Introduction | Features | Build | Contact | Disclaimer
This firmware is an alternative to Flipper Zero for ESP-32, and is always updated from the original Flipper ideas, making it the most stable alternative.
Website: https://willy-firmware.com/
We have spent many hours perfecting this code even further, and getting the most out of it.
The goal of this firmware is to be able to benefit from the same functions as the Flipper Zero but on an ESP32, which is cheaper, and easier to obtain in some countries, as well as to regularly bring out amazing updates based on what the community wants, with a real understanding of what is happening. Fixing regularly talked about bugs and expanding capabilities with exciting new features and, most importantly, ensuring the simplest user experience possible.
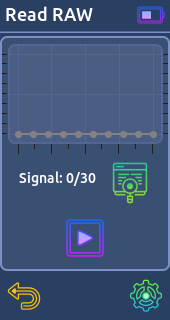
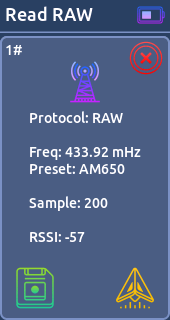
- Read RAW:
Reads and decode signals in a raw format, including signals from remotes with unknown protocols. (You can save 30 signals in the memory)
From there you can send it or save it on the sd card for use it later.
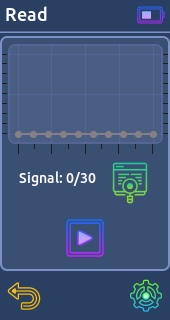
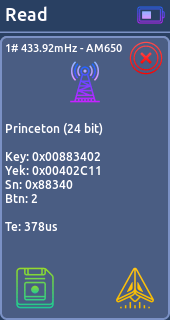
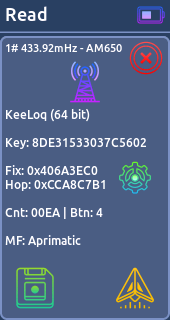
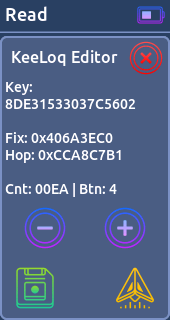
- Read:
Reads and decodes signals based on known protocols. If the protocol is static, Willy decode the signal. (You can save 30 signals in the memory)
From there you can send it or save it on the sd card for use it later.
[Supported decoders]
* Ansonic (12bit)
* BETT (18bit)
* CAME (12bit)
* CAME (18bit)
* CAME (24bit)
* CAME (25bit)
* Chamberlain (7bit)
* Chamberlain (8bit)
* Chamberlain (9bit)
* Clemsa (18bit)
* Doitrand (37bit)
* Dooya (50bit)
* FAAC SLH (64bit)
* GateTX (24bit)
* Hormann HSM (44bit)
* KeeLoq (64bit)
* Linear (10bit)
* Magellan (32bit)
* Marantec (49bit)
* Nice FLO (12bit)
* Nice FLO (24bit)
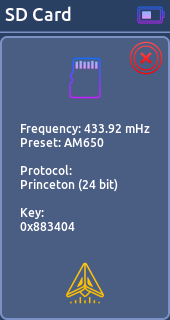
* Princeton (24bit)
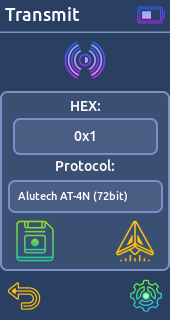
* Starline (64bit)- Transmit:
Generate and send signal based on known protocol and key.
From there you can send it or save it on the sd card for use it later.
[Supported protocols]
* Alutech AT-4N (72bit)
* Ansonic (12bit)
* BETT (18bit)
* CAME Atomo (62bit)
* CAME TWEE (54bit)
* CAME (12bit)
* CAME (18bit)
* CAME (24bit)
* CAME (25bit)
* Chamberlain (7bit)
* Chamberlain (8bit)
* Chamberlain (9bit)
* Clemsa (18bit)
* Doitrand (37bit)
* Dooya (40bit)
* Faac SLH (64bit)
* GateTX (24bit)
* Genie (64bit)
* Holtek_HT12X (12bit)
* Holtek (40bit)
* Honeywell (48bit)
* Hormann HSM (44bit)
* Hormann BiSecur (176bit)
* Intertechno_V3 (32bit)
* KeeLoq (64bit)
* KIA (61bit)
* KingGates Stylo4k (89bit)
* LinearDelta3 (8bit)
* Linear (10bit)
* Magellan (32bit)
* Marantec (49bit)
* Mastercode (36bit)
* Megacode (24bit)
* Nero Radio (56bit)
* Nero Sketch (40bit)
* Nice FLO (12bit)
* Nice FLO (24bit)
* Nice FloR-S (52bit)
* Phoenix_V2 (52bit)
* Power Smart (64bit)
* Princeton (24bit)
* Security+ 1.0 (21bit)
* Security+ 2.0 (62bit)
* SMC5326 (25bit)
* Somfy Keytis (80bit)
* Somfy Telis (56bit)
* Starline (64bit)
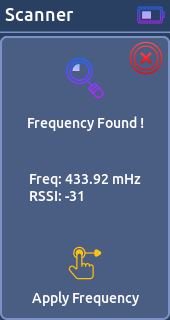
* UNILARM (25bit)- Scanner:
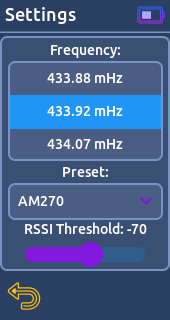
When analysing, the device scanning signals strength (RSSI) at all the frequencies available in frequency configuration. Then displays the frequency with the highest RSSI value, with signal strength higher than than configured.
From there you can apply the found frequency for the general settings.
- Jammer:
This function generates noise. Be careful when using this feature and ensure you follow the laws in your country. This may cause interference and potentially disrupt the proper operation of some devices.
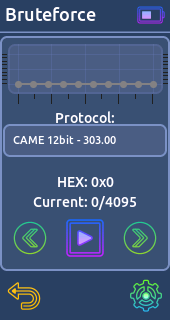
- Bruteforce:
If you know the protocol used for example by the garage door it's possible to generate all the codes and send them with the Willy.
[Supported protocols]
* CAME (12bit) - 303.87 mHz
* CAME (12bit) - 307.80 mHz
* CAME (12bit) - 315.00 mHz
* CAME (12bit) - 330.00 mHz
* CAME (12bit) - 433.92 mHz
* CAME (12bit) - 868.35 mHz
* Nice FLO (12bit) - 433.92 mHz
* Nice FLO (12bit) - 868.35 mHz
* Ansonic (12bit) - 433.07 mHz
* Ansonic (12bit) - 433.92 mHz
* Ansonic (12bit) - 434.07 mHz
* Holtek_HT12X (12bit) FM - 433.92 mHz (TE: 204μs)
* Holtek_HT12X (12bit) AM - 433.92 mHz (TE: 433μs)
* Holtek_HT12X (12bit) AM - 315.00 mHz (TE: 433μs)
* Holtek_HT12X (12bit) AM - 868.35 mHz (TE: 433μs)
* Holtek_HT12X (12bit) AM - 915.00 mHz (TE: 433μs)
* Chamberlain (9bit) - 300.00 mHz
* Chamberlain (9bit) - 315.00 mHz
* Chamberlain (9bit) - 390.00 mHz
* Chamberlain (9bit) - 433.92 mHz
* Chamberlain (8bit) - 300.00 mHz
* Chamberlain (8bit) - 315.00 mHz
* Chamberlain (8bit) - 390.00 mHz
* Chamberlain (7bit) - 300.00 mHz
* Chamberlain (7bit) - 315.00 mHz
* Chamberlain (7bit) - 390.00 mHz
* Linear (10bit) - 300.00 mHz
* Linear (10bit) - 310.00 mHz
* Linear Delta 3 (8bit) - 310.00 mHz
* UNILARM (25bit) - 330.00 mHz (TE: 209μs) // Note: Only dip switch combinations, not full 25bit bruteforce
* UNILARM (25bit) - 433.92 mHz (TE: 209μs) // Note: Only dip switch combinations, not full 25bit bruteforce
* SMC5326 (25bit) - 330.00 mHz (TE: 320μs) // Note: Only dip switch combinations, not full 25bit bruteforce
* SMC5326 (25bit) - 433.92 mHz (TE: 320μs) // Note: Only dip switch combinations, not full 25bit bruteforce
* Princeton (24bit) - 315.00 mHz (TE: 286μs) // Note: Only for 8 dip switch remote, not full 24bit bruteforce
* Princeton (24bit) - 330.00 mHz (TE: 286μs) // Note: Only for 8 dip switch remote, not full 24bit bruteforce
* Princeton (24bit) - 390.00 mHz (TE: 286μs) // Note: Only for 8 dip switch remote, not full 24bit bruteforce
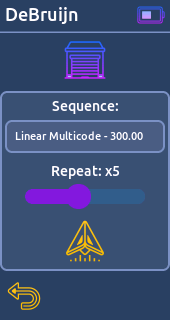
* Princeton (24bit) - 433.92 mHz (TE: 286μs) // Note: Only for 8 dip switch remote, not full 24bit bruteforce- DeBruijn:
Generate and send DeBruijn sequence for predefined garage door models.
[Supported sequence]
* Linear Multicode - 300.00 mHz
* Linear Multicode - 310.00 mHz
* Linear Multicode - 390.00 mHz
* Linear Multicode - 433.92 mHz
* Stanley Multicode - 300.00 mHz
* Stanley Multicode - 310.00 mHz
* Stanley Multicode - 390.00 mHz
* Stanley Multicode - 433.92 mHz
* Charmberlain - 300.00 mHz
* Charmberlain - 310.00 mHz
* Charmberlain - 390.00 mHz
* Charmberlain - 433.92 mHz
* Linear MooreMatic - 300.00 mHz
* Linear MooreMatic - 310.00 mHz
* Linear MooreMatic - 390.00 mHz
* Linear MooreMatic - 433.92 mHzFrom original Samy Kamkar Open Sesame
- Tesla:
Generate and send open charge door signal for Tesla.
[Supported region]
* EU - 433.92 mHz
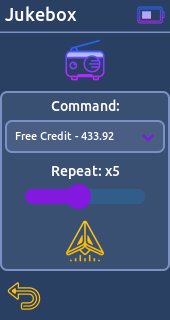
* US - 315.00 mHz- Jukebox:
Generate and send command for jukeboxes commonly found in bars.
[Supported command]
* Free Credit - 433.92 mHz
* Pause Song - 433.92 mHz
* Skip Song - 433.92 mHz
* Volume UP - 433.92 mHz
* Volume DOWN - 433.92 mHz
* Power OFF - 433.92 mHz
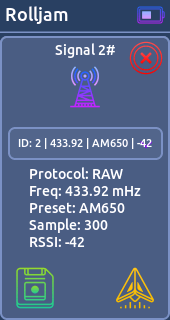
* Lock Queue - 433.92 mHz- Rolljam:
This function is a proof of concept.
RollJam is a method of capturing a rolling code key transmission by simultaneously intercepting the transmission and jamming the receivers window with another device; giving the attacker a valid rolling code for re-transmission.
You need two devices to perform this P.O.C successfully.
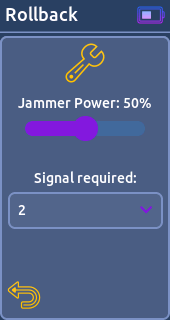
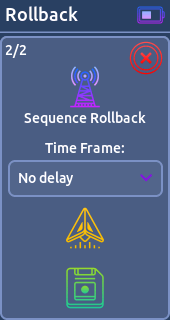
- Rollback:
This function is a proof of concept.
Rollback is a vulnerability found mostly in Honda vehicles. By capturing X valid unlock key fob signals, it allows remote attackers to perform unlock operations and force a resynchronization; giving the attacker the ability to unlock indefinitely.
You need two devices to perform this P.O.C successfully.

- Saved File:
Let's you to view the contents of your SD card and allows you to view and transmit your files.
[Supported protocols]
* RAW Data
* Alutech AT-4N (72bit)
* Ansonic (12bit)
* BETT (18bit)
* CAME Atomo (62bit)
* CAME TWEE (54bit)
* CAME (12bit)
* CAME (18bit)
* CAME (24bit)
* CAME (25bit)
* Chamberlain (7bit)
* Chamberlain (8bit)
* Chamberlain (9bit)
* Clemsa (18bit)
* Doitrand (37bit)
* Dooya (40bit)
* Faac SLH (64bit)
* GateTX (24bit)
* Genie (64bit)
* Holtek_HT12X (12bit)
* Holtek (40bit)
* Honeywell (48bit)
* Hormann HSM (44bit)
* Intertechno_V3 (32bit)
* KeeLoq (64bit)
* KIA (61bit)
* KingGates Stylo4k (89bit)
* LinearDelta3 (8bit)
* Linear (10bit)
* Magellan (32bit)
* Marantec (49bit)
* Mastercode (36bit)
* Megacode (24bit)
* Nero Radio (56bit)
* Nero Sketch (40bit)
* Nice FLO (12bit)
* Nice FLO (24bit)
* Nice FloR-S (52bit)
* Phoenix_V2 (52bit)
* Power Smart (64bit)
* Princeton (24bit)
* Security+ 1.0 (21bit)
* Security+ 2.0 (62bit)
* SMC5326 (25bit)
* Somfy Keytis (80bit)
* Somfy Telis (56bit)
* Starline (64bit)
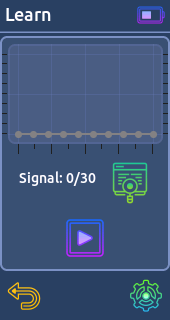
* UNILARM (25bit)- Learn:
Point the LED of the remote at the IR receiver and just press the button which you want to capture. (You can save 30 signals in the memory)
From there you can send it or save it on the sd card for use it later.
- Remote:
Just a universal remote control for TVs, AUdio, Projectors, Fans, etc.. Works with a database defined in a file, require an SD card.
- Tv-B-Gone:
Just a universal remote control for TVs, works with the public TV-B-Gone database, does not require an SD card.
[Supported region]
* EU - 139 signals
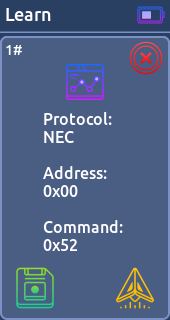
* NA - 139 signals- Saved File:
Let's you to view the contents of /SD Card/infrared/ (the default place to save your remotes) and allows you to transmit it.
[Supported protocols]
* RAW
* NEC
* NECext
* NEC42
* NEC42ext
* Kaseikyo
* RCA
* RC5X
* RC5
* RC6
* Samsung32
* SIRC
* SIRC15
* SIRC20Q: My universal remote doesn't work here or doesn't work there or I want to control this or that but it's not in the Universal remotes and I don't have a remote for it
A: Use the IRDB. It contains thousands of remotes sorted by type (AC, TV, Fan..) and then by name (Samsung, Logitech..). Here is a link just copy the contents to /SD Card/infrared (I recommend using a SD card reader for it.)
Q: I want to write my own .ir files, how do I do that?
A: This: IRDB Never used it myself but if you want to write your own .ir files, you can do your own research on the usage of the formats and idk what not. You should be good using irdb though, but it's always nice to have a few contributors :)
- BLE Spammer:
This function is designed to flood Bluetooth Low Energy (BLE) devices with connection requests or packets. It can be utilized for testing the resilience and security of BLE devices, including those running on Apple (iOS) and Android platforms.
[Supported payloads]
* IOS 17 Lockup Crash
* Apple Action Modal
* Apple Device Popup
* Android Device Connect
* Samsung Buds Popup
* Samsung Watch Pair
* Windows Device Found
* BT Settings Flood- BLE Scanner:
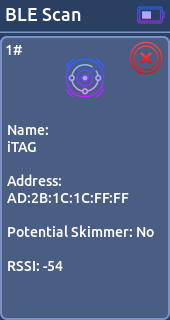
This feature is used to discover and monitor nearby Bluetooth Low Energy devices. It works by searching for advertising packets that BLE devices periodically broadcast to announce their presence.
For each Bluetooth device found, the following information is displayed:
- Name
- MAC
- Potential Skimmer (https://learn.sparkfun.com/tutorials/gas-pump-skimmers/all)
- RSSI
- SSID Spammer:
This attack is a type of wireless network attack where an attacker floods a target area with fake SSID broadcast frames. The device sends out a large number of beacon frames, each containing a different fake SSID, with the intention of overwhelming nearby devices and networks.
[Supported payloads]
* Default
* Rick Roll
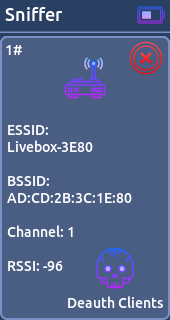
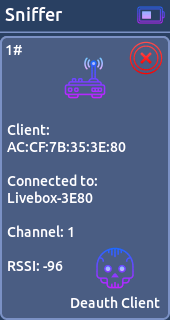
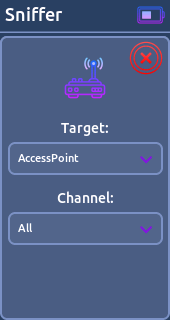
* Random- Sniffer:
This feature is used to scan for WiFi networks and clients.
From here you have the possibility to start a deauth attack on a access point or particular station.
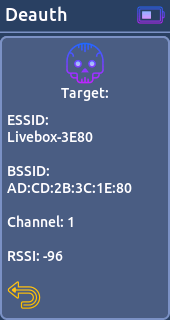
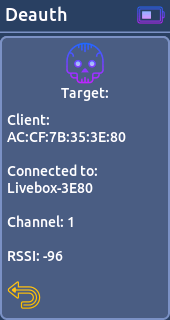
- Deauth:
This feature is used to disconnect devices from their WiFi network by sending deauth packets (deauthentication attack).
[Supported target]
* Access Point
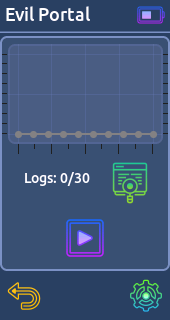
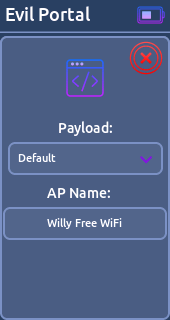
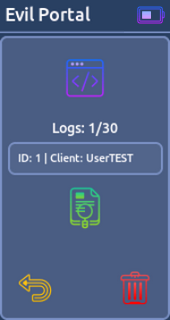
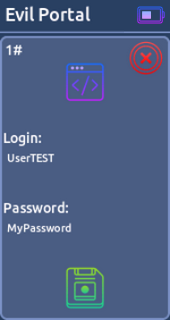
* Station- Evil Portal:
This function will turn your device into an open access point. When users try to connect to this access point they will be served a fake login screen. User data are sent to the Willy.
Note: Place your custom html files into /SD Card/evilportal/
Q: ESP32 Limitations ?
A: The ESP32 access point will not have internet access while hosting the portal, as a result there cannot be any requests for stylesheets or javascript such as CDNs for bootstrap and JQuery.
All HTML/CSS/JS must be in a single HTML file. This is due to the fact that the index.html kept in the memory of the esp32.
There is a 20k character limit for each HTML file.
The form data must be sent to the
/getendpoint as a GET request with the paramspassword. You can put any information you want in these two fields. For example thePlease check the examples to get an idea of what this has to look like.
- About:
Show information about the device.
- Sleep Mode:
You can turn off the device with the physical button located under the screen at the bottom left.
- Color:
Recolor all firmware icons and save the choice in memory.
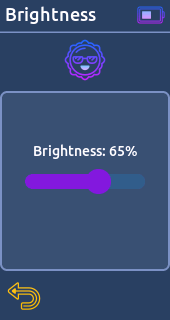
- Brightness:
Adjust the display brightness and save the choice in memory.
- PIN Code:
You can configure a 4-digit PIN code to secure the device boot.
Default PIN:0000
- Reset Device:
You can reset the device if you want to return to the original icons.
Please note this also resets the PIN code to0000and disable the secure boot.
First, you need a board, select the cheapest link for you:
Lilygo (China warehouse)
Lilygo (Germany warehouse)
Lilygo (US warehouse)
Aliexpress
There are several methods to build Willy, you can build him in DIY ways, or buy a Willy shield.
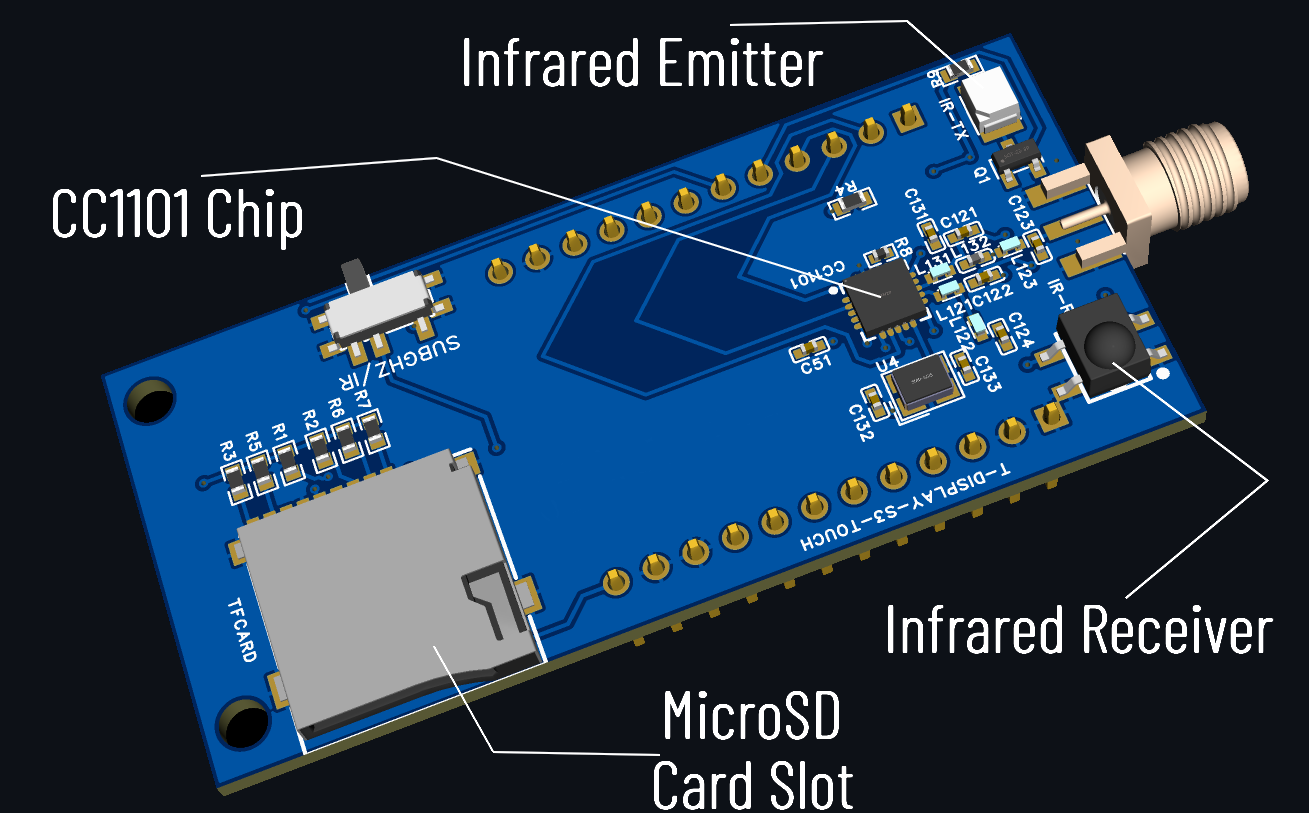
D.I.Y Shield
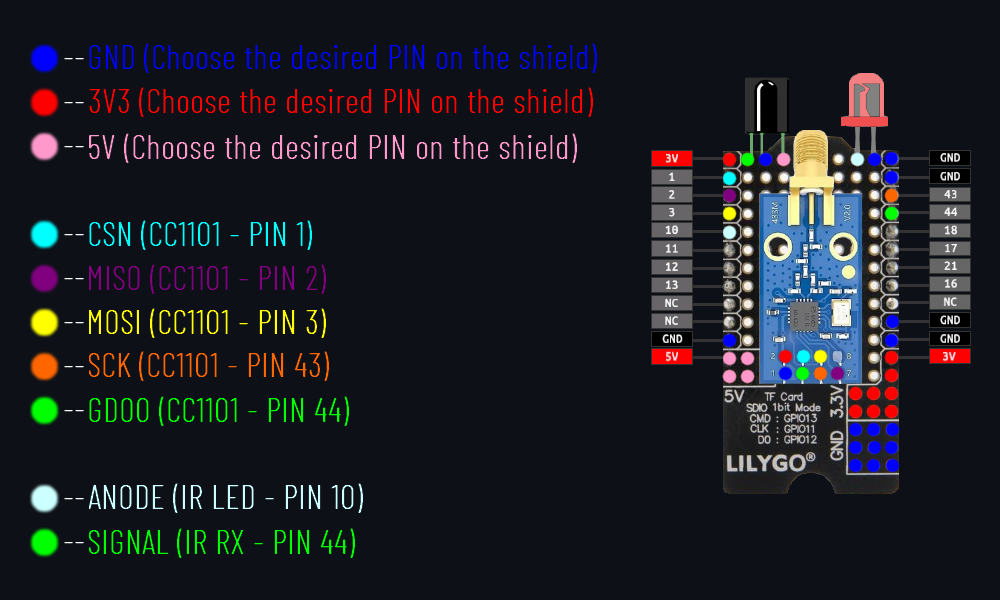
- 1x TF Shield:
- Lilygo : T-Display TF Shied (Female PIN Version [H610]) - https://www.lilygo.cc/products/t-display-tf-shied?variant=42729797025973
or
- Aliexpress : T-Display TF Shied (Female PIN Version) - https://www.aliexpress.us/item/3256804956138540.html
- 1x CC1101 V2.0 Module:
- Aliexpress : https://www.aliexpress.us/item/2251832873028557.html
- 1x Infrared Receiver TSOP4838 ( or any IR receiver model with same specs ):
- Aliexpress : https://www.aliexpress.us/item/1005004481948853.html
- 1x Infrared LED TSAL6400 ( or any IR LED model with same specs ):
- Aliexpress : https://www.aliexpress.us/item/32670031000.html
- 1x Transistor 2N4401 ( or any transistor model with same specs )(Optional):
- Aliexpress : https://www.aliexpress.us/item/1005005484591463.html
- Contact me on discord for more information
Website: https://willy-firmware.com/
This device designed specifically for educational purposes. this device have been carefully developed to offer a hands-on experience in the field of cybersecurity and penetration testing. As a responsible provider, I would like to emphasize that any illegal use of this device is strictly prohibited.
It is crucial to acknowledge that using this device for any unauthorized activities, such as hacking or attempting to access sensitive information without proper authorization, is deemed illegal and unethical. I strongly discourage engaging in any activities that may cause harm, compromise security, or infringe upon others' privacy rights.
By accessing and utilizing this device, users take complete responsibility for their actions and the consequences that may arise from them. I expect users to act responsibly, adhere to ethical guidelines, and ensure that their activities remain within the boundaries of the law and ethical norms.
Remember, this device are aimed at promoting knowledge, improving cybersecurity skills, and raising awareness about the potential vulnerabilities present in infrastructures. I encourage you to explore this device, learn from them, and embrace the opportunity to enhance your understanding in a controlled and legal environment.
Thank you for your cooperation and commitment to responsible usage. Together, let us foster a secure and ethical cyberspace.