-
Notifications
You must be signed in to change notification settings - Fork 103
wireguard
hev edited this page Apr 13, 2024
·
2 revisions
通过NATMap在运营商的NAT-1上打洞,分配私网IPv4的宽带可以部署WireGuard服务,并能像具有公网IP一样在其它外部主机上访问。
WG1 NATMap(on gateway) WG2
Internal: (192.168.0.2:6000) <----> (100.65.11.55:6000)
^
|
v
External: (112.24.0.23:6348) <------------>
- WG1: WG1运行在内网主机,侦听在192.168.0.2:6000端口。
- NATMap: NATMap运行在网关,侦听在100.65.11.55:6000端口,打洞使公网地址112.24.0.23:6348映射至100.65.11.55:6000,同时又将100.65.11.55:6000映射至192.168.0.2:6000。从外部访问112.24.0.23:6348等同于访问192.168.0.2:6000。
- WG2: WG2运行在外部主机上,通过NATMap打洞获得的公网地址112.24.0.23:6348访问WG1。
IP4P方法利用DNS的AAAA类型记录,将公网IPv4地址和端口同时记录在域名解析记录中。WG客户端识别到IP4P类型的域名解析结果后,则能获得实时的公网IPv4地址和端口。IP4P的方法要求客户端增加支持,WireGuard Android目前已有支持IP4P的衍生项目。
示例采用Linux内核的WireGuard实现:
ip link add dev wg0 type wireguard
ip address add dev wg0 192.168.2.1/24
wg set wg0 listen-port 6000 private-key /path/to/private-key peer m6zIxkcWAcTJpbwB9evp/f73S1kOrDKTrKmJJTCVLFw= allowed-ips 0.0.0.0/0
ip link set up dev wg0更多参考:https://www.wireguard.com/quickstart
创建文件/usr/bin/ddns写入如下内容,并补充必要的变量值:
#!/bin/sh
ZONE=''
RECORD=''
EMAIL=''
AUTH=''
DOMAIN=''
IP4P=${3}
while true; do
curl -X PUT "https://api.cloudflare.com/client/v4/zones/${ZONE}/dns_records/${RECORD}" \
-H "X-Auth-Email: ${EMAIL}" \
-H "Authorization: Bearer ${AUTH}" \
-H "Content-Type:application/json" \
--data "{\"type\":\"AAAA\",\"name\":\"${DOMAIN}\",\"content\":\"${IP4P}\",\"ttl\":60,\"proxied\":false}" > /dev/null 2> /dev/null
if [ $? -eq 0 ]; then
break
fi
done再增加可执行权限:
chmod +x /usr/bin/ddns从软件仓库安装natmap和luci-app-natmap软件包。

或命令行
opkg install natmap luci-app-natmap从项目发布页下载匹配的版本: https://github.com/heiher/natmap/releases

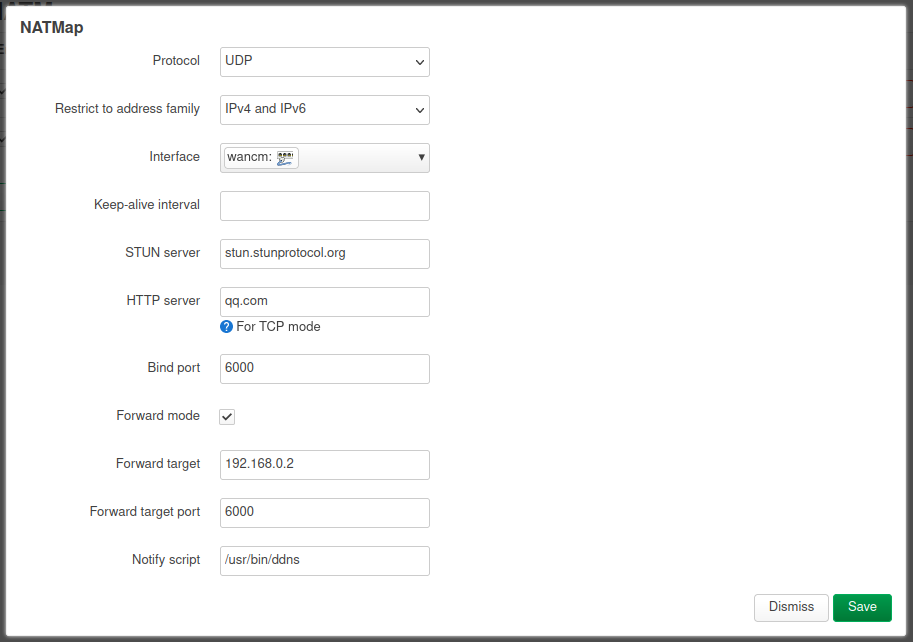
- Protocol: UDP
- Interface: wan
- STUN server: turn.cloudflare.com
- HTTP server: qq.com
- Bind port: 6000
- Forward mode: ☑
- Forward target: 192.168.0.2
- Forward target port: 6000
- Notify script: /usr/bin/ddns



将如下内容写入 /etc/rc.local 开机自动启动,或创建其它服务管理配置:
natmap -d -u -i pppoe-wan -s turn.cloudflare.com -b 6000 -t 192.168.0.2 -p 6000 -e /usr/bin/ddns防火墙放行UDP协议目的端口6000的入站。
比如域名为: wg.hev.cc
nslookup wg.hev.cc当配置正确且运行正常时,应当能够解析类似如下结果:
Server: 192.168.0.1
Address: 192.168.0.1#53
Non-authoritative answer:
Name: wg.hev.cc
Address: 2001::18cc:7018:0017
从衍生项目发布页下载匹配的版本: https://github.com/heiher/wireguard-android/releases

- 打开WireGuard Android,点击「+」。

- 手工创建如下配置:

Interface:
- Name: wg0
- Private key: aD4SfpM2APKsfAR5zfLBmzblZVWnESe0GD+CEdXooXU=
- Public key: m6zIxkcWAcTJpbwB9evp/f73S1kOrDKTrKmJJTCVLFw=
- Addresses: 192.168.2.2/24
Peer:
- Public key: lkc17GQJmqMILdh4jnvOalN8dSNIJY2EXDjuZWFssxc=
- Endpoint: wg.hev.cc:0
- Allowed IPs: 0.0.0.0/0