-
Notifications
You must be signed in to change notification settings - Fork 3
Commit
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
- Loading branch information
1 parent
5200c7f
commit 6af6103
Showing
1 changed file
with
1 addition
and
58 deletions.
There are no files selected for viewing
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -1,58 +1 @@ | ||
| # PS4JbEmU | ||
|
|
||
| ## Local PS4 Jailbreak Host with USB emulation | ||
| This project is aimed at setting up a local web host, with USB emulation, on select Raspberry Pi boards that can be used to exploit and jailbreak PS4 consoles running firmware version 9.00. Raspberry Pi Zero W / Pi Zero 2 W / Pi4 B are eligible boards as they support a USB on-the-go (OTG) gadget mode and eliminate the need to manually insert and remove the USB stick required in the exploit process. This project is implemented on a clean Raspberry Pi OS (Debian) install which makes it easier to repurpose the Pi to run additional applications and services on it.<br> | ||
| Developed and Tested on Raspberry Pi 4 B but should work on Pi Zero W / Pi Zero 2 W / Pi4 B | ||
|
|
||
| ### Benefits | ||
| - Clean Raspberry Pi OS install - easy to setup the Pi for other purposes as you desire | ||
| - Easily update exploit, GoldHen and payload files from the web interface | ||
| - One device for local web server and USB emulation | ||
| - One USB cable is sufficient to power the Pi and emulate USB | ||
| - You can leave the Pi permanently connected to the PS4. No need not to remove and plug in a USB stick to run explolit | ||
|
|
||
| ### Setup - Easy Method | ||
| 1. Write the image provided in the releases to an SD card (using program like Pi Imager or Rufus) | ||
| 2. Insert the SD card into the Raspberry Pi | ||
| 3. For Pi Zero W & Pi Zero 2W, connect the USB marked Pi USB port to PS4. Be sure to use a cable that supports data transfer<br> | ||
| 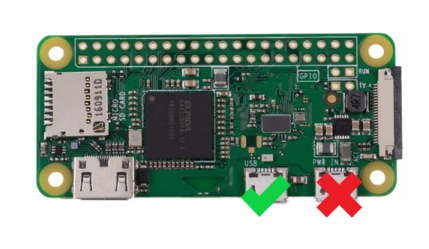 <br /> | ||
| 4. For Pi4 B, connect a USB C cable from Pi to PS4 | ||
| 5. Power up the PS4. This should also boot up your Pi | ||
| 6. Use `raspi-config` to expand the filesystem to the capacity of your SD card | ||
| 7. On the PS4 go to Browser and visit http://<ip.address.of.your.pi>/ps4 | ||
| 8. Click on the GoldHen button for the version you want to exploit with | ||
| a. A popup will be thrown saying USB emulation started and wait for ps4 pop up | ||
|  <br /> | ||
| b. Once the USB message disappears, Click ok | ||
| c. Gold Hen will load automatically | ||
| 9. If you need SSH access, username is `pi` and password is `ps4free` | ||
|
|
||
| ### Setup - Advanced Method | ||
| 1. Install a clean Raspberry Pi OS image to an SD card (Developed and tested on Debian Bullseye) | ||
| 2. Enable USB Gadget Mode on the Pi <br> | ||
| a. Add `dtoverlay=dwc2,dr_mode=peripheral` to the `[all]` section inside `/boot/config.txt` | ||
| 3. Prevent the Pi from automatically becoming a USB gadget on every boot <br /> | ||
| a. Add `sudo /sbin/modprobe -r g_mass_storage` to `/etc/rc.local` | ||
| 5. Install and setup `lighttpd` and `PHP` | ||
| 6. Enable fast cgi module for lighttpd <br /> | ||
| a. `sudo lighttpd-enable-mod fastcgi fastcgi-php` <br /> | ||
| b. `sudo systemctl reload lighttpd.service` | ||
| 8. Configure `/var/www/html/ps4` as the document root directory for the exploit app (via `lighttpd` configs) | ||
| 9. Clone or download the source code from this repo <br> | ||
| a. `cd /home/pi` <br> | ||
| b. `git clone https://github.com/CrazeeGhost/PS4JbEmu.git` <br /> | ||
| 10. Allow the webserver user to run modprobe as root without password <br> | ||
| a. Add `www-data ALL=(ALL) NOPASSWD: /sbin/modprobe` to your sudoers file using the `visudo` command | ||
| 11. Make the web app accessible to the webserver (will not work if you did not follow the directory strcture in step 8)<br /> | ||
| a. `cp /home/pi/PS4JbEmu/updateHost.sh /home/pi` <br /> | ||
| b. `sudo chmod 755 /home/pi/updateHost.sh` <br /> | ||
| c. `sudo /home/pi/updateHost.sh` | ||
| 12. (Optional) Enable auto-updates via cron <br /> | ||
| a. `sudo crontab -e` <br /> | ||
| b. `*/30 * * * * /home/pi/updateHost.sh` | ||
|
|
||
| ### Credits | ||
| 1. Kameleonre_ - Porting PSFree Exploit | ||
| 2. Sleirsgoevy – Webkit, Offline Activator | ||
| 3. Chendochap – KeExploit | ||
| 5. PaulJenkin – Inspiration for USB Emulation | ||
| # See Notes on individual releases |
6af6103There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Hello everything is fine. I saw your new script, but I have some questions if you could help me, I would really appreciate it. I use the GitHub image to install on the rsspbarry memory card. Then, will I have to make the settings with PuTTY? Or is your image already prepared with xploit replay script on PS4? folder that I activated in the PPPoE settings on the PS4 and after recording the image on the Raspberry SD card, I connect it via network cable to the PS4 and it should start running xploit?