| Python | Linux | OSX |
|---|---|---|
| 3.7 | ||
| 3.8 | ||
| 3.9 | ||
| 3.10 | ||
| 3.11 |
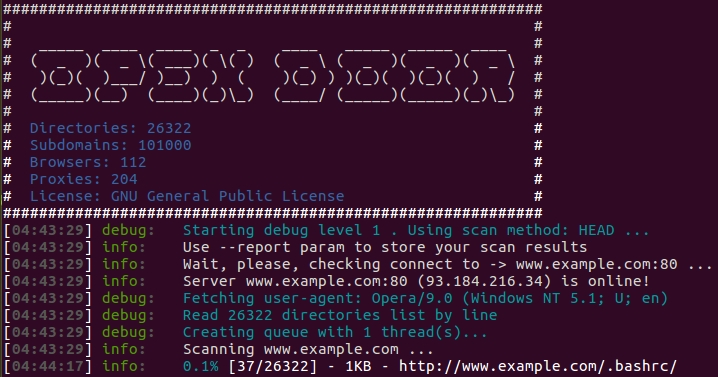
OpenDoor OWASP is console multifunctional website's scanner. This application finds all possible ways to login, index of/ directories, web shells, restricted access points, subdomains, hidden data and large backups. The scanning is performed by the built-in dictionary and external dictionaries as well. Anonymity and speed are provided by means of using proxy servers. Software is written for informational purposes and is open source product under the GPL license.
- Current 4.2.0 (29.07.2023)
- Directories: 83012
- Subdomains: 255260
Changelog (last changes)
- Fixed:
--sniff skipempty,skipsizes=NUM:NUM...moved pages to ignore in reports instead of just skipping - Fixed: invalid response statuses received because of invalid headers were passed
- Fixed: --accept-cookie param. Now it is working correctly if the server provided Cookies for surfing
- Optimized
directories_countandsubdomains_countoperation to reduce RAM usage. - Removed:
-262directories from internal wordlist because of trash - Edit Keep-Alive connection type moved to a separate parameter
--keep-alive - Optimized internal wordlist directories.txt list (sort, removed trash lines)
Testing of the software on the live commercial systems and organizations is prohibited!
- ✅ directories scanner
- ✅ subdomains scanner
- ✅ multithreading control
- ✅ scan's reports
- ✅ HTTP(S) (PORT) support
- ✅ Keep-alive long pooling
- ✅ Invalid certificates scan
- ✅ HTTP(S)/SOCKS proxies
- ✅ dynamic request header
- ✅ custom wordlists prefixes
- ✅ custom wordlists, proxies, ignore lists
- ✅ debug levels (1-3)
- ✅ extensions filter
- ✅ custom reports directory
- ✅ custom config wizard (use random techniques)
- ✅ analyze techniques:
- detect redirects
- detect index of/ Apache
- detect large files
- skip 200 OK redirects
- skip empty pages
- heuristic detect invalid pages
- blank success page filter
- certificate required pages
- ✅ randomization techniques:
- random user-agent per request
- random proxy per request
- wordlists shuffling
- wordlists filters
curl https://bootstrap.pypa.io/get-pip.py -o get-pip.py
git clone https://github.com/stanislav-web/OpenDoor.git
cd OpenDoor/
pip3 install -r requirements.txt
chmod +x opendoor.py
python3 opendoor.py --host http://www.example.com
git clone https://github.com/stanislav-web/OpenDoor.git
cd OpenDoor/
python3 setup.py build && python3 setup.py install
opendoor --host http://www.example.com
python3 opendoor.py --update
opendoor --update
usage: opendoor.py [-h] [--host HOST] [-p PORT] [-m METHOD] [-t THREADS]
[-d DELAY] [--timeout TIMEOUT] [-r RETRIES]
[--accept-cookies] [--debug DEBUG] [--tor]
[--torlist TORLIST] [--proxy PROXY] [-s SCAN] [-w WORDLIST]
[--reports REPORTS] [--reports-dir REPORTS_DIR]
[--random-agent] [--random-list] [--prefix PREFIX]
[-e EXTENSIONS] [-i IGNORE_EXTENSIONS] [--sniff SNIFF]
[--update] [--version] [--examples] [--docs]
[--wizard [WIZARD]]
optional arguments:
-h, --help show this help message and exit
required named options:
--host HOST Target host (ip); --host http://example.com
Application tools:
--update Update from CVS
--version Get current version
--examples Examples of usage
--docs Read documentation
--wizard [WIZARD] Run wizard scanner from your config
Debug tools:
--debug DEBUG Debug level -1 (silent), 1 - 3
Reports tools:
--reports REPORTS Scan reports (json,std,txt,html)
--reports-dir REPORTS_DIR
Path to custom reports dir
Request tools:
-p PORT, --port PORT Custom port (Default 80)
-m METHOD, --method METHOD
Request method (use HEAD as default)
-d DELAY, --delay DELAY
Delay between requests threading
--timeout TIMEOUT Request timeout (30 sec default)
-r RETRIES, --retries RETRIES
Max retries to reconnect (default 3)
--keep-alive Use keep-alive connection
--accept-cookies Accept and route cookies from responses
--tor Using built-in proxylist
--torlist TORLIST Path to custom proxylist
--proxy PROXY Custom permanent proxy server
--random-agent Randomize user-agent per request
Sniff tools:
--sniff SNIFF Response sniff plugins
(indexof,collation,file,skipempty,skipsize=INT)
Stream tools:
-t THREADS, --threads THREADS
Allowed threads
Wordlist tools:
-s SCAN, --scan SCAN Scan type scan=directories or scan=subdomains
-w WORDLIST, --wordlist WORDLIST
Path to custom wordlist
--random-list Shuffle scan list
--prefix PREFIX Append path prefix to scan host
-e EXTENSIONS, --extensions EXTENSIONS
Force use selected extensions for scan session -e
php,json e.g
-i IGNORE_EXTENSIONS, --ignore-extensions IGNORE_EXTENSIONS
Ignore extensions for scan session -i aspx,jsp e.g
- @stanislav-web https://github.com/stanislav-web (Developer)
pip3 install -r requirements-dev.txt
python setup.py test
If you like to contribute to the development of the project, in that case, pull requests are open for you. Also, you can suggest an ideas and create a task in my track list