diff --git a/.github/workflows/pullRequest-lint.yaml b/.github/workflows/pullRequest-lint.yaml
new file mode 100644
index 000000000..e2c4fceb4
--- /dev/null
+++ b/.github/workflows/pullRequest-lint.yaml
@@ -0,0 +1,61 @@
+# #############################################################################
+# Copyright (c) 2023 Contributors to the Eclipse Foundation
+#
+# See the NOTICE file(s) distributed with this work for additional
+# information regarding copyright ownership.
+#
+# This program and the accompanying materials are made available under the
+# terms of the Apache License, Version 2.0 which is available at
+# https://www.apache.org/licenses/LICENSE-2.0.
+#
+# Unless required by applicable law or agreed to in writing, software
+# distributed under the License is distributed on an "AS IS" BASIS, WITHOUT
+# WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. See the
+# License for the specific language governing permissions and limitations
+# under the License.
+#
+# SPDX-License-Identifier: Apache-2.0
+# #############################################################################
+
+name: "Lint PullRequest"
+
+on:
+ pull_request_target:
+ types:
+ - opened
+ - edited
+ - synchronize
+
+jobs:
+ main:
+ name: Validate PR title
+ runs-on: ubuntu-latest
+ steps:
+ - uses: amannn/action-semantic-pull-request@v5
+ id: lint_pr_title
+ env:
+ GITHUB_TOKEN: ${{ secrets.GITHUB_TOKEN }}
+
+ - uses: marocchino/sticky-pull-request-comment@v2
+ # When the previous steps fail, the workflow would stop. By adding this
+ # condition you can continue the execution with the populated error message.
+ if: always() && (steps.lint_pr_title.outputs.error_message != null)
+ with:
+ header: pr-title-lint-error
+ message: |
+ Hey there and thank you for opening this pull request! 👋🏼
+
+ We require pull request titles to follow the [Conventional Commits specification](https://www.conventionalcommits.org/en/v1.0.0/) and it looks like your proposed title needs to be adjusted.
+
+ Details:
+
+ ```
+ ${{ steps.lint_pr_title.outputs.error_message }}
+ ```
+
+ # Delete a previous comment when the issue has been resolved
+ - if: ${{ steps.lint_pr_title.outputs.error_message == null }}
+ uses: marocchino/sticky-pull-request-comment@v2
+ with:
+ header: pr-title-lint-error
+ delete: true
diff --git a/.gitignore b/.gitignore
index 8800349bb..86392e509 100644
--- a/.gitignore
+++ b/.gitignore
@@ -1,3 +1,10 @@
**/.DS_Store
node_modules
-public/documentation/js/lib
\ No newline at end of file
+public/documentation/js/lib
+
+# Add legal info files during build
+
+public/assets/notice/LICENSE
+public/assets/notice/DEPENDENCIES
+public/assets/notice/NOTICE.md
+public/assets/notice/SECURITY.md
\ No newline at end of file
diff --git a/CHANGELOG.md b/CHANGELOG.md
index 11b4b3f4e..88d250dc9 100644
--- a/CHANGELOG.md
+++ b/CHANGELOG.md
@@ -2,103 +2,72 @@
New features, fixed bugs, known defects and other noteworthy changes to each release of the Catena-X Portal Assets.
-## 1.7.0-RC4
+## 1.7.0
### Change
+- Portal Version Upgrade
+ - updated documentation for fixes, changes and news
+ - added information about PostgresSQL upgrade and recommended upgrade approach
+ - added table of content
+- Technical Documentation
+ - updated documentation for application monitoring options
+ - updated documentation about application auditing
+- Technical User documentation
+ - enhanced developer documentation of technical user deletion function
+ - added technical user credential reset documentation/flow
+ - dev documentation of new added technical user filters
+- Credential Management
+ - updated end user documentation of allowed file types and size for VC request flow
+ - added new endpoint in developer documentation regarding requestable credentials
+ - added end user FAQ
+- Technical User Role Definition
+ - removed 'Connector User' and 'App Tech User'
+ - updated 'Service Management' to 'Offer Management'
+ - added 'Semantic Model Management', 'Dataspace Discovery', 'CX Membership Info'
+ - updated permission assignment (R&R matrix documentation & portal upgrade script provided for portal db)
+- Legal information for distributions [TRG 7.05](https://eclipse-tractusx.github.io/docs/release/trg-7/trg-7-05/)
+ - added legal info at build
+- updated static template guidelines
+- enhanced/updated content for app provider introduction page
+- added onboarding service provider introduction page
+- added list of standard technical user needed to run the portal application integration with core applications
+- updated identity provider connection documentation (developer & end user) for new flow
+- enhanced subscription management board (service provider) documentation (developer & end user)
+- updated app change process (roles, tenant url, etc.) for developers and end users
+- interface contract documentation for 'Clearinghouse' updated with new architecture images and additional details of relevant authentication users and used endpoints
+- traceability use case page images and text sections updated for release 23.12
+- useCase content file updated
+- images linked for traceability useCase exchanged
- added documentation for service account sync
-- added table of content to version upgrade
- added documentation for app change documents
- added license notice and image licenses
- added notice to md files in docs and developers directory
- added check for license info headers, footers and files in pr-template
-- added data-flow diagram
+- added security assessment documentation and removed data-flow diagram (integrated in security assessment)
- moved iam specific documentation to portal-iam repository
- updated documentation for bulk user creation
- updated bpdm interface contract
+- updated offer authentication flow
- fixed typos
-### Technical Support
-
-- Trivy scan: changed to no failure on high findings, as it should only fail if there is an error/misconfiguration
-
-## 1.7.0-RC3
-
-### Change
-
-- useCase content file updated
-- images linked for traceability useCase exchanged
-- portal database upgrade documentation updated
-
### Feature
-n/a
-
-### Bugfix
-
-n/a
-
-## 1.7.0-RC2
-
-### Change
-
-- identity provider connection documentation (developer & end user); new flow released
-- subscription management board (service provider) documentation enhanced (developer & end user)
-- updated technical user role definition
- - removal of 'Connector User', 'App Tech User'
- - updated 'Service Management' to 'Offer Management'
- - added 'Semantic Model Management', 'Dataspace Discovery', 'CX Membership Info'
- - permission assignment updated (R&R Matrix documentation & portal upgrade script provided for portal db and
-- Interface contract documentation for 'Clearinghouse' updated with new architecture images and additional details of relevant authentication users and used endpoints
-- traceability use case page images and text sections updated for release 23.12
-
-### Feature
-
-n/a
-
-### Technical Support
-
-- Portal db - technical user upgrade script provided which need to get executed for upgrade from 1.6.0 to 1.7.0 RC
-- Keycloak db - technical user upgrade script provided which need to get executed for upgrade from 1.6.0 to 1.7.0 RC
-- Added linter rules and prettify gitHub actions for asset repo and fixed findings
+- Service Change Process
+ - released documentation of 'Service Deactivation'
### Bugfix
-- md file linkage
-
-## 1.7.0-RC1
-
-### Change
-
-- Updates static template guidelines
-- Enhanced/updated content for app provider introduction page
-- Added onboarding service provider introduction page
-- Technical Documentation: updated documentation for application monitoring options
-- Technical Documentation: updated documentation about application auditing
-- Technical User documentation
- - enhanced developer docu of technical user deletion function
- - added technical user credential reset documentation/flow
- - dev documentation of new added technical user filters
-- Added list of standard technical user needed to run the portal application integration with core applications
-- Updated app change process (roles, tenant url, etc.) for developers and end users
-- Credential Management
- - updated end user docu of allowed file types and size for VC request flow
- - added new endpoint in developer documentation regarding requestable credentials
- - added end user FAQ
-
-### Feature
-
-- Service Change Process
- - released docu of 'Service Deactivation'
+- updated background color used in static page last section
+- fixed links in md files
### Technical Support
-- Dependencies upgraded
-- Moved couple of images from gitHub md files to docs/static image folder/directory
-
-### Bugfix
-
-- Updated background color used in static page last section
+- upgraded dependencies
+- moved some images referenced in md file from GitHub to docs/static directory
+- added linter rules and prettify gitHub actions for asset repo and fixed findings
+- Trivy scan: changed to no failure on high findings, as it should only fail if there is an error/misconfiguration
+- added pull request linting
## 1.6.1
diff --git a/developer/Technical Documentation/Architecture/Data-Flow.md b/developer/Technical Documentation/Architecture/Data-Flow.md
deleted file mode 100644
index 8be269f58..000000000
--- a/developer/Technical Documentation/Architecture/Data-Flow.md
+++ /dev/null
@@ -1,121 +0,0 @@
-# Data Flow Diagram
-
-```mermaid
-flowchart LR
-
- RF("Registration")
- PF("Portal")
-
- RS(Registration service)
- AS(Administration service)
- MAS(Marketplace apps service)
- MSS(Marketplace services service)
- NS(Notification service)
-
- CU-Own(Company user)
-
- NC1("Potential new company (admin)")
- CU-Shared1(Company user)
-
- NC2("Potential new company (admin)")
- CU-Shared2(Company user)
-
- NC3("Potential new company (admin)")
- CU-Shared3(Company user)
-
- K("Keycloak (REST API)")
-
- BPDM(Business Partner Data Management)
- SDT(Semantic Hub)
- SDF("SD Factory \n (Self Description)")
- MIW(Managed Identity Wallets)
-
- CH(Gaia-X Clearing House)
- OSP("Onboarding Service Provider \n (Owns infrastructure \n e.g. IAM, portal and registration app, \n other core services) ")
-
- subgraph Portal
- subgraph Frontend
- RF
- PF
- end
- subgraph Backend
- RS
- AS
- MAS
- MSS
- NS
- end
- PDB[(Portal DB \n Postgres \n EF Core for mapping \n objects to SQL)]
- end
- subgraph operator[Operator IdP]
- subgraph centralidp[centralidp Keycloak]
- K
- end
- subgraph sharedidp[sharedidp Keycloak]
- subgraph companyrealm1[Company realm]
- NC1
- CU-Shared1
- end
- subgraph companyrealm2[Company realm]
- NC2
- CU-Shared2
- end
- subgraph companyrealm3[Company realm]
- NC3
- CU-Shared3
- end
- end
- end
- subgraph ownIdP
- CU-Own
- end
- subgraph cross[Catena-X Cross functions]
- BPDM
- SDT
- SDF
- MIW
- OSP
- end
- subgraph ext["External Services (3rd party)"]
- CH
- end
-
- RS <-->|Company data \n user role data \n T&C / consent agreements| RF
- RS <--> K
- RS -->|Company data \n user role data \n T&C consent agreements| PDB
-
- AS --> K
- AS <--> PF
- AS -->|"User data \n (real and technical company data)"| PDB
- AS ---|Data related to \n self description| SDF
- AS -->|"Create MIW-tenant \n update MIW-tenant (BPN-VC, Member-VC) \n update MIW-framework-VC \n update dismantler-VC \n data: BPN, Auth, Contract, Version"| MIW
- AS <-->|Company data \n signed self description| CH
- AS <-->|OSP registers its customer \n Company Data \n Admin User Record| OSP
-
- NS --> PDB & PF & K
-
- BPDM -->|"Company data (e.g. name, etc.)"| RF
- BPDM -->|"Company data (e.g. BPN)"| AS
-
- MAS -->|Company app subscription data \n app service data + user preferences| PDB
- MAS <--> K & PF
-
- MSS <--> PF & K
- MSS -->|Company app subscription data \n app service data + user preferences| PDB
-
- SDF <--> CH
-
- SDT -->|Product meta data| PF
-
- NC1 & CU-Shared1 & NC2 & CU-Shared2 & NC3 & CU-Shared3 & CU-Own --> |OIDC| K
-
- K <--> |"Authentication/authorization data (using JWT)"| RF & PF
-```
-
-## NOTICE
-
-This work is licensed under the [Apache-2.0](https://www.apache.org/licenses/LICENSE-2.0).
-
-- SPDX-License-Identifier: Apache-2.0
-- SPDX-FileCopyrightText: 2021-2023 Contributors to the Eclipse Foundation
-- Source URL: https://github.com/eclipse-tractusx/portal-assets
diff --git a/developer/Technical Documentation/Architecture/Security-Assessment.md b/developer/Technical Documentation/Architecture/Security-Assessment.md
index ceda94806..b3426b580 100644
--- a/developer/Technical Documentation/Architecture/Security-Assessment.md
+++ b/developer/Technical Documentation/Architecture/Security-Assessment.md
@@ -1,4 +1,35 @@
-# Security Assessment
+# Security Assessment Portal (incl. Frontend, Backend Services, IAM and other infrastructure)
+
+| | |
+| ------------------------- | ---------------------------------------------------------------------------------------------- |
+| Contact for product | [@evegufy](https://github.com/evegufy)
[@jjeroch](https://github.com/jjeroch) |
+| Security responsible | [@SSIRKC](https://github.com/SSIRKC)
[Szymon Kowalczyk](szymon.kowalczyk.external@zf.com) |
+| Version number of product | 23.12 |
+| Dates of assessment | 2023-11-14: Re-Assessment |
+| Status of assessment | RE-ASSESSMENT DRAFT |
+
+## Product Description
+
+The Catena-X Portal and Marketplace is the heart of Catena-X and the entry point for all activities in the automotive network/value chain.
+Every user of the automotive value chain, no matter if it is a consumer, app provider, IT administrator or IT support will connect via the portal to the value bringing services.
+The whole eco-system on the automotive value chain is connected at one place.
+
+- Portal Frame
+- Partner Onboarding Process (initial, technical & business)
+- Login Process
+- User Management
+- App Store
+- Developer Platform
+- UI / UX & Developer Guidelines
+
+### Important Links
+
+- [portal-frontend](https://github.com/eclipse-tractusx/portal-frontend)
+- [portal-frontend-registration](https://github.com/eclipse-tractusx/portal-frontend-registration)
+- [portal-shared-components](https://github.com/eclipse-tractusx/portal-shared-components)
+- [portal-assets](https://github.com/eclipse-tractusx/portal-assets)
+- [portal-backend](https://github.com/eclipse-tractusx/portal-backend)
+- [portal-iam](https://github.com/eclipse-tractusx/portal-iam)
## Data Flow Diagram
@@ -14,18 +45,26 @@ flowchart LR
MSS(Marketplace services service)
NS(Notification service)
- NC("Potential new company (admin)")
- CU-Shared(Company user)
CU-Own(Company user)
+ NC1("Potential new company (admin)")
+ CU-Shared1(Company user)
+
+ NC2("Potential new company (admin)")
+ CU-Shared2(Company user)
+
+ NC3("Potential new company (admin)")
+ CU-Shared3(Company user)
+
K("Keycloak (REST API)")
BPDM(Business Partner Data Management)
- SDT(Semantic Hub / Digital Twin)
- SDR("SD-Registry \n (Self Description)")
+ SDT(Semantic Hub)
+ SDF("SD Factory \n (Self Description)")
MIW(Managed Identity Wallets)
CH(Gaia-X Clearing House)
+ OSP("Onboarding Service Provider \n (Owns infrastructure \n e.g. IAM, portal and registration app, \n other core services) ")
subgraph Portal
subgraph Frontend
@@ -41,14 +80,22 @@ flowchart LR
end
PDB[(Portal DB \n Postgres \n EF Core for mapping \n objects to SQL)]
end
- subgraph Keycloak
- subgraph centralidp
+ subgraph operator[Operator IdP]
+ subgraph centralidp[centralidp Keycloak]
K
end
- subgraph sharedidp
- subgraph Company realms
- NC
- CU-Shared
+ subgraph sharedidp[sharedidp Keycloak]
+ subgraph companyrealm1[Company realm]
+ NC1
+ CU-Shared1
+ end
+ subgraph companyrealm2[Company realm]
+ NC2
+ CU-Shared2
+ end
+ subgraph companyrealm3[Company realm]
+ NC3
+ CU-Shared3
end
end
end
@@ -58,40 +105,156 @@ flowchart LR
subgraph cross[Catena-X Cross functions]
BPDM
SDT
- SDR
+ SDF
MIW
+ OSP
end
subgraph ext["External Services (3rd party)"]
CH
end
-
- RS <-->|Company data \n user role data \n T&C / consent agreements| RF
- RS <--> K
- RS -->|Company data \n user role data \n T&C consent agreements| PDB
- RS -->|"Company data (e.g. name, etc.)"| BPDM
-
- AS --> K
+RS <-->|Company data \n user role data \n T&C / consent agreements| RF
+ RS <-.-> K
+ RS ==>|Company data \n user role data \n T&C consent agreements| PDB
+ AS -.-> K
AS <--> PF
- AS -->|"User data \n (real and technical company data)"| PDB
- AS -->|Data related to \n self description| SDR
+ AS ==>|"User data \n (real and technical company data)"| PDB
+ AS ---|Data related to \n self description| SDF
AS -->|"Create MIW-tenant \n update MIW-tenant (BPN-VC, Member-VC) \n update MIW-framework-VC \n update dismantler-VC \n data: BPN, Auth, Contract, Version"| MIW
- AS -->|Company data \n signed self description| CH
+ AS <-->|Company data \n signed self description| CH
+ AS <-->|OSP registers its customer \n Company Data \n Admin User Record| OSP
+ NS --> PF
+ NS ==> PDB
+ NS -.-> K
+ BPDM -.->|"Company data (e.g. name, etc.)"| RF
+ BPDM -->|"Company data (e.g. BPN)"| AS
+ MAS ==>|Company app subscription data \n app service data + user preferences| PDB
+ MAS <--> PF
+ MAS <-.-> K
+ MSS <--> PF
+ MSS <-.-> K
+ MSS ==>|Company app subscription data \n app service data + user preferences| PDB
+ SDF <--> CH
+ SDT -.->|Product meta data| PF
+ NC1 & CU-Shared1 & NC2 & CU-Shared2 & NC3 & CU-Shared3 & CU-Own -.-> |OIDC| K
+ K <-.-> |"Authentication/authorization data (using JWT)"| RF & PF
+ subgraph Legend
+ C1("Component 1")
+ D1[("Database")]
+ C1 <-.-> |https| D1
+ C1 <--> |https| D1
+ C1 <==> |https| D1
+
+ end
+```
+
+### Changes compared to last Security Assessment
+
+- No major architectural changes that introduce new threats.
+- Main changes are connections to the onboarding service provider.
- MAS -->|Company app subscription data \n app service data + user preferences| PDB
- MAS <--> K & PF
+### Features for Upcoming Versions
- MSS <--> PF & K
- MSS -->|Company app subscription data \n app service data + user preferences| PDB
+- Integration of onboarding service provider endpoints.
- NS --> PDB & PF & K
+## Threats & Risks
- PF -->|Product meta data| SDT
- PF -->|"Company data (e.g. BPN)"| BPDM
+All threats identified are mitigated.
- NC & CU-Shared & CU-Own --> |OIDC| K
+### Mitigated Threats
- K <--> |"Authentication/authorization data (using JWT)"| RF & PF
+- Risks from Logging: Repudiation, Corrupted Logs, Compromised Audit Capabilities
+ - Follow best practices for logging - ensure logs are being sent over a secure channel and that there is additional monitoring on logs originating from lower trust sources. Ensure the source of the logs is authenticated before accepting logs. Review substance of logs with security administrators and data protection officer. Integrity monitoring can be implemented at a later stage by the operator.
+- Elevation by Changing the Execution Flow in Front-End, Out-of-band resource load (HTTP)
+ - An operator should review the purpose and intended use of the relevant application functionality, and determine whether the ability to trigger arbitrary out-of-band resource load is intended behavior. If so, you should be aware of the types of attacks that can be performed via this behavior and take appropriate measures. These measures might include blocking network access from the application server to other internal systems, and hardening the application server itself to remove any services available on the local loopback adapter. You should also ensure that content retrieved from other systems is processed in a safe manner, with the usual precautions that are applicable when processing input from direct incoming web requests. If the ability to trigger arbitrary out-of-band resource load is not intended behavior, then you should implement a whitelist of permitted URLs, and block requests to URLs that do not appear on this whitelist.
+- Cross Site Scripting (XSS) \* Input validation for both front ends would greatly reduce chances of this threat. Input should be sanitized syntactically and also be checked semantically.
+ All variables go through validation and are then escaped or sanitized (confirmation needed). API call validation - best practice that is implemented. Output encoding - unsure on current implementation.
+- Cross Site Request Forgery (XSRF)
+ - Unique Session IDs, Anti-CSRF token, SSL/TLS implemented.
+- Weakness in SSO Authorization Protocol
+ - Mitigated with the standardized protocol implementation.
+- Replay Attacks
+ - Token validation in place and this threat was not discovered in the PenTest.
+- Weak Authentication Scheme
+ - Implementation of Password Policies for all Catena-X IdP users. The password policies need to get configured, tested and automated to have the possibility to run the configuration by new realm creation.
+- SQL Injection - This issue is addressed within the capabilities of .NET and includes:
+ - Parameterization
+ - Input Validation
+ - Other Framework Mechanisms (e.g. Query Builder Methods)
+- Breach of Portal DB Information
+ - Migrations .NET mechanisms applied (restrict the access)
+ - No root or default users
+ - All users are restricted (custom user, custom access restriction)
+- Data Flow HTTPS Is Potentially Interrupted (Resource Overload)
+ - Service Accounts for all APIs
+ - Rate Limiting
+- Process Crash
+ - Availability implemented by having multiple pods in parallel (Check for pod failure + rolling updates)
+ - Access to resources restricted by AAA mechanisms
+ - Infrastructure measures applied like (in reference implementation), but this is covered by the operating company
+- JavaScript Object Notation Processing / Hijacking Attacks
+ - .NET parser implemented for JSON according to best practices
+- K8s Breach
+ - Kubernetes configured through Helm Chart, reviewed by KICS scan (scans for security vulnerabilities) - overall best practices to be managed by DevOps.
+- Service Account Handling (Client Secret/ ID storage
+ - Secrets are safely stored in KeyCloak
+ - Secret handling is fully implemented on provider side (KeyCloak)
+ - These measures are applied overall to all service accounts
+
+### Performed Security Checks
+
+- Static Application Security Testing (SAST) - VeraCode
+- Dynamic Application Security Testing (DAST) - Invicti
+- Secret Scanning - GitGuardian, GitHub, VeraCode
+- Software Composition Analysis (SCA) - VeraCode
+- Container Scan conducted - Trivy
+- Infrastructure as Code - KICS
+
+### Penetration Testing
+
+The lasted Penetration Test by an external security testing company was performed on version 1.6.0-RC1 and took place during the period of July-August 2023.
+
+The following overview shows the open findings at the time of the release of version 1.7.0:
+
+```mermaid
+gantt
+ title Findings Portal Backend
+ dateFormat X
+ axisFormat %s
+
+ section Critical
+ 0 : 0, 0
+ section High
+ 0 : 0, 0
+ section Medium
+ 2 : 0, 2
+ section Low
+ 5 : 0, 5
- %% workaround to improve arrangement of subgraphs
- K ~~~ ownIdP & cross & ext
```
+
+```mermaid
+gantt
+ title Findings Portal Frontend
+ dateFormat X
+ axisFormat %s
+
+ section Critical
+ 0 : 0, 0
+ section High
+ 0 : 0, 0
+ section Medium
+ 2 : 0, 2
+ section Low
+ 5 : 0, 5
+
+```
+
+As outlined in the [Security Policy](../../../SECURITY.md), the findings will be documented as security advisories.
+
+## NOTICE
+
+This work is licensed under the [Apache-2.0](https://www.apache.org/licenses/LICENSE-2.0).
+
+- SPDX-License-Identifier: Apache-2.0
+- SPDX-FileCopyrightText: 2021-2023 Contributors to the Eclipse Foundation
+- Source URL: https://github.com/eclipse-tractusx/portal-assets
diff --git a/developer/Technical Documentation/Interface Contracts/BPDM.md b/developer/Technical Documentation/Interface Contracts/BPDM.md
index d3ea105db..5d3c5337f 100644
--- a/developer/Technical Documentation/Interface Contracts/BPDM.md
+++ b/developer/Technical Documentation/Interface Contracts/BPDM.md
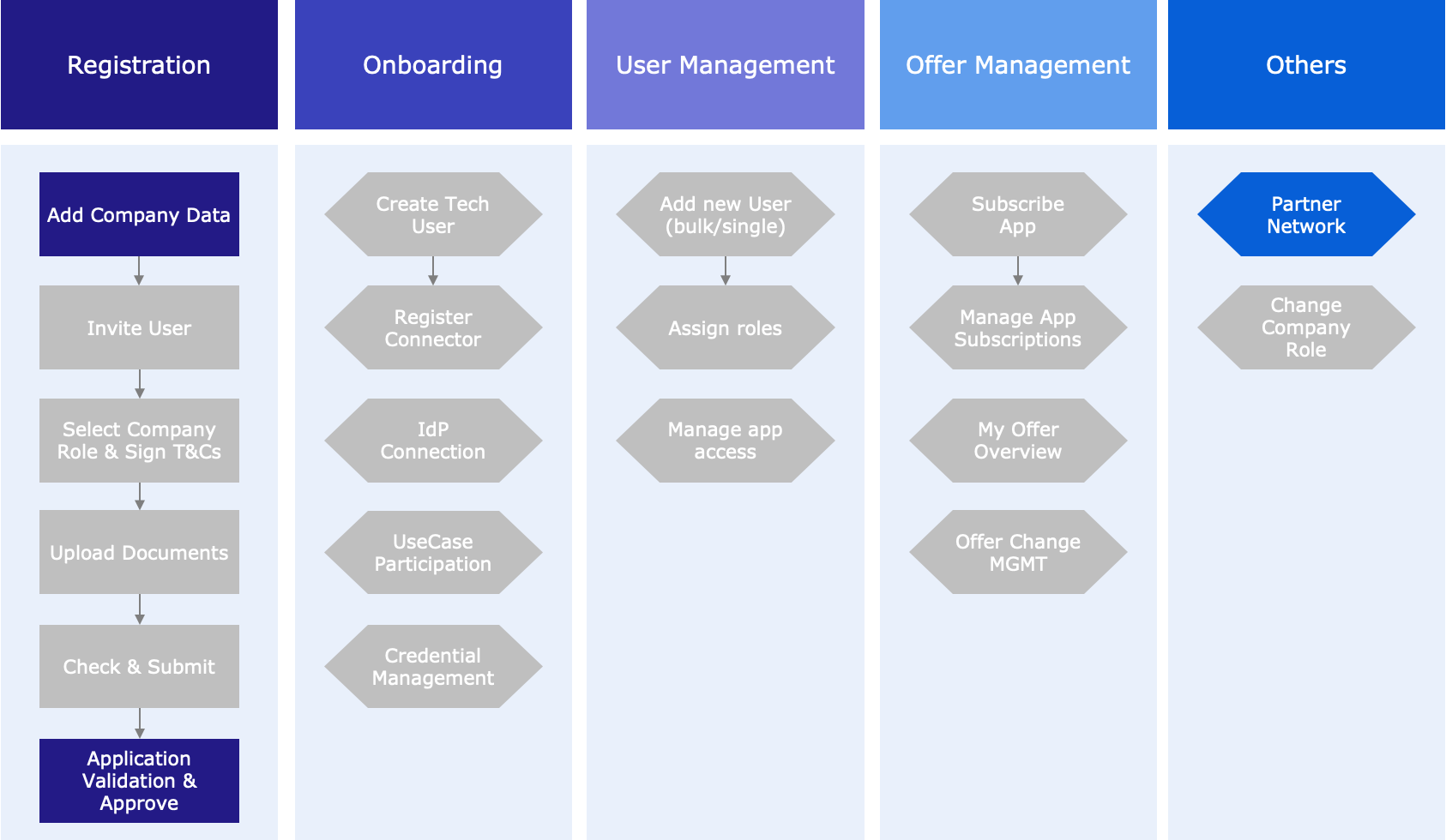
@@ -15,7 +15,7 @@ Business Partner Data Management as a product as well as the portal have three d
Below the respective touched business process steps are highlighted to enable an easier mapping of the interfaces to the portal product business process:
- +
+
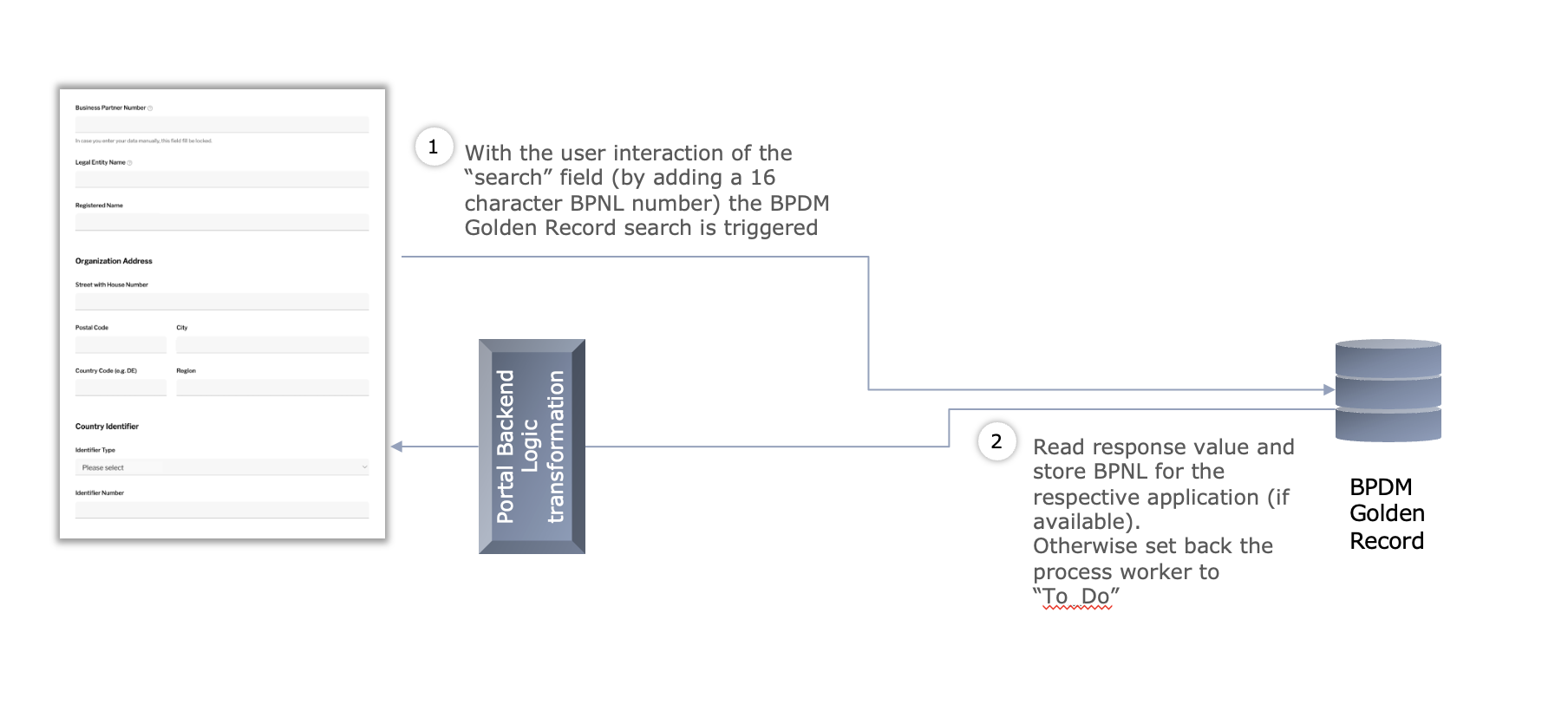
@@ -47,7 +47,7 @@ For the registration process we are using the BPDM data call to pull the company
To integrate the API into CX onboarding process, portal team just have to call the lookup REST endpoint and transform the response into a pick list for the portal user.
- +
+
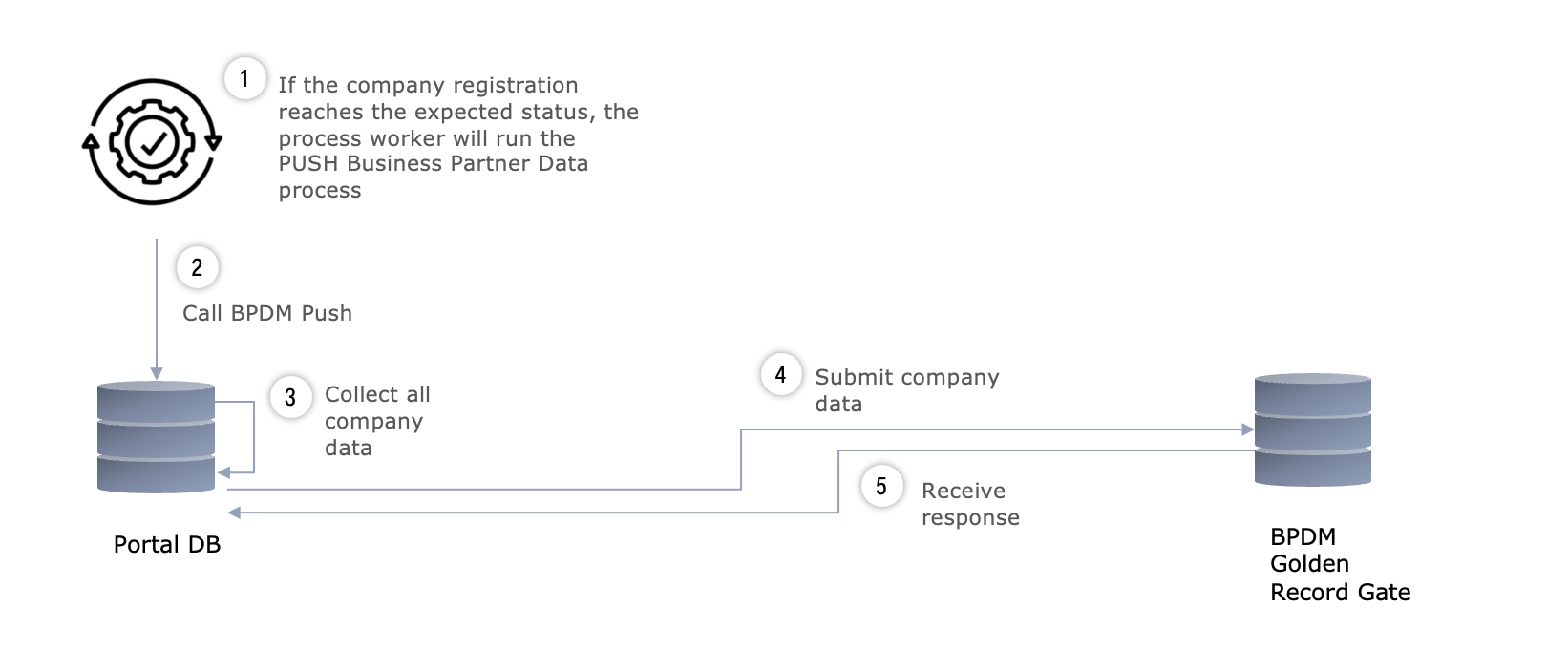
@@ -60,7 +60,7 @@ Retrieving company data from the CX mirror.
### Description of the physical interfaces (HOW)
- +
+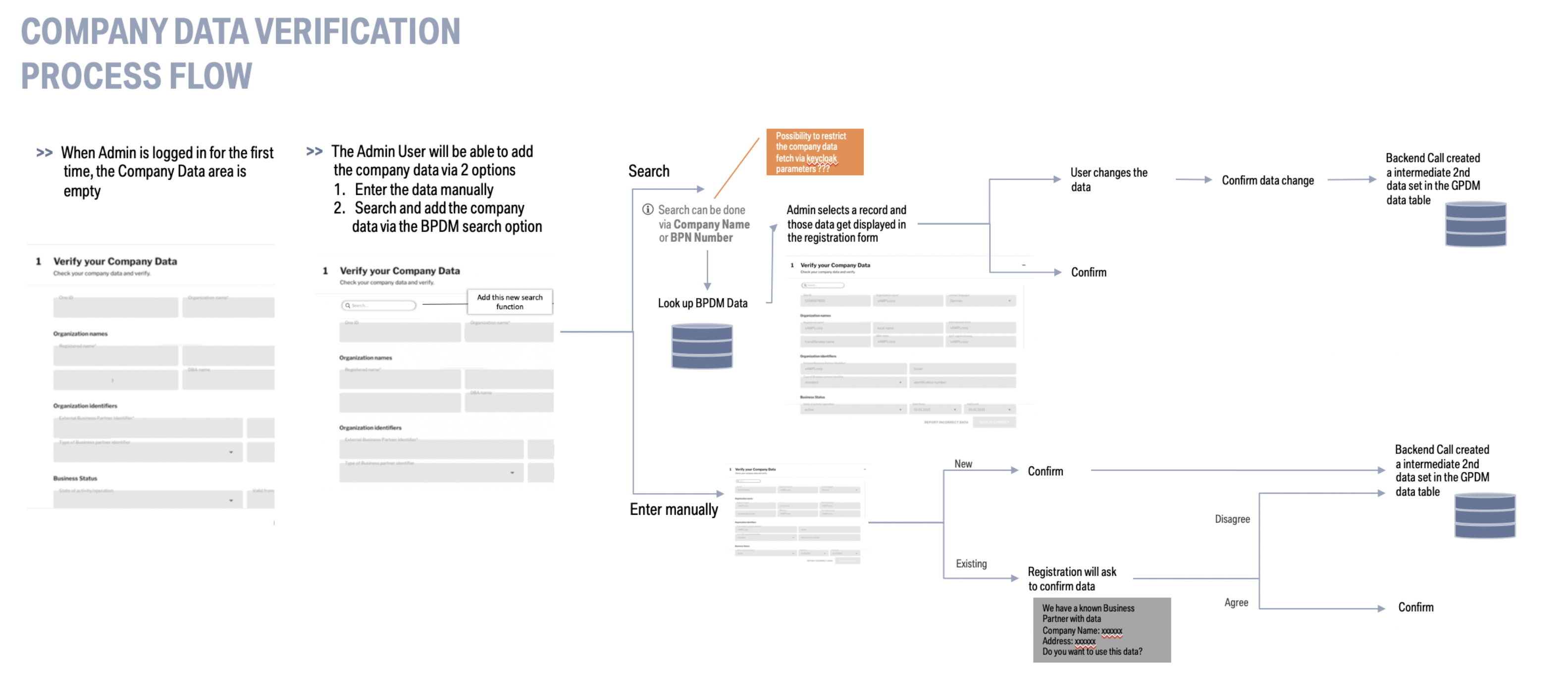
@@ -131,7 +131,7 @@ The Golden Record has a couple of implemented validations to validate the regist
- +
+
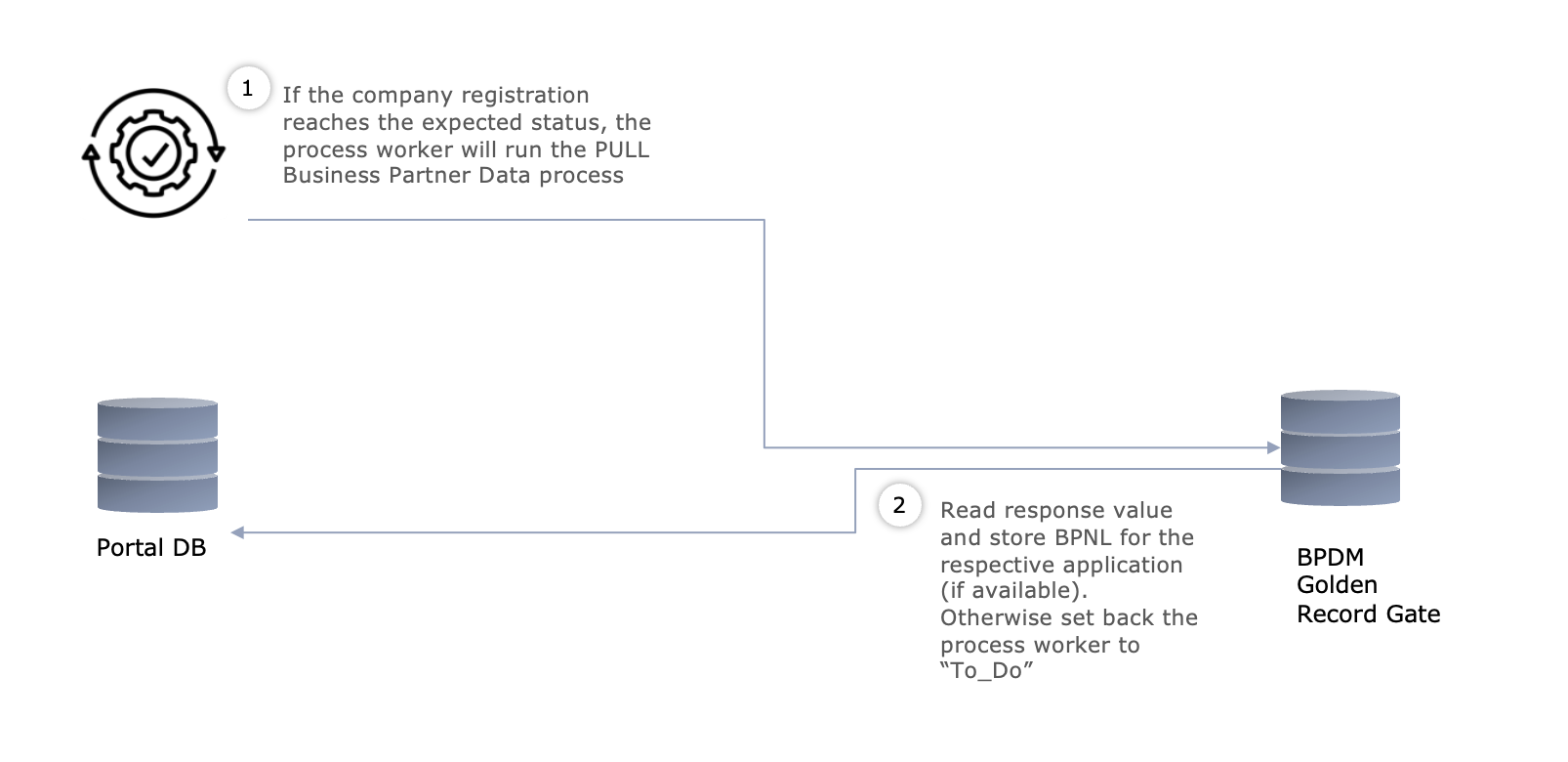
@@ -206,7 +206,7 @@ The interface is used to fetch the BPN of the previously submitted party registr
### Architecture Overview
- +
+
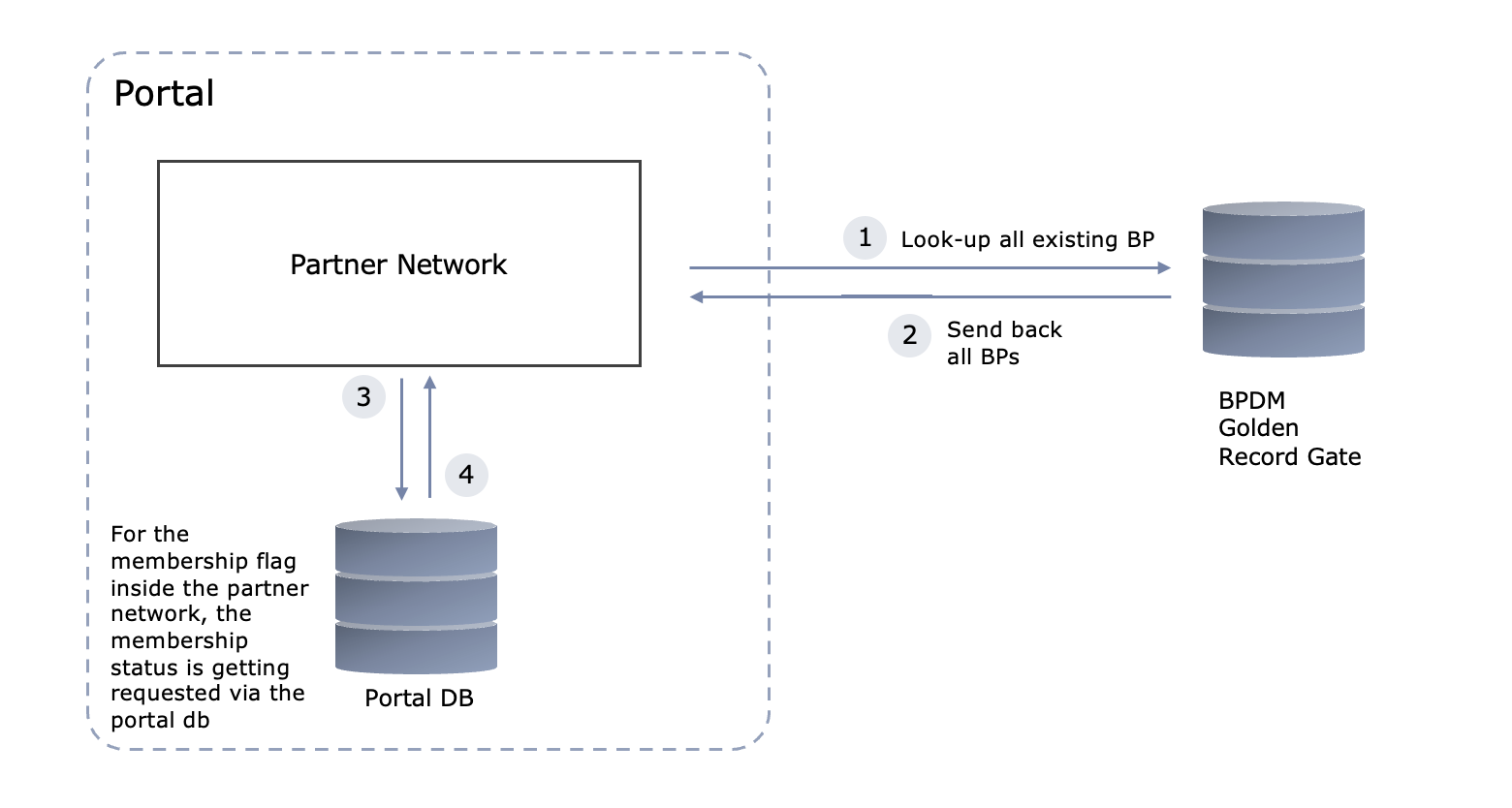
@@ -278,7 +278,7 @@ This document describes the details of the interface spec between BPDM and Porta
### Architecture Overview
- +
+
diff --git a/developer/Technical Documentation/Version Upgrade/portal-upgrade-details.md b/developer/Technical Documentation/Version Upgrade/portal-upgrade-details.md
index 67b22cabc..91bcd3aec 100644
--- a/developer/Technical Documentation/Version Upgrade/portal-upgrade-details.md
+++ b/developer/Technical Documentation/Version Upgrade/portal-upgrade-details.md
@@ -1,11 +1,13 @@
- [Summary](#summary)
- [v1.7.0](#v170)
+ - [PostgreSQL - Upgrade](#postgresql---upgrade)
- [Company Service Account - FIX](#company-service-account---fix)
- [Enable OSP Provider IdPs - Update](#enable-osp-provider-idps---update)
- [Enable Application Types - NEW](#enable-application-types---new)
- [Enable Onboarding Service Provider - NEW](#enable-onboarding-service-provider---new)
- [Technical Role - UPDATE](#technical-role---update)
- [Database Constraints - FIX](#database-constraints---fix)
+ - [Technical User Profile - CHANGE](#technical-user-profile---change)
- [v1.6.0](#v160)
- [Company Credential Details - NEW](#company-credential-details---new)
- [Connectors - CHANGED](#connectors---changed)
@@ -28,6 +30,38 @@ Each section includes the respective change details, impact on existing data and
### v1.7.0
+#### PostgreSQL - Upgrade
+
+Please be aware that the PostgreSQL version of the subchart by Bitnami of the [portal helm chart](https://github.com/eclipse-tractusx/portal-cd) is upgraded from 14.5.0 to 15.4.x (dependency updated from version 11.9.13 to 12.12.x).
+
+In case you are using an external PostgreSQL instance and would like to upgrade to 15.x, please follow the [official instructions](https://www.postgresql.org/docs/15/upgrading.html).
+
+In case you would like to upgrade the PostgreSQL subchart from Bitnami, we recommend a blue-green deployment approach. In the following, you find a rough outline of the necessary steps:
+
+1. Scale down the current Portal services and suspend jobs (blue deployment)
+2. Backup the current data
+3. Deploy the new Portal instance (green deployment e.g: `-green`, `-portal170`, ...) in another namespace than the blue instance
+4. Restore the data of the blue instance to the green instance
+5. Start the new Portal services
+6. Make sure that the database migrations jobs which are defined as post-upgrade hooks are completed successfully
+7. Once the new/green instance is validated, switch the user traffic to it
+
+For restoring the data of the blue instance to the green instance (step 4), execute the following statement using [pg-dumpall](https://www.postgresql.org/docs/current/app-pg-dumpall.html):
+
+On the cluster:
+
+```shell
+ kubectl exec -it green-postgresql-primary-0 -n green-namespace -- /opt/bitnami/scripts/postgresql/entrypoint.sh /bin/bash -c 'export PGPASSWORD=""; echo "local all postgres trust" > /opt/bitnami/postgresql/conf/pg_hba.conf; pg_ctl reload; time pg_dumpall -c -h 10-123-45-67.blue-namespace.pod.cluster.local -U postgres | psql -U postgres'
+```
+
+Or on the primary pod of the new/green PostgreSQL instance:
+
+```shell
+/opt/bitnami/scripts/postgresql/entrypoint.sh /bin/bash -c 'export PGPASSWORD=""; echo "local all postgres trust" > /opt/bitnami/postgresql/conf/pg_hba.conf; pg_ctl reload; time pg_dumpall -c -h 10-123-45-67.blue-namespace.pod.cluster.local -U postgres | psql -U postgres'
+```
+
+Where '10-123-45-67' is the cluster IP of the old/blue PostgreSQL instance.
+
#### Company Service Account - FIX
To fix the empty user_entity_id for company_service_accounts the following process can be created. It will than run the process which will request the user from keycloak and set the user_entity_id for the corresponding company_service_account.
@@ -44,7 +78,7 @@ values ('68d28f88-85fc-43a9-835a-fce0d5a9e665', 300, 1, '2023-02-21 08:15:20.479
The `identity_providers` table has been adjusted to provide the possibility to safe the owner of the idp.
-
+
- added "Identity_Provider_Types" table which is connected to portal.identity_providers table
- added inside the new table "Identity_Provider_Types" an id as well as a label. Labels are defined below:
@@ -88,7 +122,7 @@ Logic:
The `company_applications` table has been expanded. New columns `company_application_type`, `onboarding_service_provider_id` have been added to have the possibility to track which onboarding service provider started an application for a specific company.
-
+
"onboarding_service_provider_id" => nullable
"external" => enum; 1 = "INTERNAL", 2 = "EXTERNAL"
@@ -106,7 +140,7 @@ NEW portal.onboarding_service_provider_details to safe information of the onboar
#### Technical Role - UPDATE
-To align the portal database with the Keycloak database the following SQL must be executed against the portal database. The script will replace the 'Connector User' role with the roles 'Semantic Model Management' and 'Dataspace Discovery'. As well as replace the 'App Tech User' role with 'Semantic Model Management', 'Dataspace Discovery' and 'CX Membership Info'. This results in all identity assigned roles being replaced, all technical user profile assigned roles being updated and the old roles being removed from the database.
+To align the portal database with the Keycloak database the following SQL must be executed against the portal database. The script will replace the 'Connector User' role with the roles 'Semantic Model Management', 'Identity Wallet Management' and 'Dataspace Discovery'. As well as replace the 'App Tech User' role with 'Semantic Model Management', 'Dataspace Discovery' and 'CX Membership Info'. This results in all identity assigned roles being replaced, all technical user profile assigned roles being updated and the old roles being removed from the database.
```sql
WITH connector_users AS (
@@ -122,7 +156,7 @@ connector_roles_to_insert AS (
CROSS JOIN (
SELECT id
FROM portal.user_roles
- WHERE user_role IN ('Semantic Model Management', 'Dataspace Discovery')
+ WHERE user_role IN ('Semantic Model Management', 'Identity Wallet Management', 'Dataspace Discovery')
) AS ur
)
INSERT INTO portal.identity_assigned_roles (identity_id, user_role_id)
@@ -168,7 +202,7 @@ connector_profiles_to_insert AS (
CROSS JOIN (
SELECT id
FROM portal.user_roles
- WHERE user_role IN ('Semantic Model Management', 'Dataspace Discovery')
+ WHERE user_role IN ('Semantic Model Management', 'Identity Wallet Management', 'Dataspace Discovery')
) ur
)
INSERT INTO portal.technical_user_profile_assigned_user_roles (technical_user_profile_id, user_role_id)
@@ -329,6 +363,36 @@ FOR EACH ROW
EXECUTE PROCEDURE portal.tr_is_external_type_use_case();
```
+#### Technical User Profile - CHANGE
+
+**Hint:** This is only applicable if you're running on a release candidate 1.7.0-alpha - 1.7.0-RC5
+
+To make sure that all apps have at least one technical user profile assigned, please execute the following script against the portal db:
+
+```sql
+
+CREATE EXTENSION IF NOT EXISTS "uuid-ossp";
+
+WITH inserted_profiles AS (
+ INSERT INTO portal.technical_user_profiles (id, offer_id)
+ SELECT uuid_generate_v4(), o.id
+ FROM portal.offers AS o
+ LEFT JOIN portal.technical_user_profiles AS tup ON o.id = tup.offer_id
+ WHERE o.offer_type_id != 2 AND tup.offer_id IS NULL
+ RETURNING id
+)
+
+INSERT INTO portal.technical_user_profile_assigned_user_roles (technical_user_profile_id, user_role_id)
+SELECT ip.id AS technical_user_profile_id, ur.default_user_role_id AS user_role_id
+FROM inserted_profiles AS ip
+CROSS JOIN (
+ SELECT roles.id
+ FROM portal.user_roles as roles
+ where roles.user_role in ('Identity Wallet Management', 'Dataspace Discovery', 'Semantic Model Management')
+) AS ur(default_user_role_id);
+
+```
+
### v1.6.0
#### Company Credential Details - NEW
@@ -353,11 +417,11 @@ New verified_credential_external_types, verified_credential_external_type_use_ca
Company SSI Database Structure
-
+
Use Case Database Structure
-
+
- NEW: table "language_long_names"
- ENHANCED: table portal.languages "long_name_de" and "long_name_en" removed
@@ -494,7 +558,7 @@ Attributes
- service_type_id (connected to portal.service_types and replacing table service_assigned_service_types)
- technical_user_needed (true/false flag)
-
+
Impact on existing data:
Migration script existing, based on the service type which is fetched for all existing data from portal table service_assigned_service_types, the technical_user_needed attribute is set to "true" for "DATASPACE_SERVICE" services and "false" for "CONSULTANCE_SERVICE".
diff --git a/docs/03. User Management/01. User Account/04. Create new user account (bulk).md b/docs/03. User Management/01. User Account/04. Create new user account (bulk).md
index 8c9a70a6d..5db094ce3 100644
--- a/docs/03. User Management/01. User Account/04. Create new user account (bulk).md
+++ b/docs/03. User Management/01. User Account/04. Create new user account (bulk).md
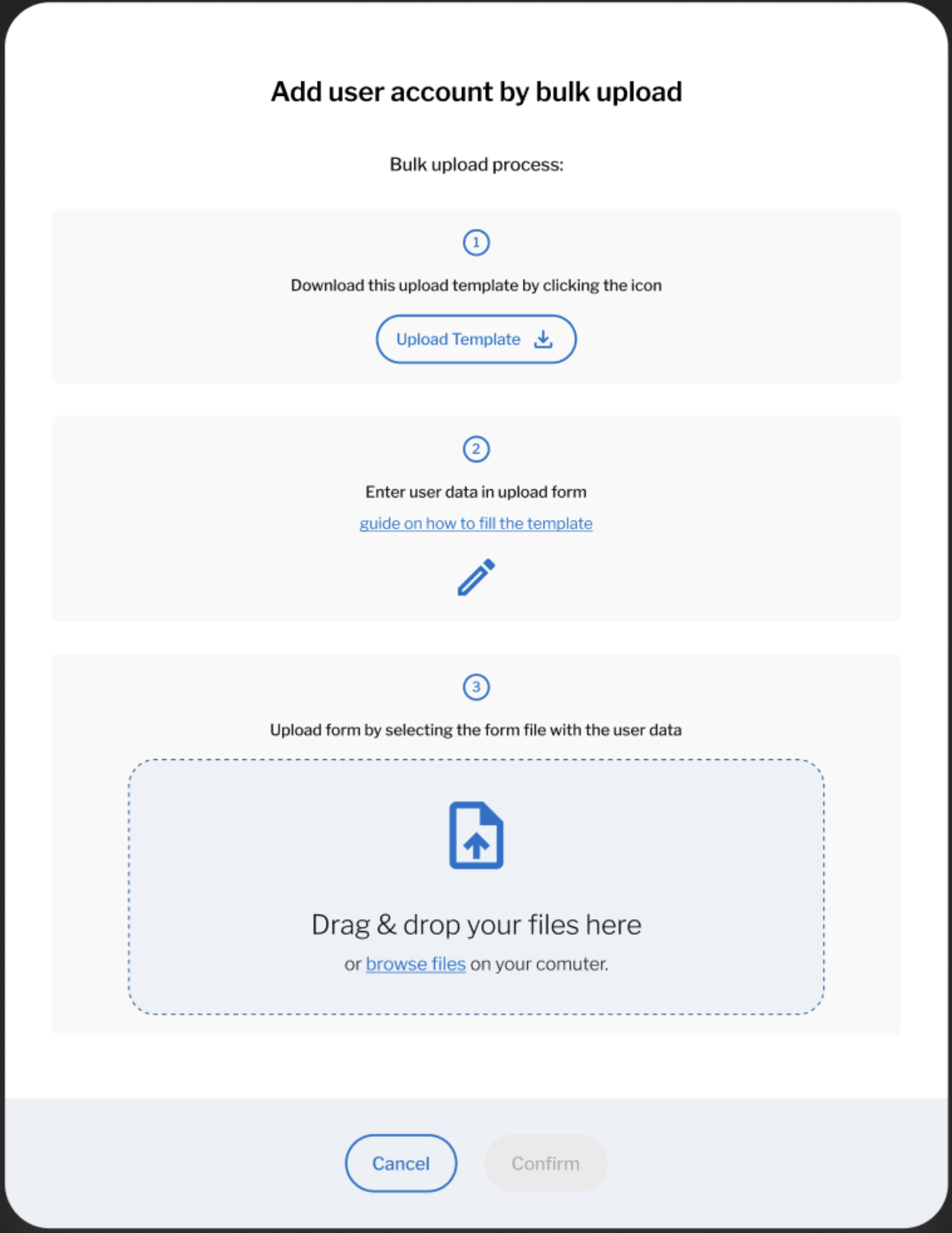
@@ -5,7 +5,7 @@ Please note that it is suggested to separate the bulk user create groups per rol
- +
+
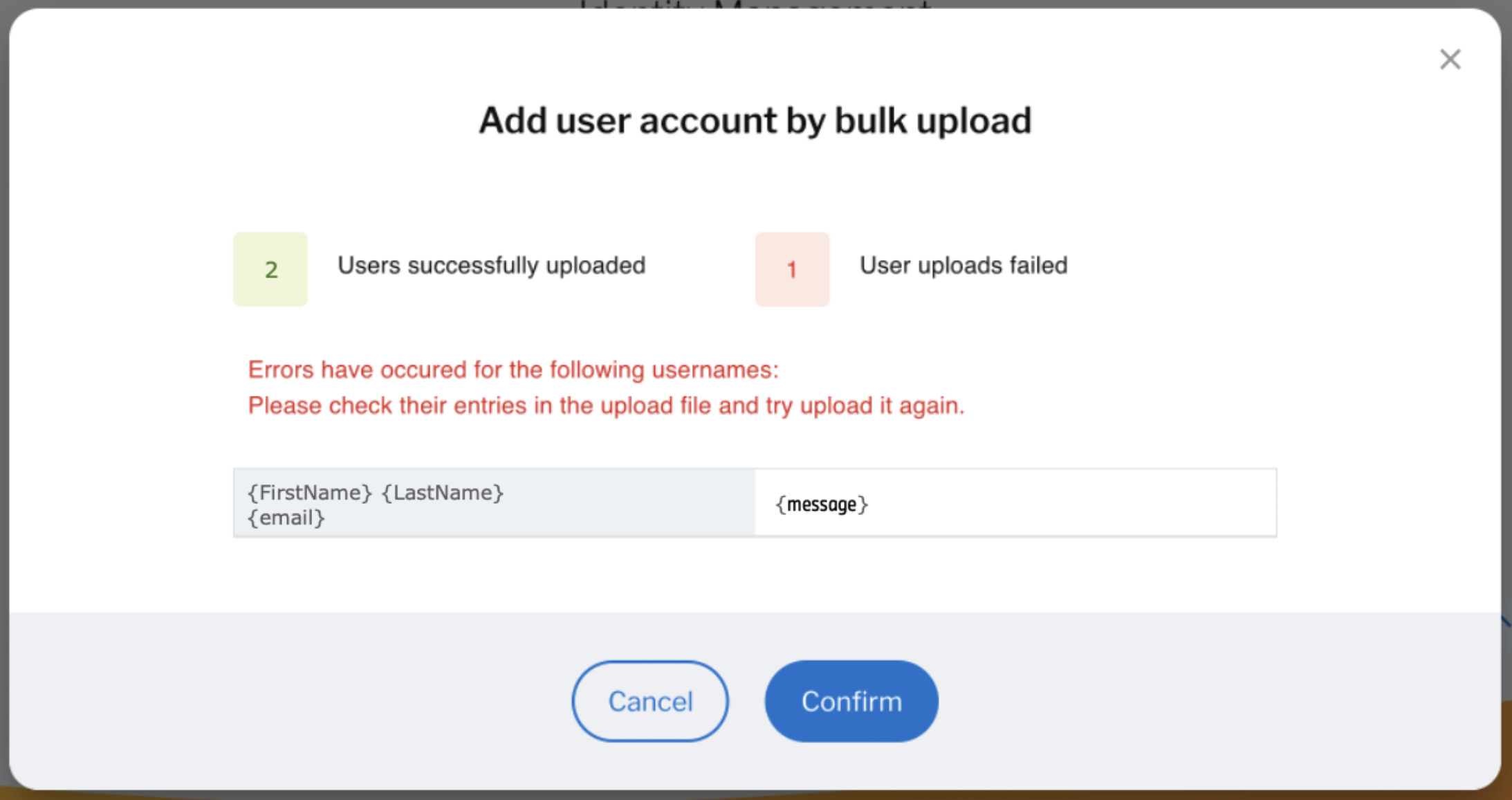
@@ -56,7 +56,7 @@ Note: if a user inside the csv file upload fails in the user account creation, t
- +
+
diff --git a/docs/04. App(s)/02. App Release Process/index.md b/docs/04. App(s)/02. App Release Process/index.md
index 0c352ae5c..7355945d3 100644
--- a/docs/04. App(s)/02. App Release Process/index.md
+++ b/docs/04. App(s)/02. App Release Process/index.md
@@ -31,7 +31,7 @@ Access the "App Overview" page via the top navigation "App Management"
- +
+
@@ -43,7 +43,7 @@ and click on
- +
+
diff --git a/docs/04. App(s)/06. App Change Process/07. Document Change.md b/docs/04. App(s)/06. App Change Process/07. Document Change.md
index d6351d2ca..578a3f2fa 100644
--- a/docs/04. App(s)/06. App Change Process/07. Document Change.md
+++ b/docs/04. App(s)/06. App Change Process/07. Document Change.md
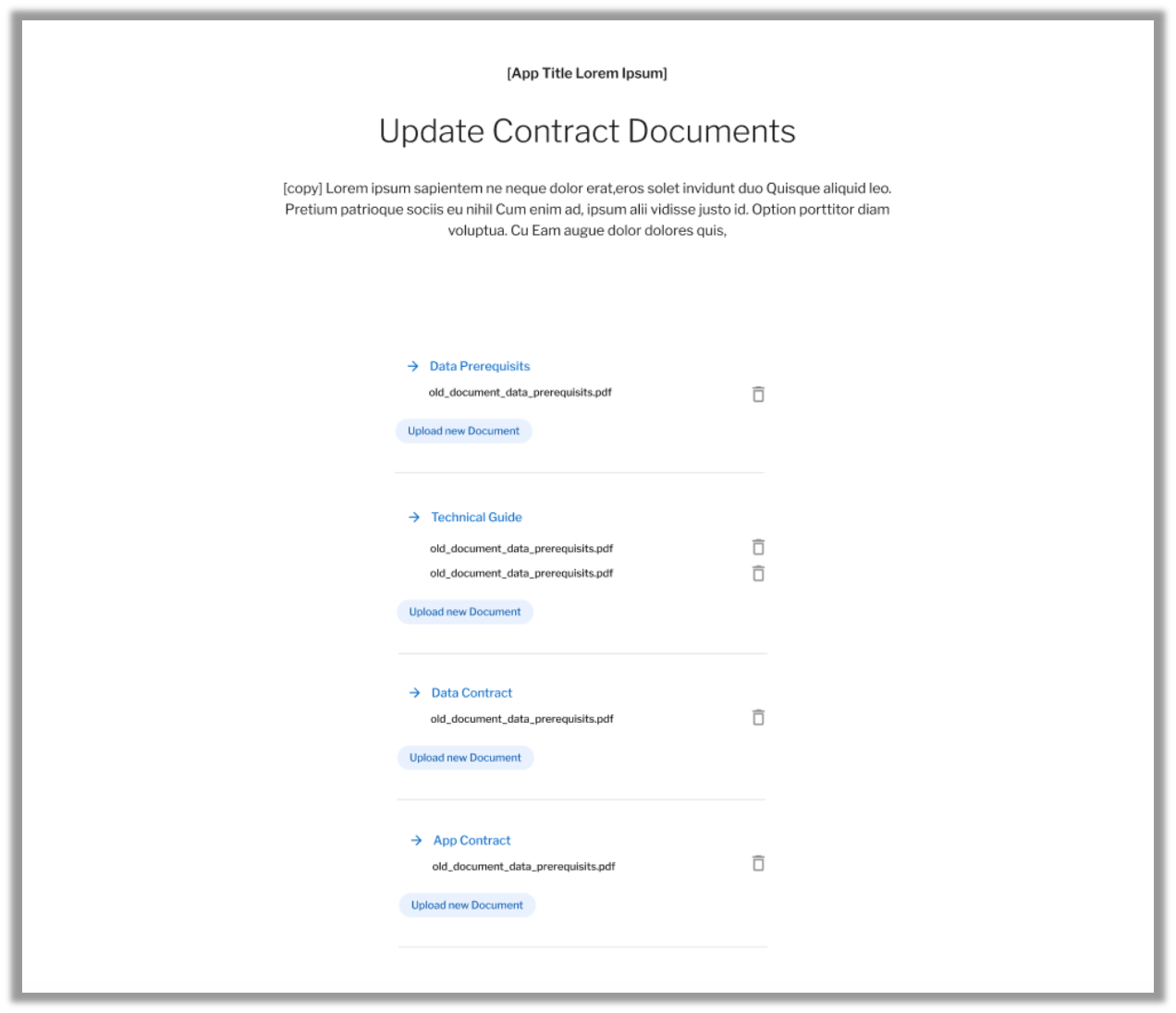
@@ -2,7 +2,7 @@
- +
+
diff --git a/docs/09. Others/12. Offer Authentication Flow.md b/docs/09. Others/12. Offer Authentication Flow.md
index f41f1d4bd..0c0a698f7 100644
--- a/docs/09. Others/12. Offer Authentication Flow.md
+++ b/docs/09. Others/12. Offer Authentication Flow.md
@@ -17,10 +17,10 @@
### Process
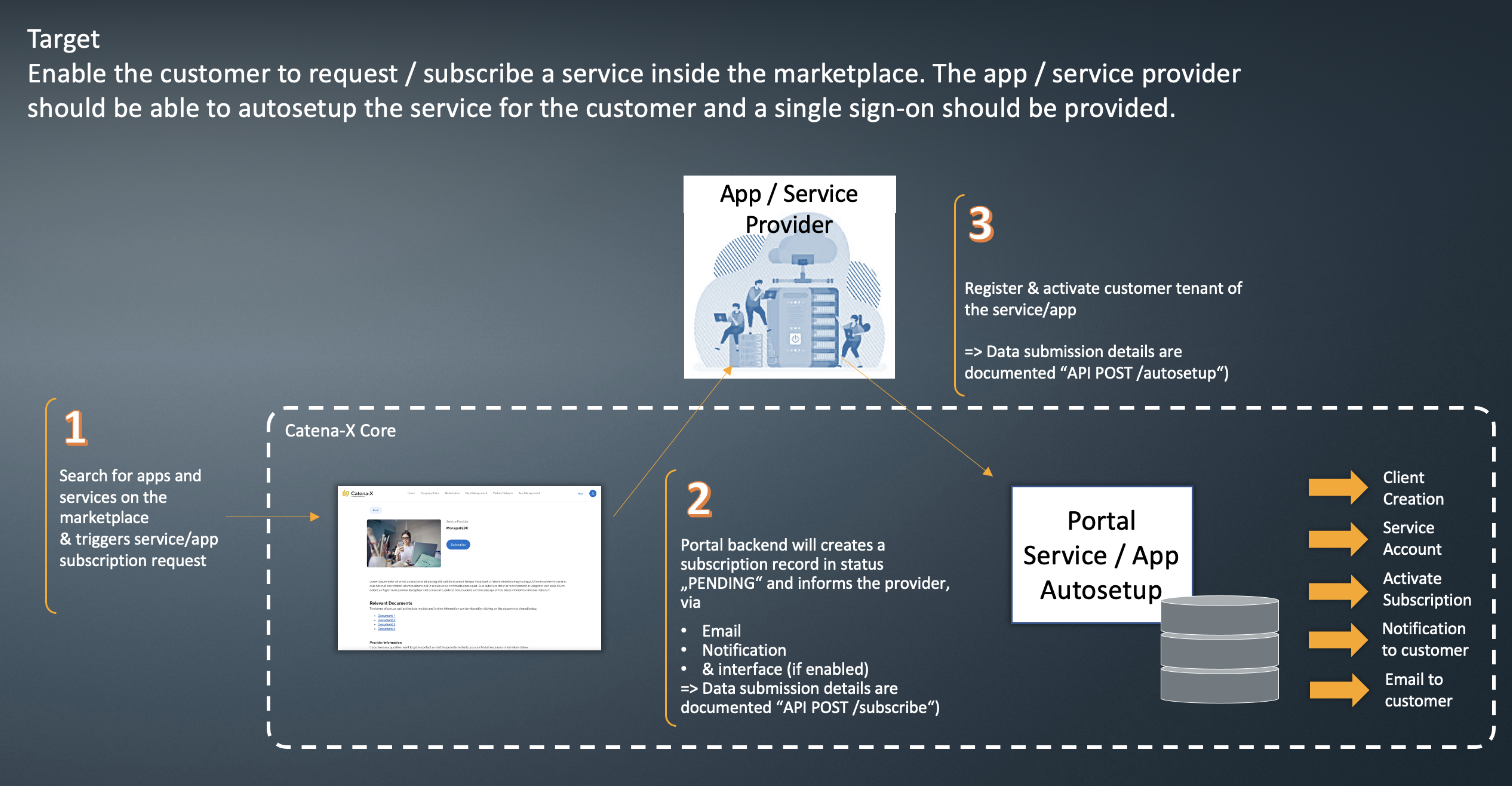
-In the description below the high level process of app/service listing; subscription; activation and configuration with authentication are stated.
+In the description below the highlevel process of app/service listing; subscription; activation and configuration with authentication are stated.
The process is relevant for App Provider, Service Provider and the App/Service Customer.
-The integration to the operator keycloak enables:
+The integration to the operator Keycloak enables:
- app provider to register the application instance (per customer)
- app provider separate app customer instances (each instance has a own client)
@@ -29,9 +29,9 @@ The integration to the operator keycloak enables:
-## High level Process
+## Highlevel Process
- +
+
diff --git a/package.json b/package.json
index e468b43d1..c22b96077 100644
--- a/package.json
+++ b/package.json
@@ -1,6 +1,6 @@
{
"name": "cx-portal-assets",
- "version": "v1.7.0-RC4",
+ "version": "v1.7.0",
"description": "Shared frontend content and static assets for the Catena-X Portal",
"main": "index.js",
"repository": "git@github.com:eclipse-tractusx/portal-assets.git",
@@ -23,8 +23,9 @@
},
"scripts": {
"build:release": "node src/documentation/Release.js ${1}",
- "build": "./scripts/build.sh",
+ "build": "yarn build:copy-legal-info && ./scripts/build.sh",
"build:legal-notice": "bash scripts/legal-notice.sh",
+ "build:copy-legal-info": "cp LICENSE NOTICE.md DEPENDENCIES SECURITY.md public/assets/notice/",
"build:sources": "zip -r portal-assets.zip src package.json yarn.lock -x '*.stories.*' -x '*.test.*' -x '*.ttf' -x '*.svg' -x '*.png' -x '*.jpg'",
"start": "concurrently \"yarn start:assets\" \"yarn start:proxy\" \"open http://localhost:3000/\"",
"start:proxy": "node src/proxy/index.cjs",
diff --git a/src/documentation/Release.js b/src/documentation/Release.js
index 5d73e09f5..beb217da8 100644
--- a/src/documentation/Release.js
+++ b/src/documentation/Release.js
@@ -20,6 +20,8 @@
import fs from 'fs'
import dirTree from 'directory-tree'
+const exclude = /\/static(\/|$)/
+
class MDHelper {
readContent(path) {
if (!fs.lstatSync(path).isFile()) return ''
@@ -39,15 +41,16 @@ class MDHelper {
extractChapterTree(tree) {
if (fs.lstatSync(tree.path).isFile())
tree.chapter = this.parseChapters(tree.path)
- else if (tree.children)
+ else if (tree.children) {
tree.children.forEach((child) => this.extractChapterTree(child))
+ }
return tree
}
}
class TreeHelper {
static readDirTree(root) {
- const tree = dirTree(root)
+ const tree = dirTree(root, { exclude })
//const tree = Transformer.tree2map({}, dirTree(root), undefined, 0, 0)
return tree
}
 +
+
 +
+
 +
+
 +
+
 +
+
 +
+
 +
+
 +
+
 +
+
 +
+
 +
+
 +
+
 +
+