-
Notifications
You must be signed in to change notification settings - Fork 32
Home
Included below are configuration setups for other network configurations:
As per the tailscale guide, site-to-site L3 networking connects two subnets on your Tailscale network with each other.
Consider the scenario below where we are wanting to connect the two subnet routes 192.168.88.0/24 and 192.168.99.0/24, connected to routers mikrotik-east-1 and mikrotik-west-1 respectively.
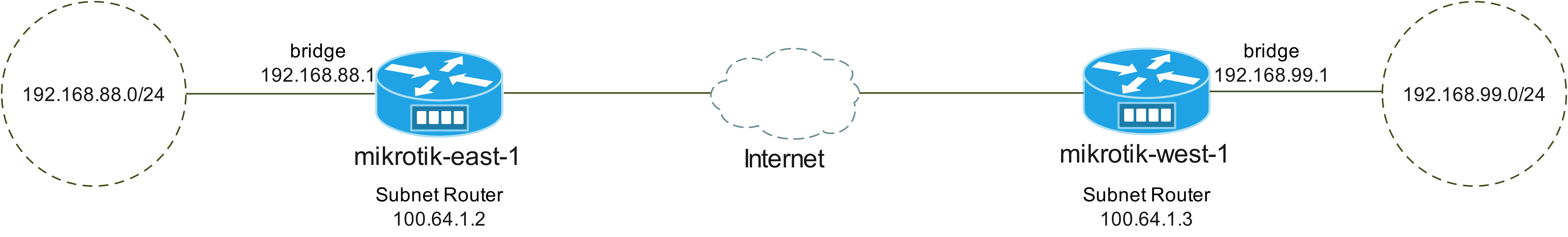
Assuming you have configured both routers as per the README, we outline the changes required to enable site-to-site networking.
- Configure the router name in the container configuration
/container set 0 hostname=mikrotik-east-1
- Disable source NAT and accept advertised routes.
/container envs
set [find where key="TAILSCALE_ARGS"] value="--snat-subnet-routes=false --accept-routes"
- Enable a static route to the remote LAN.
/ip route add dst-address=192.168.99.0/24 gateway=172.17.0.2
- Configure the router name in the container configuration
/container set 0 hostname=mikrotik-west-1
- Configure the advertised route, disable source NAT and accept advertised routes.
/container envs
set [find where key="ADVERTISE_ROUTES"] value="192.168.99.0/24"
set [find where key="TAILSCALE_ARGS"] value="--snat-subnet-routes=false --accept-routes"
- Enable a static route to the remote LAN.
/ip route add dst-address=192.168.88.0/24 gateway=172.17.0.2
In the Tailscale console, check each router is authenticated and enable the subnet routes. From each router you should now be able to ping the respective LAN bridge addresses.
[admin@mikrotik-east-1] > ping count=5 192.168.99.1 src-address=192.168.88.1
SEQ HOST SIZE TTL TIME STATUS
0 192.168.99.1 56 62 72ms450us
1 192.168.99.1 56 62 83ms540us
2 192.168.99.1 56 62 72ms439us
3 192.168.99.1 56 62 71ms856us
4 192.168.99.1 56 62 73ms389us
sent=5 received=5 packet-loss=0% min-rtt=71ms856us avg-rtt=74ms734us
max-rtt=83ms540us
[admin@mikrotik-west-1] > ping count=5 192.168.88.1 src-address=192.168.99.1
SEQ HOST SIZE TTL TIME STATUS
0 192.168.88.1 56 62 73ms193us
1 192.168.88.1 56 62 174ms928us
2 192.168.88.1 56 62 127ms837us
3 192.168.88.1 56 62 131ms916us
4 192.168.88.1 56 62 72ms677us
sent=5 received=5 packet-loss=0% min-rtt=72ms677us avg-rtt=116ms110us
max-rtt=174ms928us
In this scenario the two subnet routes 192.168.88.0/24 and 192.168.99.0/24 are connected directly between mikrotik-east-1 and mikrotik-west-1 via an Ethernet service (10.0.0.0/30).
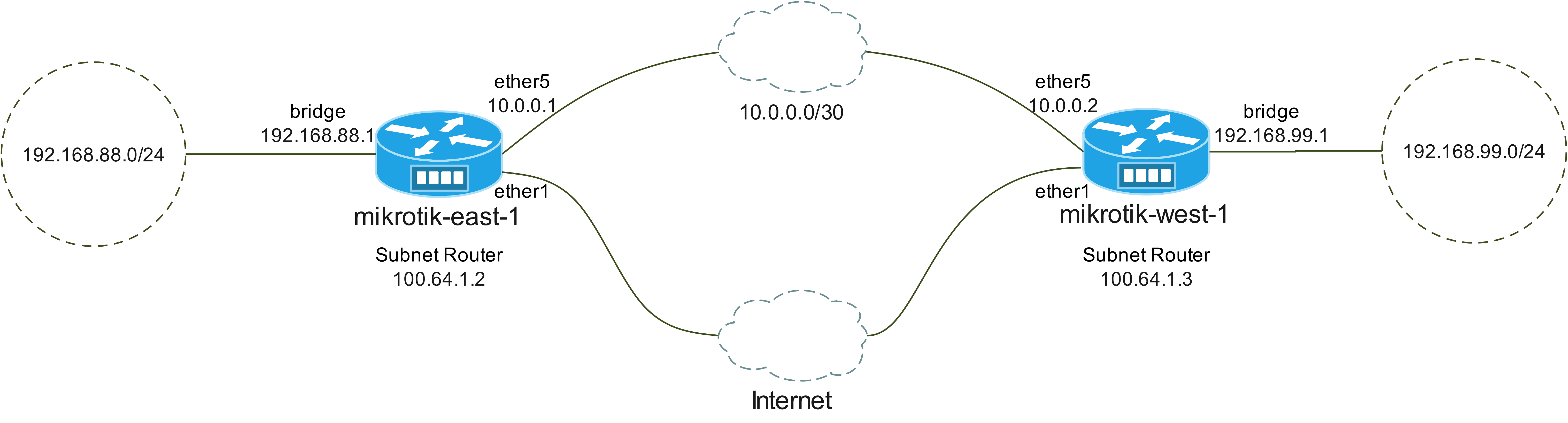
The Tailscale site to site network will be used as a backup route in the event of failure of the primary route.
This example uses static routes to accomplish the backup service, however a routing protocol, e.g. BGP, would also be applicable.
We assume both routers are configured as per the README.
- Configure the router name in the container configuration
/container set 0 hostname=mikrotik-east-1
- Disable source NAT and accept advertised routes.
/container envs
set [find where key="TAILSCALE_ARGS"] value="--snat-subnet-routes=false --accept-routes"
- Enable the primary route, use BFD to monitor the link state.
/ip route add dst-address=192.168.88.0/24 gateway=10.0.0.1 distance=1 check-gateway=bfd
- Enable a backup route with an administrative distance of 200.
/ip route add dst-address=192.168.88.0/24 gateway=172.17.0.2 distance=200
- Configure the router name in the container configuration
/container set 0 hostname=mikrotik-west-1
- Configure the advertised route, disable source NAT and accept advertised routes.
/container envs
set [find where key="ADVERTISE_ROUTES"] value="192.168.99.0/24"
set [find where key="TAILSCALE_ARGS"] value="--snat-subnet-routes=false --accept-routes"
- Enable the primary route, use BFD to monitor the link state.
/ip route add dst-address=192.168.99.0/24 gateway=10.0.0.2 distance=1 check-gateway=bfd
- Enable a backup route with an administrative distance of 200.
/ip route add dst-address=192.168.99.0/24 gateway=172.17.0.2 distance=200
In the Tailscale console, check each router is authenticated and enable the subnet routes. From each router you should now be able to ping the respective LAN bridge addresses.
Perform a continuous ping test and fail the primary interface. Here we fail the interface after the 4th ping.
[admin@mikrotik-east-1] /interface> /ping 192.168.99.1 src-address=192.168.88.1
SEQ HOST SIZE TTL TIME STATUS
0 192.168.99.1 56 64 593us
1 192.168.99.1 56 64 608us
2 192.168.99.1 56 64 616us
3 192.168.99.1 56 64 614us
4 192.168.99.1 56 64 605us
5 192.168.99.1 timeout
6 192.168.99.1 56 62 239ms49us
7 192.168.99.1 56 62 145ms631us
8 192.168.99.1 56 62 110ms191us
9 192.168.99.1 56 62 201ms225us
10 192.168.99.1 56 62 154ms849us
11 192.168.99.1 56 62 189ms894us
12 192.168.99.1 56 62 175ms886us
13 192.168.99.1 56 62 100ms782us
sent=14 received=13 packet-loss=7% min-rtt=593us avg-rtt=101ms580us
max-rtt=239ms49us