-
Notifications
You must be signed in to change notification settings - Fork 0
Introduction to Attack Trees
Attack trees have been proved to be useful in threat analysis due to their simple and unambiguous concepts. Attack Trees were introduced by Bruce Schneier as a formal way of describing the security of systems, based on a variety of attacks. Basically, attacks against a system are represented in a tree structure, with the goal as the root node and different ways of achieving that goal as leaf nodes. A node is connected to its children with one of the 2 types of conditions: AND and OR conditions. The figure below shows example of attack tree where the goal described here as Attack "A" requires the realization of both Attacks "B" AND "C".
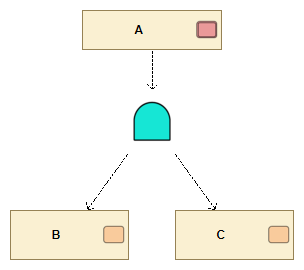
Example of an attack tree with an AND clause
The following figure shows a attack tree where the Attack "A" can be realized by either realizing Attack "B" OR "C".
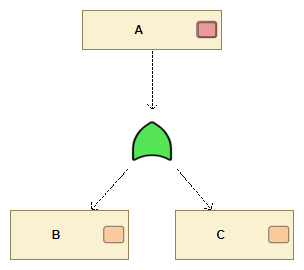
Example of an attack tree with an OR clause