Welcome to the 403 and 401 Bypass Techniques and Bug Bounty Tips repository! This repo is a collection of methods and strategies to bypass 403 and 401 HTTP response codes, along with various tips and tricks for bug bounty hunting. If you're passionate about finding vulnerabilities and improving security, this is the right place for you!
This repository includes a wordlist of payloads specifically designed for bypassing 403 and 401 restrictions. You can access the payloads at the following link:
-
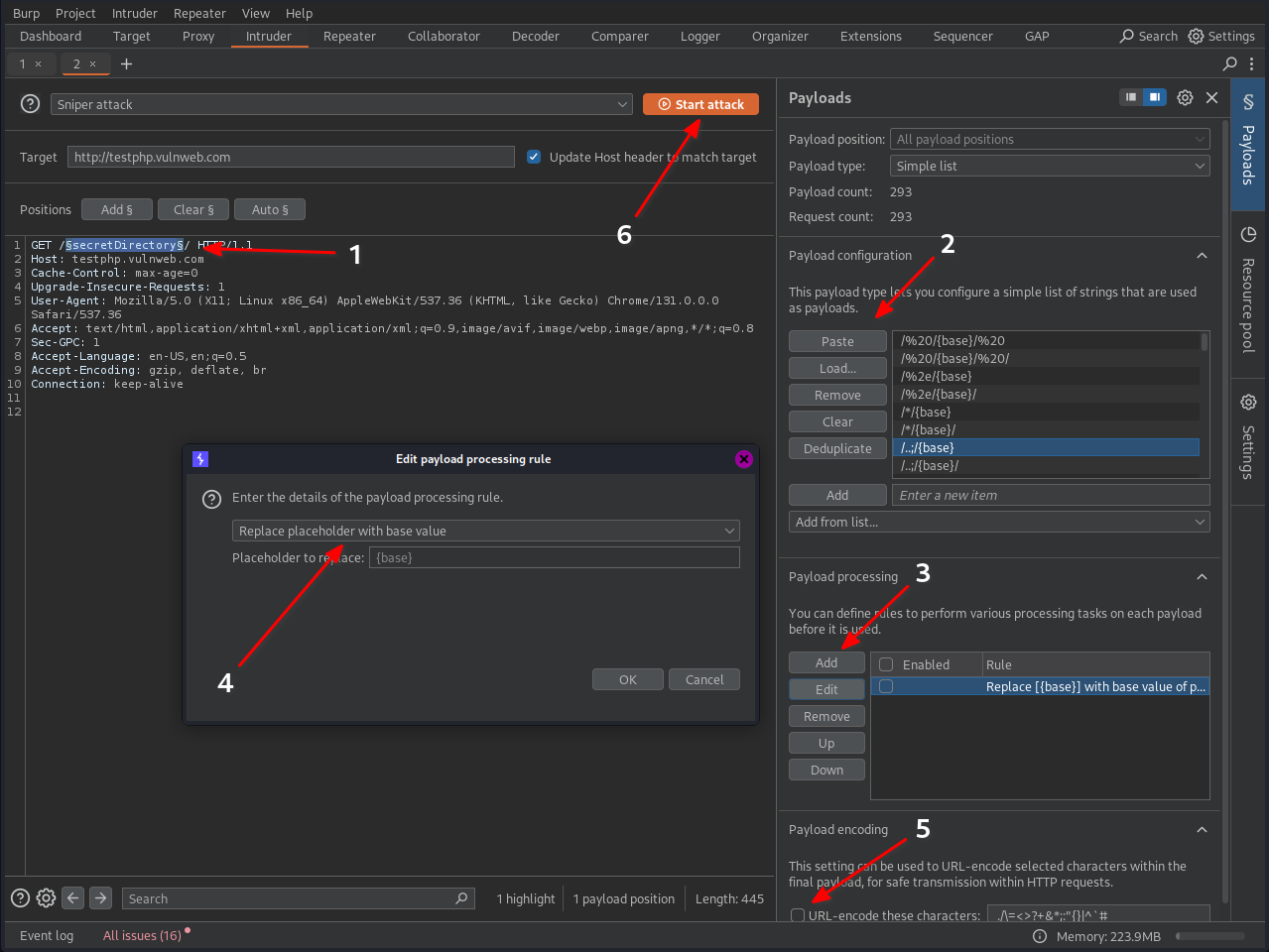
Set Up Burp Suite Intruder:
- Open Burp Suite and navigate to the Intruder tab.
- Send your request to Intruder by right-clicking on it in the Proxy tab and selecting Send to Intruder.
- Configure the Intruder positions by selecting the directory or path you want to bypass.
-
Load the Payloads:
- Copy the payloads from the provided wordlist.
- Paste the payloads into the Payload Options input field in the Intruder tab.
-
Payload Processing:
- Below the Payload Options section, locate the Payload Processing tool.
- Click the Add button to open a new window.
- Select the rule Replace String.
- Replace the placeholder
{base}with the base value you want to use for bypassing.
-
Disable URL Encoding:
- Uncheck the option URL-encode these characters to ensure the payloads are not altered.
-
Start the Attack:
- Automation is Key: Use tools like Burp Suite, Nmap, and custom scripts to automate repetitive tasks.
- Understand the Application: Spend time understanding how the target application works to uncover hidden vulnerabilities.
- Think Outside the Box: Be creative and try unconventional methods to find flaws.
- Header Injection: Test for bypasses by adding headers like
X-Original-URL,X-Rewrite-URL, orX-Forwarded-For. - Method Tampering: Try HTTP methods like
HEAD,OPTIONS, orPUTto bypass restrictions.
- If you want to support my work, feel free to DM me on Twitter at 0xSabir or contact me on WhatsApp at +923170975428. Your support means a lot and helps me continue sharing useful content!
Contributions are welcome! If you have new techniques, tips, or wordlists to share, feel free to open a pull request or submit an issue.
This repository is for educational purposes only. Use these techniques responsibly and only on systems you have explicit permission to test.
Happy bug hunting! 🐞