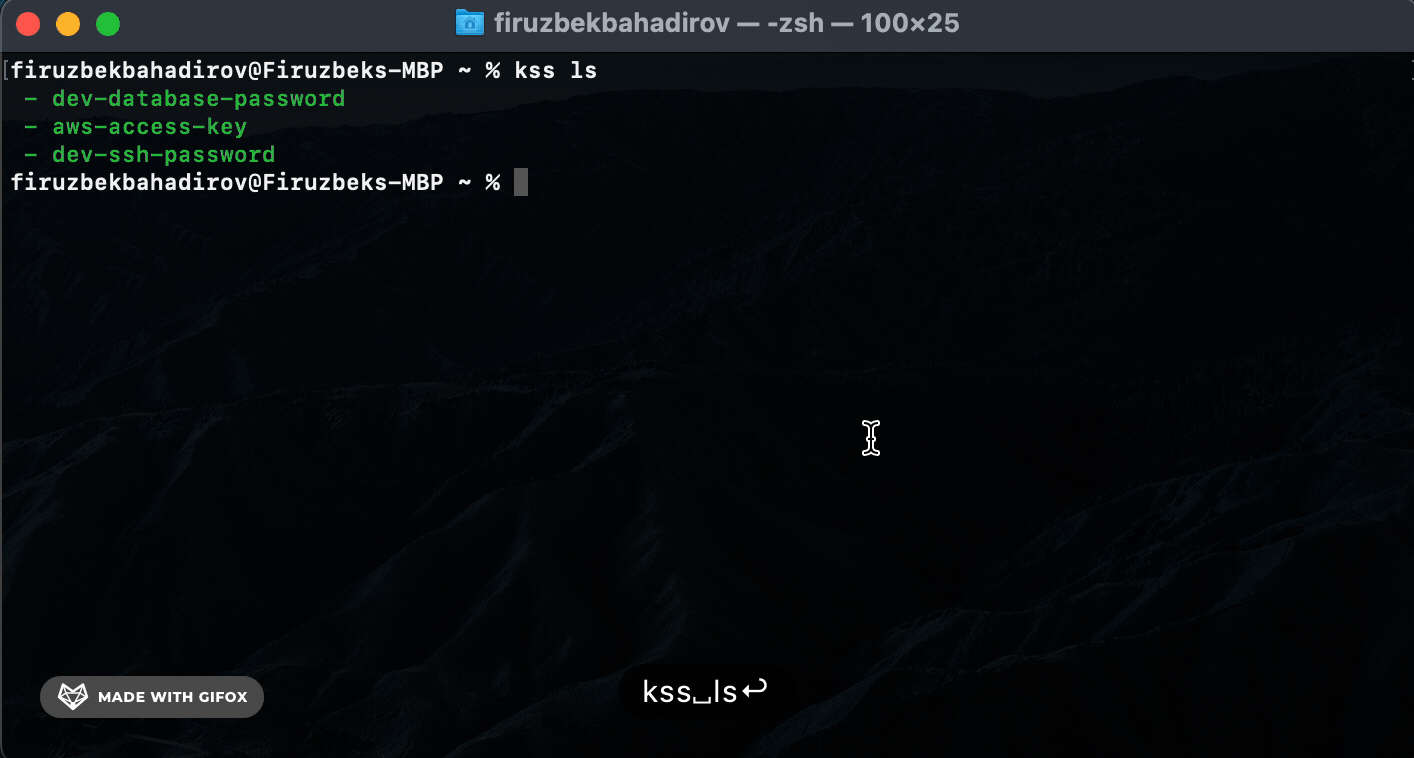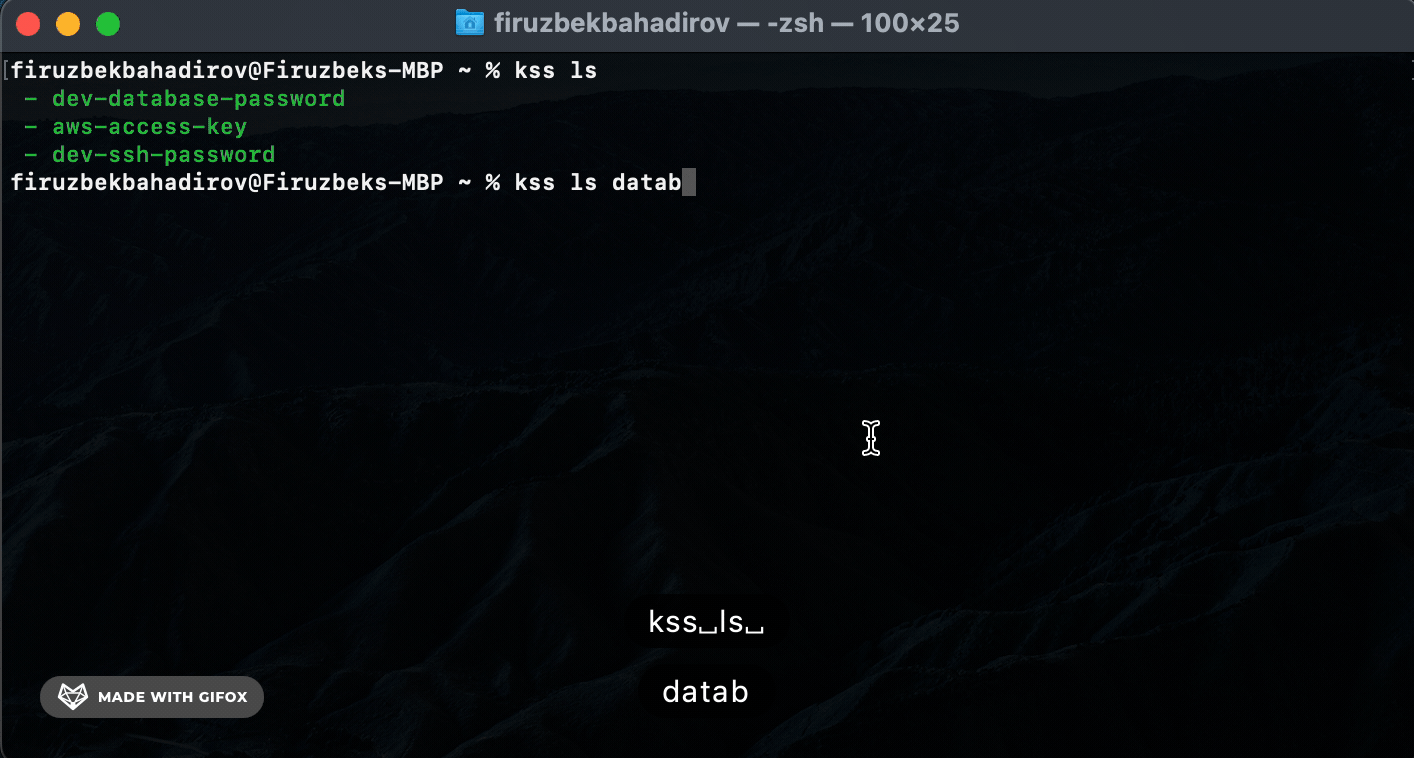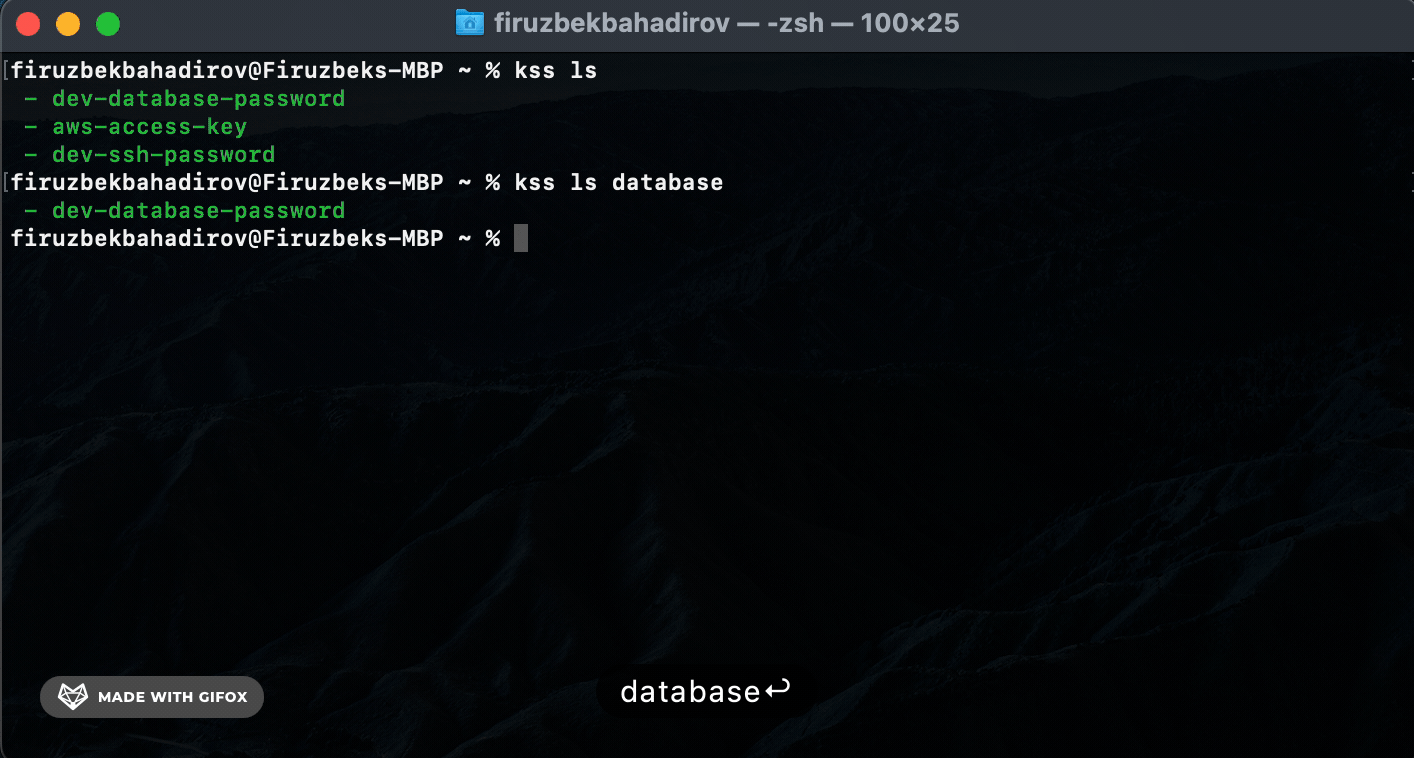
List (
ls) Command: Usekss-cli lsto list all stored secrets. Provide a[name]argument to filter the results based onsecret-name. -
Config (
config) Command: Usekss-cli configto change configuration options. Currently, the available option iskeychain-always-allow, which determines whether your app has "Always Allow" access in the keychain. By default, this option is set toenabled.
Add (add) Command. Use the add command to securely store a new secret:
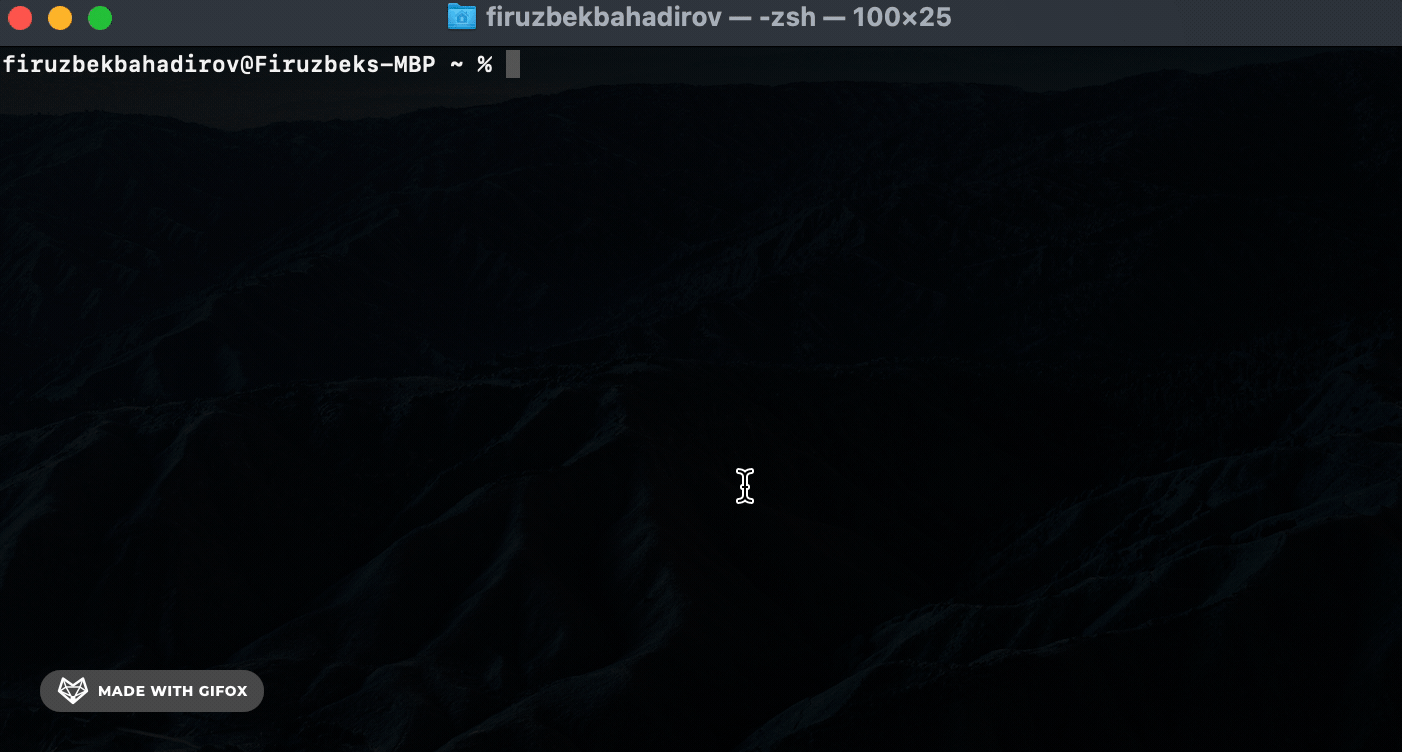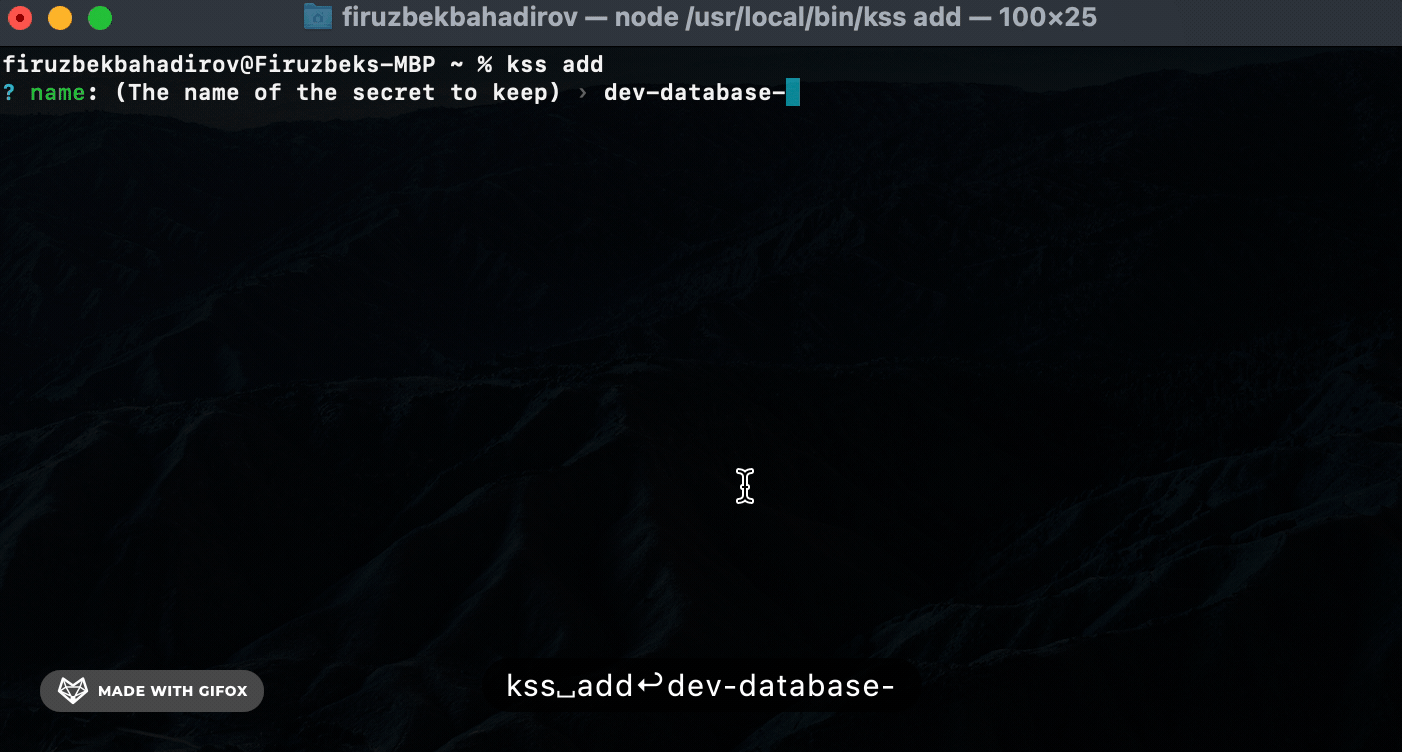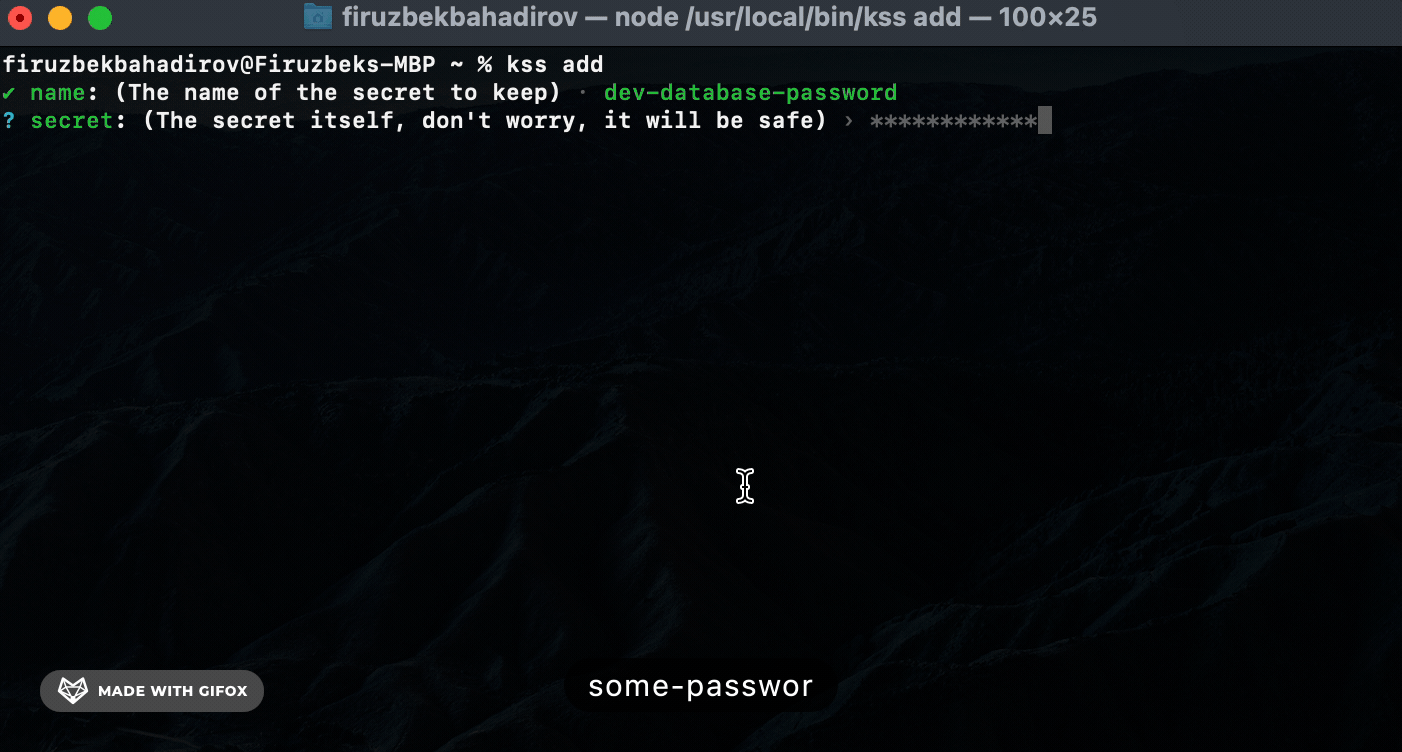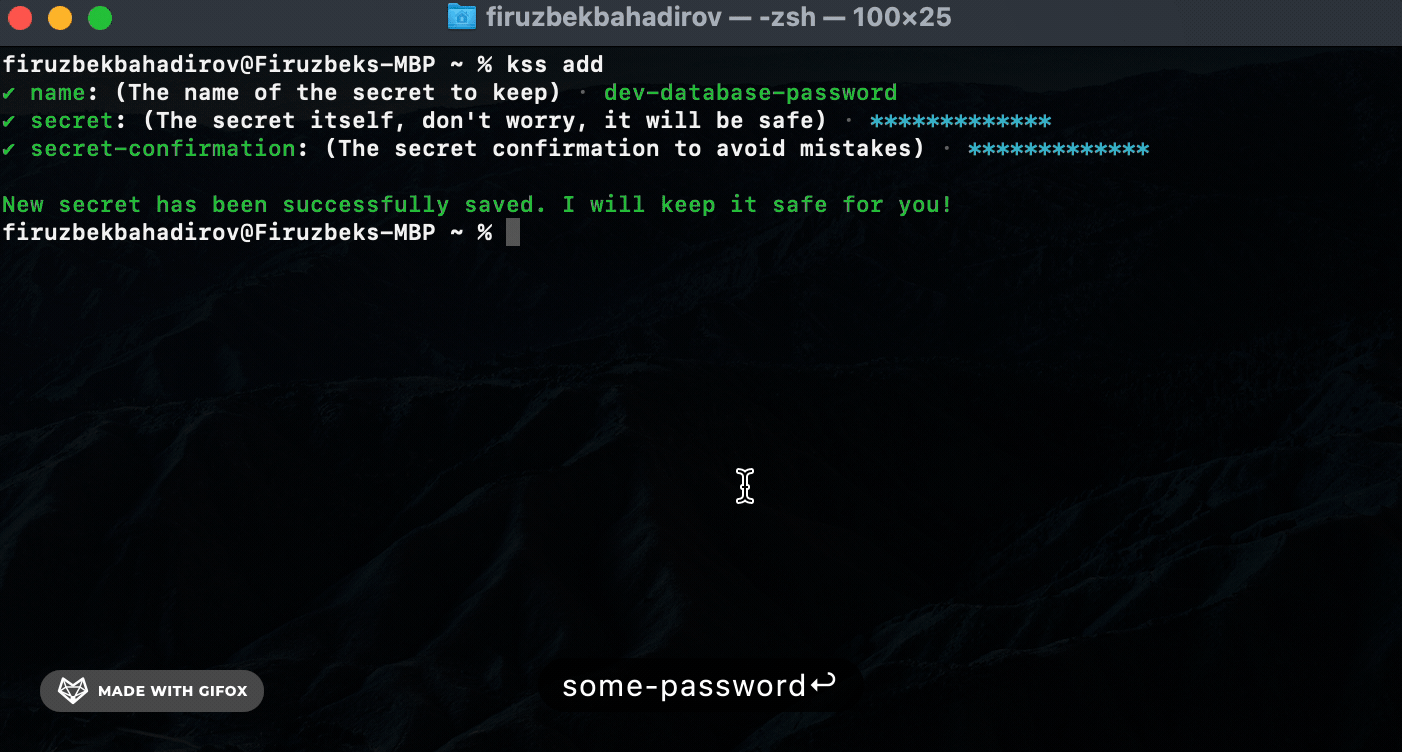
Remove (rm) Command. Use the rm command to remove a specific secret:
Copy (cp) Command. Use the cp command to copy a specific secret to the clipboard:
List (ls) Command. Use the ls command to list all stored secrets or filter results based on secret-name: