Copyright Amazon.com, Inc. or its affiliates. All Rights Reserved. SPDX-License-Identifier: CC-BY-SA-4.0
- Overview of the SDCA Deployment Process
- CloudFormation Implementation Instructions
- Easy Setup Architecture Details
- Common Prerequisites Architecture Details
- Config in Management Account Architecture Details
- Security Hub Architecture Details
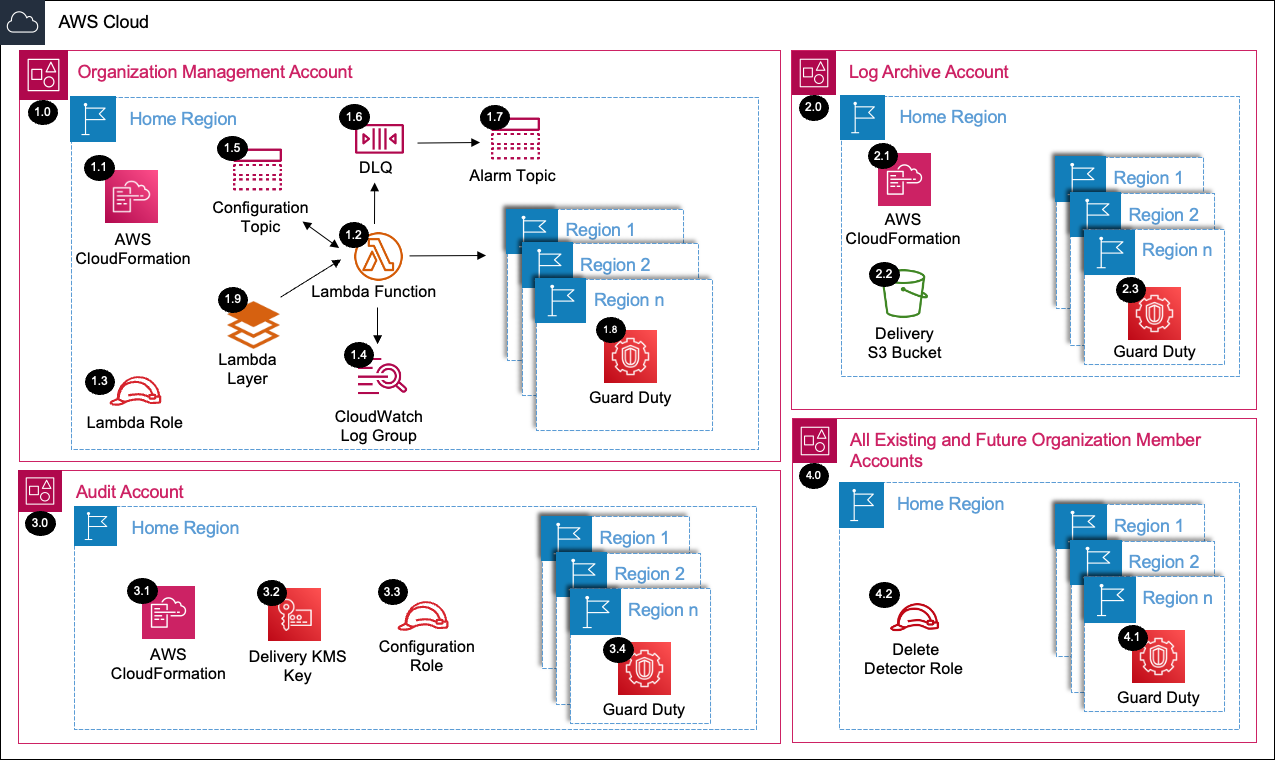
- GuardDuty Architecture Details
- Shield Advanced Architecture Details
The SDCA provides a consolidated method to install key security services in your environment with a single CloudFormation template. The SDCA leverages the solutions developed as a part of the AWS SRA code library to deliver this in alignment with the AWS Cloud Adoption Framework, Well-Architected Framework, and Security Best Practices.
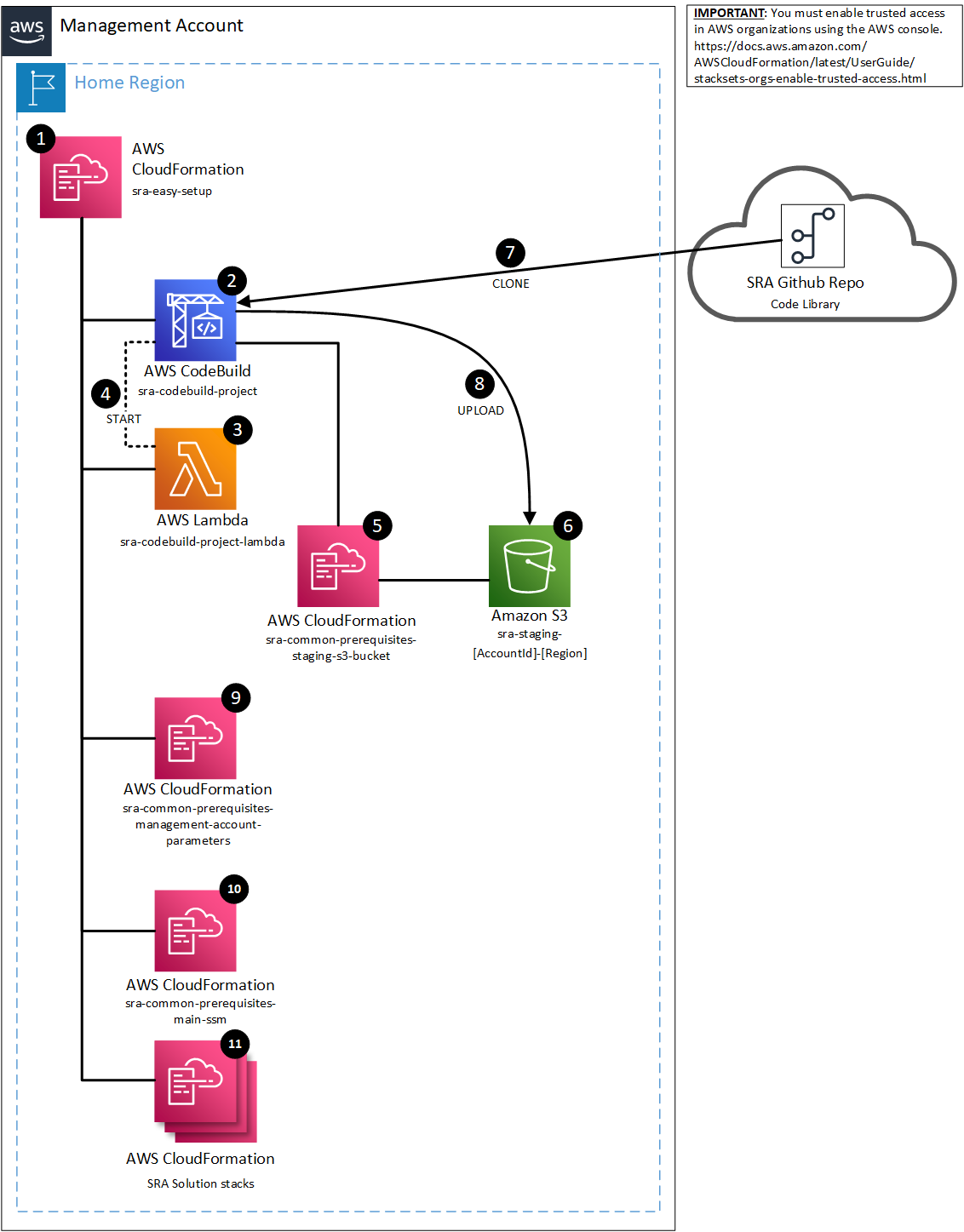
The SDCA CloudFormation template performs all of the steps in this section automatically so that you do not have to perform them on your own. The initial preparatory steps include creating an SDCA staging bucket to then download and store the AWS SRA Easy Setup in. At this point, the SDCA CloudFormation template will setup AWS Config in the management account, AWS Security Hub into the AWS Organization, and also Amazon GuardDuty into the AWS Organization. Please refer to the AWS SRA Easy setup for more details at AWS SRA Easy Setup
For the this deployment to work, you must enabled trusted access with AWS Organizations.
- Please follow the AWS CloudFormation instruction documentation to learn how to do this.
- The process to implement security services as a part of the SDCA begins with downloading the
sdca-setup.yamlcloudformation template from the SDCA code repository. Then, follow the instructions for deployment via the AWS console. - IMPORTANT: Trusted Access with AWS Organizations for StackSets must be manually enabled first.
Download the sdca-setup.yaml template by either navigating to it in the AWS SDCA code repository, or by using the example download commands in this section.
curl -LJO https://raw.githubusercontent.com/aws-samples/security-driven-cloud-acceleration/main/CloudFormation/templates/sdca-setup.yamlDeployment using the AWS console requires the template to be downloaded first (see above).
In your AWS management account, navigate to the CloudFormation service console.
In the CloudFormation service console, navigate to the stacks area.
In the stacks area, create a stack, and then select the "Upload a template file" option. Click on "Next", then follow the process to deploy the stack. Be sure to specify the appropriate parameters for the template as needed.
- IMPORTANT: If
AWS Organizationsis being used without AWS Control Tower, you must also specify the following parameter values as you create the stack:pControlTowerasfalsepLogArchiveAccountIdas the AWS Account Id of the account designated to be theLog Archiveaccount.pSecurityAccountIdas the AWS Account Id of the account designated to be theSecurity Toolingaccount.pGovernedRegionsas a list of AWS regions separated by commas
Deployment using the AWS CLI requires the template to be downloaded first.
Prepare and run the aws cloudformation deploy command to launch the template. Use the example command below to do this.
- Be sure to alter the folder/path for the
sdca-setup.yamltemplate-file appropriately (replace<path to template file>) - Be sure to specify the proper parameter overrides and specify the alarm email address (
<email address>) - If
AWS Organizationsis being used without AWS Control Tower, you must also specify the following parameter values as you create the stack:pControlTowerasfalsepLogArchiveAccountIdas the AWS Account Id of the account designated to be theLog Archiveaccount.pSecurityAccountIdas the AWS Account Id of the account designated to be theSecurity Toolingaccount.pGovernedRegionsas a list of AWS regions separated by commas
aws cloudformation deploy --template-file <path to template file>/sdca-setup.yaml --stack-name sdca-setup --capabilities CAPABILITY_NAMED_IAM --parameter-overrides pSRAAlarmEmail=<email address>From within the management account:
- Delete the
sdca-setupCloudFormation stack - Delete any remaining
sdca-*andsra-*CloudWatch log groups - Delete any remaining
/sra/*SSM Parameters - Delete any remaining
sra-*IAM roles (be sure to check all other accounts for these as well) - Delete any remaining
sra-*Lambda functions - Delete any remaining
sdca-*andsra-*S3 buckets
See AWS SRA Easy Setup Architecture Details for more information.
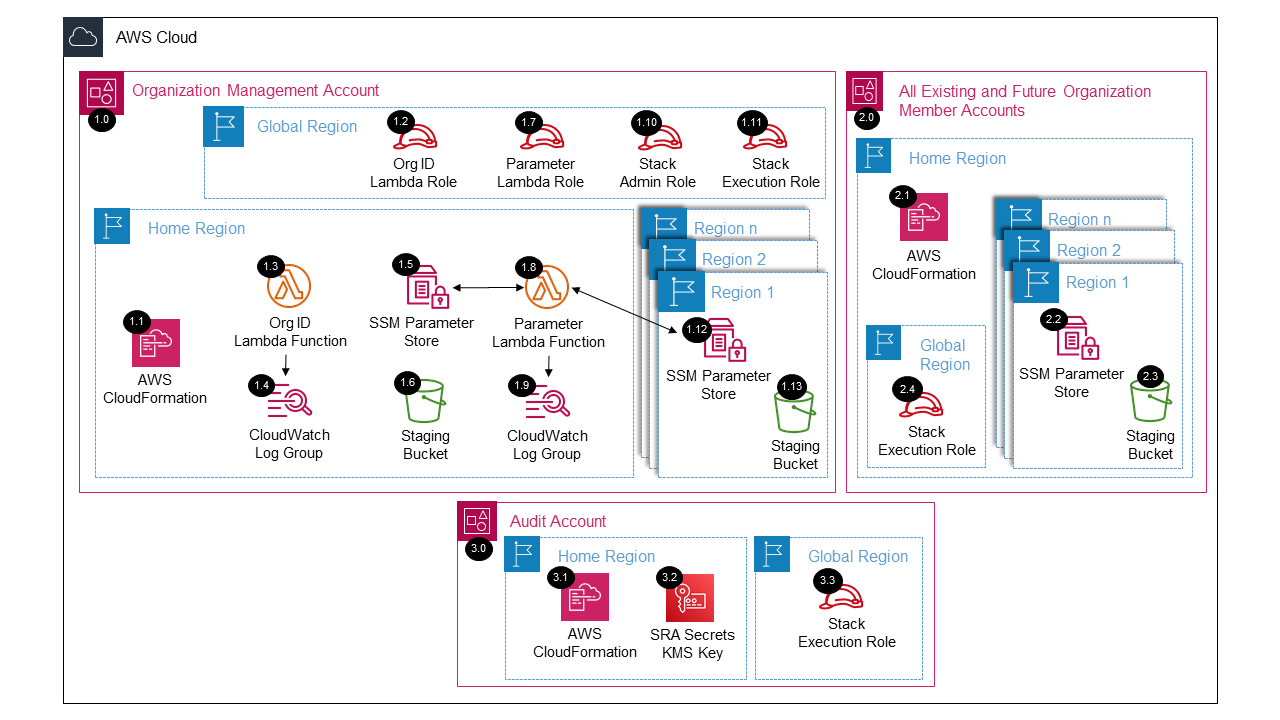
See AWS SRA Common Prerequisites Deployed Resource Details for more information.
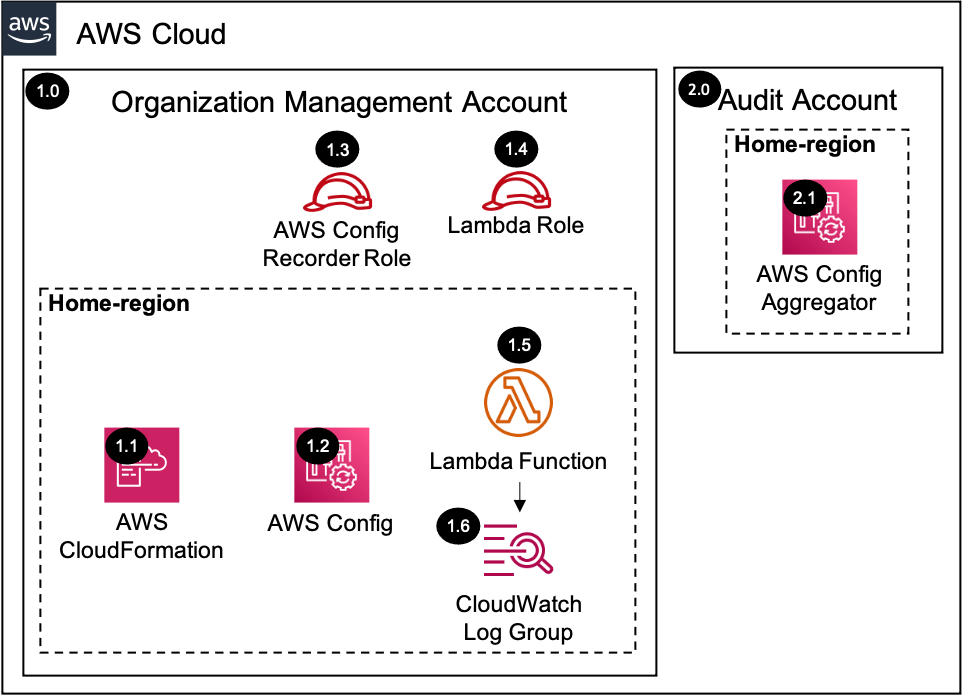
See AWS SRA Config Management Deployed Resource Details for more information.
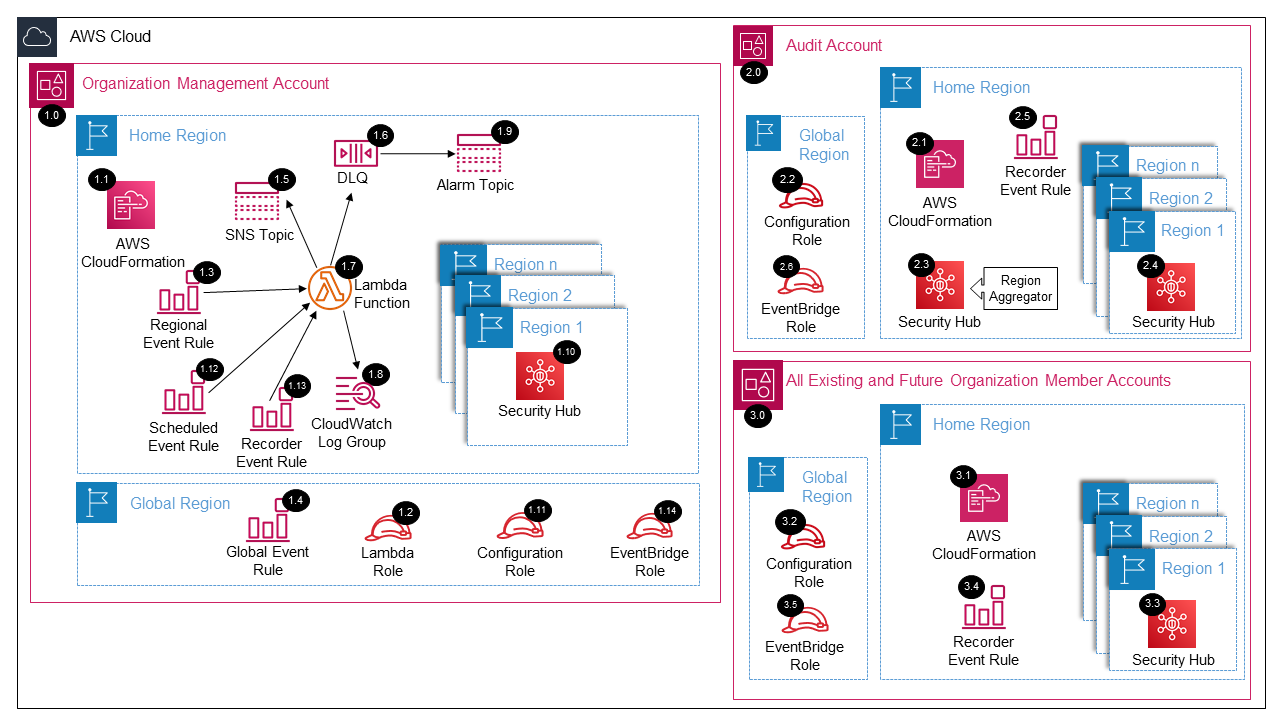
See AWS SRA Security Hub Deployed Resource Details for more information.
See AWS SRA GuardDuty Deployed Resource Details for more information.
See AWS SRA Shield Advanced Deployed Resource Details for more information.