- faster time to market
- scalability and flexibility
- cost savings
- better collaboration
- advanced security
- data loss prevention
- failover and caching mechanisms
- wide range of services
- risk of vendor lock-in
- less control over underlying cloud infra
- concerns about security risks like data privacy and online threats
- integration complexity with exisiting systems
- unforseen costs
- AWS RDS : This is a relational database service offered by aws which operates on databases that use SQL ( for eg: MySQL, PostgreSQL, MariaDB, Aurora). This services focuses on automatically backing up, dupicating, and auto scaling of the data.
- Aurora : This is a fully functional database that is compatible with MySQL and PostgreSQL, and can be run on RDS. This is a fully managed DB that automates read replica and write replicas creation, it supports auto scaling and offers an automatic failover mechanism.
- AWS Codebuild : This is a Continuous Integration platform that compiles the code, runs tests and produces production ready software packages. (like Jenkins)
- AWS CodePipeline : This is a Continuous Deployment service that automates the build, tests and deployment of code. Code can be pipelined to either test or production environment.
- Block Storage : This is used to store data in fixed size blocks that don't follow any hierarchial or directory like structure. These are usually used in SANs (Storage Area Networks) and allow multiple servers to access the blocks at the same time (shared access) as if the blocks are a part of a that server's own hard disk. Each block has a unique address that allows the server to access and (or) modify it.
- Object Storage : This type of storage divides a file into multiple objects (having variable sizes) with each having a unique identifier. Each objects consist of data, along with metadata. They are stored in flat namespaces and are highly scalable.
- S3 : Scalable, Object Storage
- EBS : For having block storage associated with EC2 instances. offers low latency and cost effectiveness.
- EFS: Offers file storage for EC2.
- S3 Glacier : Low cost cloud data archival service (like a data vault) that offfers fast retrieval, highly secure and durable.
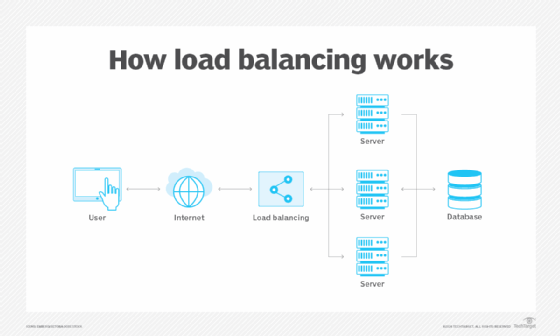
Load balancers are given the task of efficienctly dividing the network traffic or resources across multiple servers that are part of that network. This ensures that all the servers remain active (unless there’s some hardware issue).
Security groups : A security group controls the traffic that is allowed to reach and leave the resources that it is associated with. For example, after you associate a security group with an EC2 instance, it controls the inbound and outbound traffic for the instance. When you create a VPC, it comes with a default security group. (acts as a firewall)
VPC : own isolated private environment in a public cloud, which contains all the services offered by the vendor. Domain Name Service - Route 53
public-subnet : Subnets which have direct access to the internet, they can receive inbound connections from the internet. private-subnet : Subnets which don't have direct internet access, i.e. they cannot receive inbound conns from the internet. However, they may initiate internet conns through NAT Gateways.
- key pair : kind of like a password (public key is username; private key is password)
- PPK (PuTTY Private Key) and PEM (Privacy Enhanced Mail) are two file formats that are commonly used for SSH and SSL/TLS connections. While PPK files are primarily used with PuTTY on Windows, PEM files are more widely supported and can be used with various tools and platforms
- Your load balancer routes requests to the targets in a target group and performs health checks on the targets.
- LB routes traffic to target group then traffic group routes traffic to the back end ec2 instances or IP addresses etc
htop-
currently 0
-
making instance count to a high number
seq 999999999999999999999 > /dev/null &- going to the DNS name and reloading will take you to diff targets(3)
- this is round robin at work
AWS CLI : The AWS Command Line Interface (AWS CLI) is a unified tool to manage your AWS services. With just one tool to download and configure, you can control multiple AWS services from the command line and automate them through scripts.
- BOTO library in python
sudo snap install aws-cliaws configure- in security credentials , before creating access key copy and paste PU , PrK and fill location and format in terminal
- give user access
- after creating instance
aws ec2 describe-instances- docker image to create art load
- pods : Pods are the smallest deployable units of computing that you can create and manage in Kubernetes. A Pod (as in a pod of whales or pea pod) is a group of one or more containers, with shared storage and network resources, and a specification for how to run the containers.
- daemon sets : works on nodes where pods are running , can manage all your agents eg if we are runninf 5 ec2 instances behind the k8s cluster then we can run 1 daemon set and that daemon set wil take care of all the agents
- cloud based IDE (vscode , pycharm etc)
- provides IDE on browsers
- after confiugring aws cli on cloud 9 (scroll up)
- configure EKS ctl and kubectl link for installation