The code in this repository which function is to extract the shellcode from the maldoc
In my daily analysis, I will face many maldoc. Most maldoc contain shellcode, so we have to face the problem of how to quickly extract shellcode from it and analyze its behavior. This tool solves this problem very well by combining existing analysis tools to form a tool chain. And if you want know more details of this tool, you can read this article I wrote
- python3 & javascript
- REMnux or any enviroment that include these tools (zipdump & rtfdump & oledump & oleid & msoffcrypto-crack & xorsearch & scdbg & cut-bytes)
- Windows + Office + frida (If you want to use the hook function to extract the OLE object from the RTF file)
- The docker image(g0mx/remnux-shellcode_extractor) created by myself for extracting shellcode from maldoc based on REMnux
You only need to clone this repository
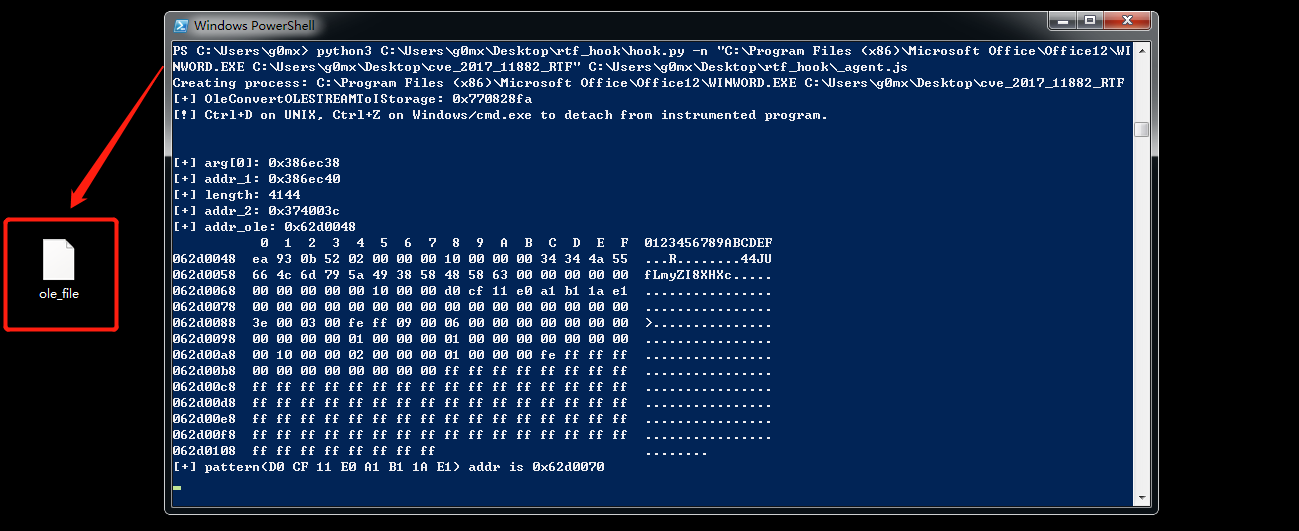
Windows + Office + frida
In the hook folder (you need modify the storage location of the OLE object which is dumped from RTF)
python3 "$(The path of hook.py)" -n "$(The path of WINWORD.exe) $(The path of RTF file)" "$(The path of hook_OLE.mjs)"REMnux or any enviroment that include these tools (zipdump & rtfdump & xorsearch & scdbg & cut-bytes) or The docker image(g0mx/remnux-shellcode_extractor) created by myself for extracting shellcode from maldoc based on REMnux
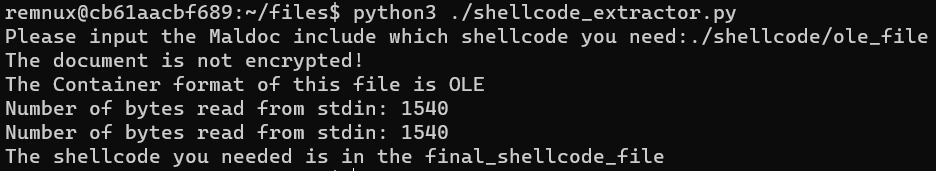
shellcode_extractor.py (you need to make sure that the tool path in the python file matches the environment you are using. At the same time you can modify the storage location of the shellcode file which is dumped from maldoc)
If you use the docker images(g0mx/remnux-shellcode_extractor), you will find the shellcode_extractor.py in the "/home/remnux"
docker run --rm -it -u remnux -v "$(The path of folder)":/home/remnux/files remnux/remnux-shellcode_extractor /bin/bash
cd /home/remnux
python3 "$(The path of shellcode_extractor.py)"- Environment is Remnux docker
- Didier Stevens 's tools and blogs
- oletools
- frida-python github
- frida's official document
- Denis O'Brien's Silver Bullet
- DarunGrim's Using Frida For Windows Reverse Engineering