railtail is a HTTP/TCP proxy for Railway workloads connecting to Tailscale nodes. It listens on a local address and forwards traffic it receives on the local address to a target Tailscale node address.
📣 This is a workaround until there are full VMs available in Railway. Please upvote the thread if you want this feature!
-
Install and setup Tailscale on the machine you want to connect to. If you're using Tailscale as a subnet router, ensure you advertise the correct routes and approve the subnets in the Tailscale admin console.
-
Deploy this template to Railway:
-
In services that need to connect to the Tailscale node, connect to your railtail service using the
RAILWAY_PRIVATE_DOMAINandLISTEN_PORTvariables. For example:MY_PRIVATE_TAILSCALE_SERVICE="http://{{railtail.RAILWAY_PRIVATE_DOMAIN}}:${{railtail.LISTEN_PORT}}"
Look at the Examples section for provider-specific examples.
railtail will forward TCP connections if you provide a TARGET_ADDR without
a http:// or https:// scheme. If you want railtail to act as an HTTP
proxy, ensure you have a http:// or https:// in your TARGET_ADDR.
| Environment Variable | CLI Argument | Description |
|---|---|---|
TARGET_ADDR |
-target-addr |
Required. Address of the Tailscale node to send traffic to. |
LISTEN_PORT |
-listen-port |
Required. Port to listen on. |
TS_HOSTNAME |
-ts-hostname |
Required. Hostname to use for Tailscale. |
TS_AUTH_KEY |
N/A | Required. Tailscale auth key. Must be set in environment. |
TS_STATEDIR_PATH |
N/A | Optional. Tailscale state dir. Defaults to /tmp/railtail. |
CLI arguments will take precedence over environment variables.
This was created to work around userspace networking restrictions. Dialing a Tailscale node from a container requires you to do it over Tailscale's local SOCKS5/HTTP proxy, which is not always ergonomical especially if you're connecting to databases or other services with minimal support for SOCKS5 (e.g. db connections from an application).
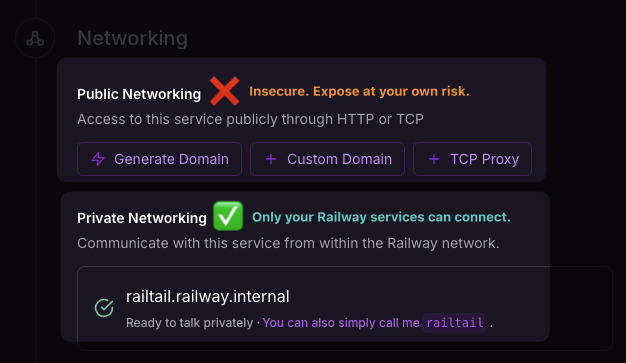
railtail is designed to be run as a separate service in Railway that you connect to over Railway's Private Network.
⚠️ Warning: Do not expose this service on Railway publicly!This service is intended to be used via Railway's Private Network only.
-
Configure Tailscale on an EC2 instance in the same VPC as your RDS instance:
# In EC2 curl -fsSL https://tailscale.com/install.sh | sh # Enable IP forwarding echo 'net.ipv4.ip_forward = 1' | sudo tee -a /etc/sysctl.d/99-tailscale.conf echo 'net.ipv6.conf.all.forwarding = 1' | sudo tee -a /etc/sysctl.d/99-tailscale.conf sudo sysctl -p /etc/sysctl.d/99-tailscale.conf # Start Tailscale. Follow instructions to authenticate the node if needed, # and make sure you approve the subnet routes in the Tailscale admin console sudo tailscale up --reset --advertise-routes=172.31.0.0/16
-
Deploy railtail to Railway by clicking the button below:
-
Use your new railtail service's Private Domain to connect to your RDS instance:
DATABASE_URL="postgresql://u:p@${{railtail.RAILWAY_PRIVATE_DOMAIN}}:${{railtail.LISTEN_PORT}}/dbname"